In 2015, email security was a decades-old market, with well-established behemoths that dominated the industry but lacked innovative solutions that ultimately failed to protect corporate email from modern email attacks. Gartner published what turned out to be its final Secure Email Gateway Magic Quadrant that year, which it has subsequently retired due to what they call a “highly saturated and very mature” market. It was into this “low differentiation” market that GreatHorn was founded, determined to drive innovation and establish a higher bar for protection against advanced email threats.
Despite the arguably premature “retirement” of the Magic Quadrant, the email security market has never been hotter or needed more. Just last week, at Gartner’s annual Security & Risk Management Summit, business email compromise was listed as one of the “Top 10 Security Projects for 2019” and analyst Mario de Boer devoted a session to “Mitigating Phishes that Your Email Gateway Misses.”
The business email compromise problem isn’t theoretical.
According to the FBI’s 2018 Internet Crime Report, financial losses from business email compromise have increased by 427% to $1.3 billion since 2015. Such statistics represent the direct financial loss—i.e. losses due to wire transfers and invoice payments—and do not reflect financial losses due to confidential information loss, brand damage, or regulatory fines.
While other aspects of email security—malware and traditional malicious link detection have indeed become commoditized as Gartner claimed, we anticipated that advanced spear phishing was both a problem that existing platforms would have difficulty solving, and also that it would become the critical driver for email security as companies moved into the cloud.
We also recognized that the mass enterprise migration to cloud email afforded an opportunity to rethink how the industry has historically approached email security (the gateway model) and weave it into a comprehensive and continuous strategy that would improve over time.
In June, more than $450 million in new investments has been poured into companies (including GreatHorn—we announced our latest round of financing today) that address aspects of this problem—from computer-based training to authentication-based detection to the vague and ever-present machine-learning. And while there is a lot of worthy innovation out there, we believe GreatHorn stands ahead of the competition in providing large enterprises comprehensive protection against email-borne threats.
What makes GreatHorn’s approach to email security unique?
Advanced email and social engineering attacks exploit three core weaknesses:
- Traditional, binary systems are ineffective at catching advanced threats like executive and brand impersonations. Such emails mimic “regular” mail so closely that to detect them, systems would also block large amounts of “regular” mail.
- Many, if not most, organizations treat email security as distinct point-in-time solutions rather than a living, integrated program. Today’s sophisticated threats require a holistic approach that balances business processes, people, and technology rather than an over-reliance on the perimeter-based blocking technology combined with disconnected and often ineffective security training programs.
- People are an underutilized asset. Given the appropriate context at the right time, people can be a highly effective defense layer.
We believe fundamentally that the insidiousness of today’s threat landscape require a reimagining of how technology addresses email security—blocking more threats at the platform level, yes, but also identifying additional points of protection at the user level, and better tools at the admin level to further reduce risk and mitigate damage.
With these issues in mind, we have developed a platform that not only dispositions obviously malicious and highly suspicious emails based on an organization’s risk tolerance (i.e. everything you expect any email security product to do—we call it “Automated Protection”), but that also provides two additional layers of robust defense: “User Engagement” and “Integrated Incident Response” that address the problems we outline above.
Using people-centric security concepts, our User Engagement layer capitalizes on the strength of your employee base when they are provided with relevant, accessible, and explicit context about why an email is suspicious at the moment that an employee might interact with it.
Equally important is the need to provide security and risk teams with a better alternative to the antiquated, cumbersome, or jury-rigged tools and scripts they’ve traditionally used to identify, isolate, and eliminate identified risks.
However, no new email security platform could hope to succeed without providing a better threat detection engine for identifying the very threats that bypass other products. By combining dynamic threat intelligence with personal and organization-specific data (deep relationship analytics and personal communication patterns for example), GreatHorn’s adaptive threat detection engine can more accurately assess risk, continuously analyzing emails at every point of risk to identify targeted phishing and fast-moving threats.
Fundamental to making this multi-layered approach work is a cloud-native architecture that provides two critical benefits that cannot be achieved by a traditional gateway (even if it’s hosted in the cloud):
- Greater visibility: For example across intra-domain email, already delivered but newly weaponized email, and even rapidly moving, zero-day threats spreading across our client base.
- More nuanced control: Unlike one-size-fits-all email security, we automatically learn, adjust, and improve our protection in a way that’s unique to your organization while giving you the ability to tune actions and policies to meet your risk profile and tolerance.
Why is a layered approach email security important?
In 2018, Gartner estimates that $490 million was spent on computer-based training software. And yet according Verizon’s annual Data Breach Investigations Report, there was only a one percent decrease in click-through rates in simulated phishing exercises.
