Credential harvesting phishing attacks have become more sophisticated. The GreatHorn Threat Intelligence Team found one recent example of a phishing email that attempts to harvest credentials harvesting while impersonating American Express. This attack not only looks real but bypasses many email security solutions. Additionally, there is not only the impersonation of the American Express brand, but also on Cole Haan – another well-known brand.
In this scenario, the attacker targets American Express users with an authentic looking email. This email is a request to review their account, stating it has been flagged due to billing and payment issues resulting in abuse and terms of use issues. It suggests that the user has done something such as abuse the usage of the account or not done something such as missing a monthly payment. This type of urgency to act is intentional by the attacker, with users falling victim at a higher rate.
Within the design of the email, the attackers have pulled some legitimate branding from American Express’ website, including brand colors and the format of the “account ending” section at the top. In the footer section of this email, the attackers have copied authentic verbiage from legitimate American Express emails, also hyperlinking to a page on the American Express website for their security center.
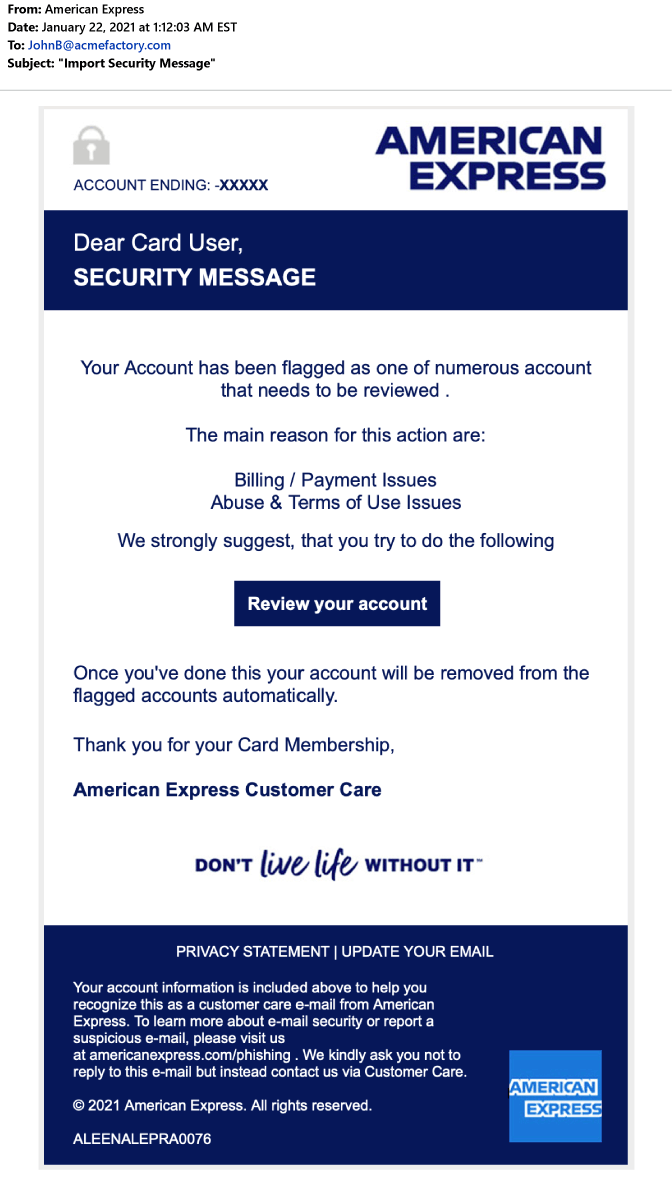
However, while the overall email looks legitimate, there are some things to notice. At the top of the email, it merely uses generic language such as “Dear card user” versus the standard inclusion of the card member’s name. Also, the lack of plural usage in the language of the email and the subject line, which is marked as “Import Security Message”, also should be a red flag to users.
Upon clicking the link to “review your account” the user is taking to an authentic-looking login page for American Express. This page prompts the user to type in their username and password, as well as select the account they would like to view. Once the account information has been submitted, the cybercriminal has harvested those credentials for the account to then begin fraudulent transactions. In addition, if other users who are on the same account, their personal information would also be exposed to the attacker.
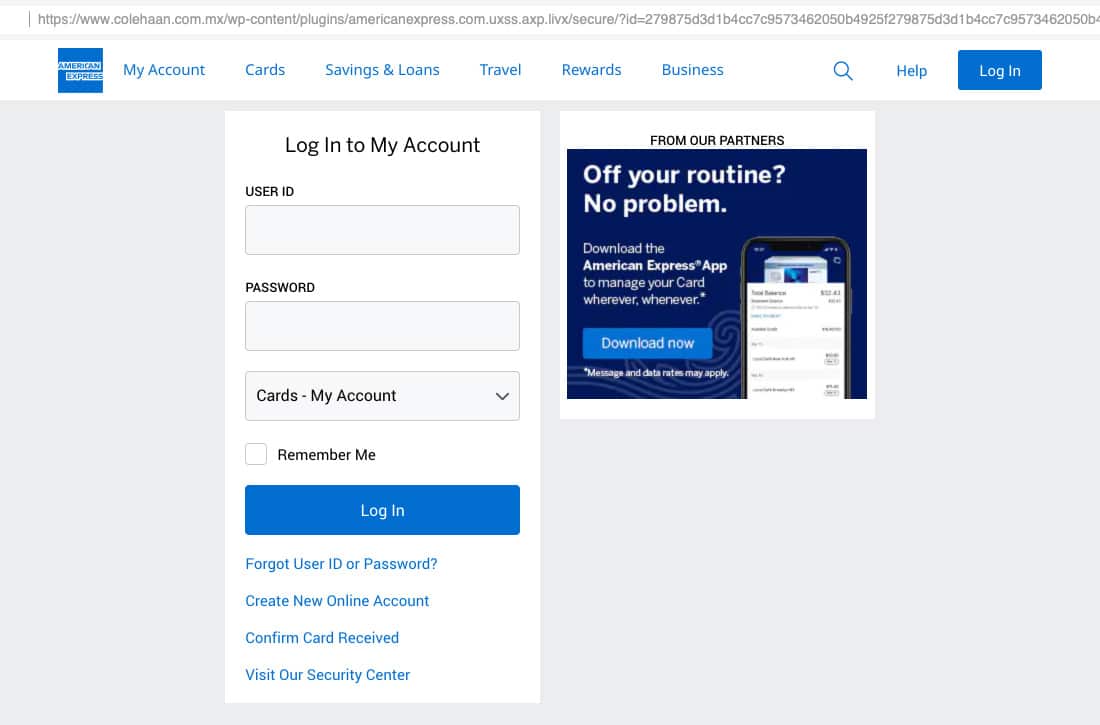
It is critical for organizations to help employees who have access to bank account information and corporate credit card information to be discerning when online and to take precautions when giving out this type of sensitive information. Understanding the risks that comes along with it can help ensure making transactions are more secure.
With cybercriminals developing more tactics to bypass email security solutions, users are falling prey to these types of attacks more often. In fact, GreatHorn’s 2020 End User Phishing Report found that employees were able to accurately identify whether an email was a phish or authentic in only 5 out of 10 examples.
More than ever, organizations today require a partner in email security that can detect and assess email risks, majorly at the start of a potential attack. Being able to analyze URLs and understand historic communication patterns is critical to adding contact to your email security. GreatHorn’s Advanced Threat Detection helps to remediate these threats faster, reducing the time to detect and respond.