Meanwhile, in our annual Email Security Benchmark, which will be released in a just a couple of weeks, we’ve learned that nearly 30 percent of organizations have experienced some sort of breach due to an email-borne threat in the past six months, and more than a third need to remediate email-based attacks on a weekly basis.
As an industry, we have spent billions of dollars and more than two decades trying to solve the problem of email-borne threats. It’s time for a different approach.
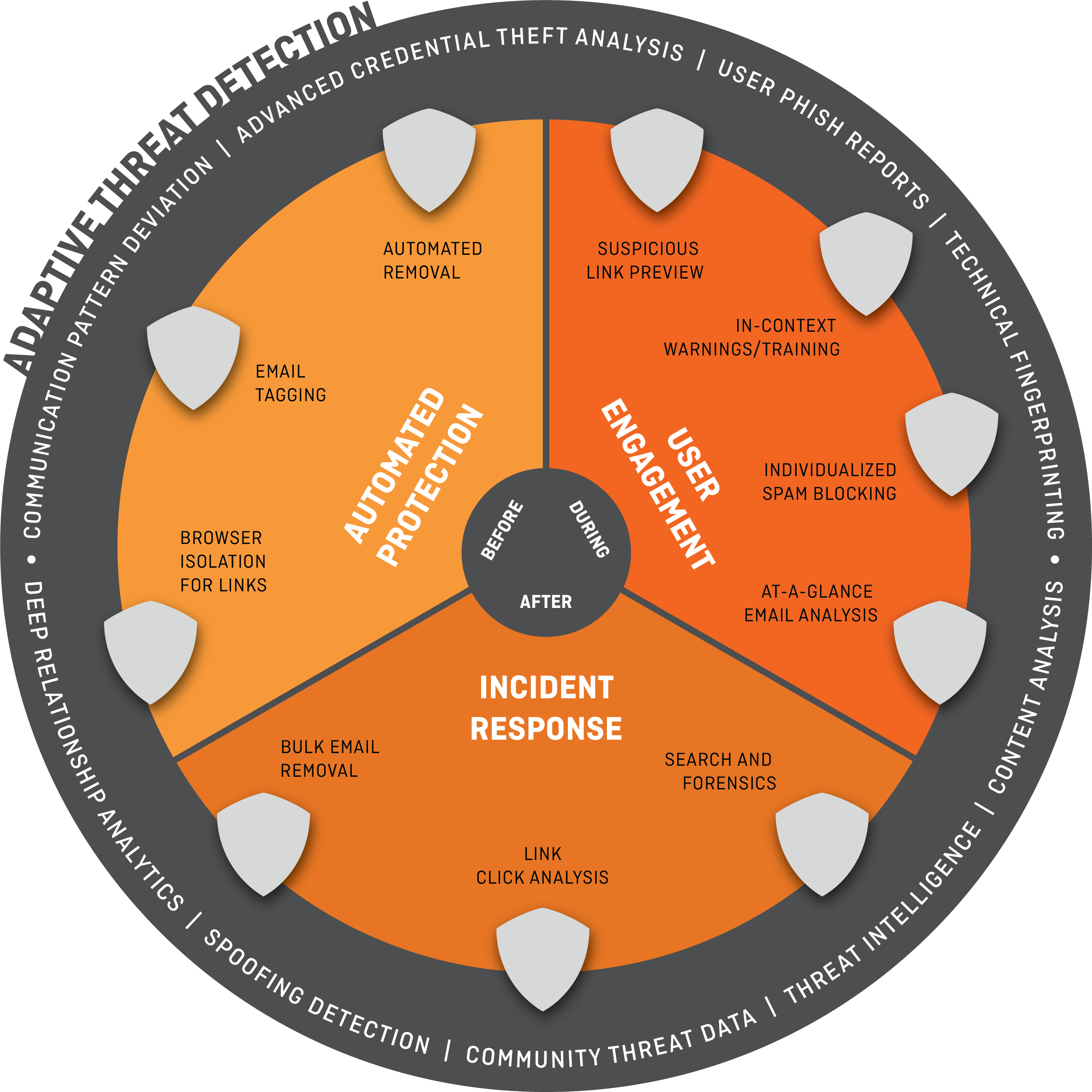
GreatHorn’s Layered Approach
Since its founding, GreatHorn has grown into a comprehensive platform that protects organizations at each point of risk—before it reaches the user, when a user might engage, and after a threat has been identified. You can read more about what we do and how we do it here.
We’re excited about putting our latest round of financing to good use in the coming months. Stay tuned!





