Over the past few months, remote work has become more common across the board. Cybercriminals are now using sophisticated and complex phishing techniques to target people and organizations as online business tools and applications become the cornerstone to maintaining productivity.
According to GreatHorn’s 2020 End User Phishing Report, when it came to emails around coworking platforms and business-related applications, 59% identified them as phish when they were authentic emails. This statistic alone shows that organization require more training to improve productivity.
Given that most of us are working online, our reliance on digital communication provides cybercriminals with more opportunities to target us. To drive awareness and improve cybercrime literacy, we’ll examine a new emerging phishing attack that has been doing rounds recently.
This specific phishing attack impersonates Adobe, beginning with an authentic-looking email from a colleague or business partner telling the user they have received files through the Adobe Cloud. Once users click on the link, they are taken to a website masquerading as a document, or a spreadsheet, blurred out with a pop-up box asking users to fill in their user id and password.
Let’s decipher the threat across each step of this multi-layered attack:
Step #1: The Email
The user will receive an email appearing as an autogenerated email seemingly from Adobe, requesting them to view the new files on Adobe Cloud. Though Adobe does not have a product named “Adobe Cloud”, the appearance of the email, including authentic looking brand logos, gives this impersonation the credibility required to get users to act.
Adobe has a suite solution which is called the Adobe Creative Cloud and features tools and software for graphic designers and content creators. Adobe’s Creative Cloud is not intended to be used as a document sharing platform.
The email also features a URL which falsely looks like an authentic Adobe email domain. However, on close inspection, you’ll find that the email URL does not contain an Adobe domain name. Most times, it is a generic email domain like Gmail or Outlook.
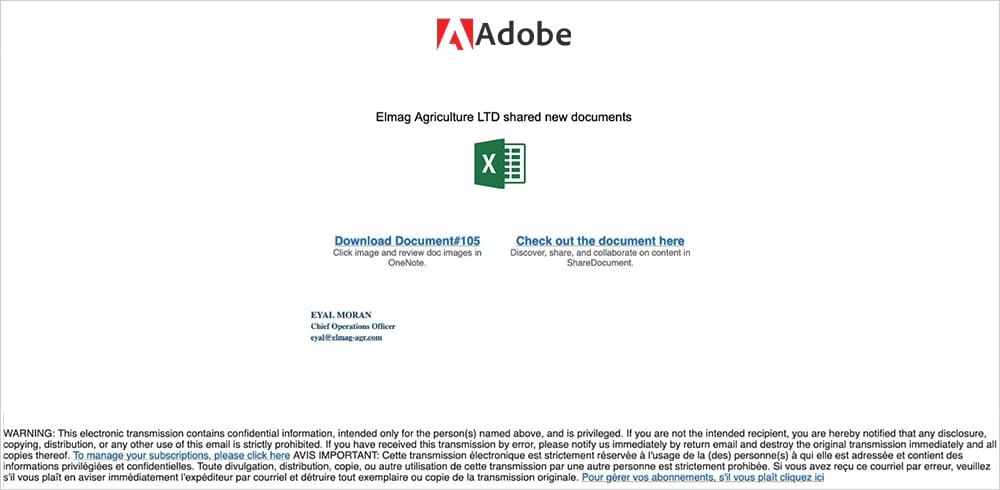
The phishing attack features a download link for users to “Access Your Secured Document” and takes the user to an external site.
Step #2: Access the Document
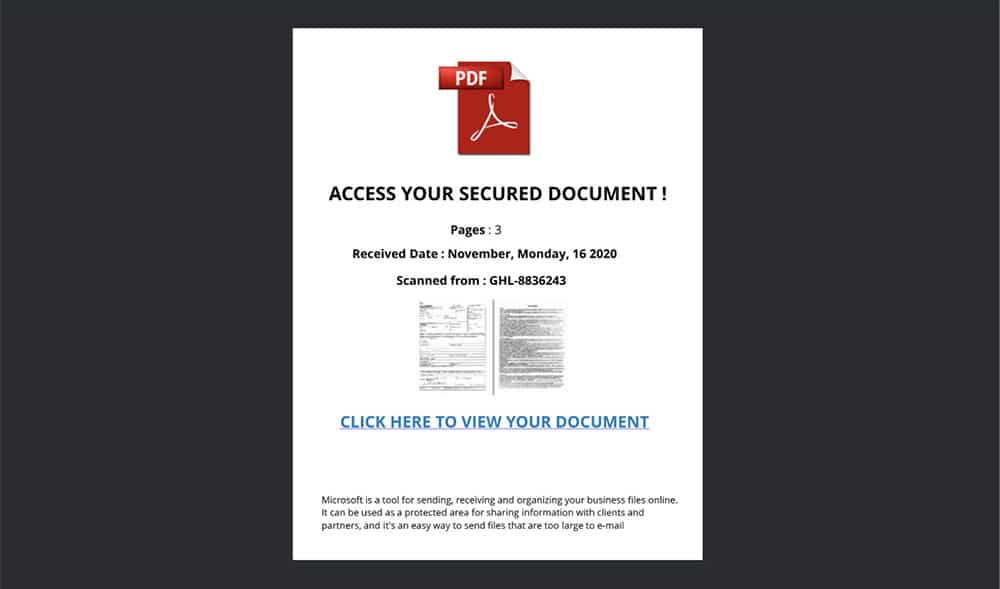
Once users click on the link within the email, they’re taken to a page that shows a blurred preview of the supposed file. The page will typically feature two links for either downloading or viewing the file. Once users click on any of the options, they are directed to a login page that asks them to login with Microsoft Office 365 ID, Google ID, or an email and password combination.
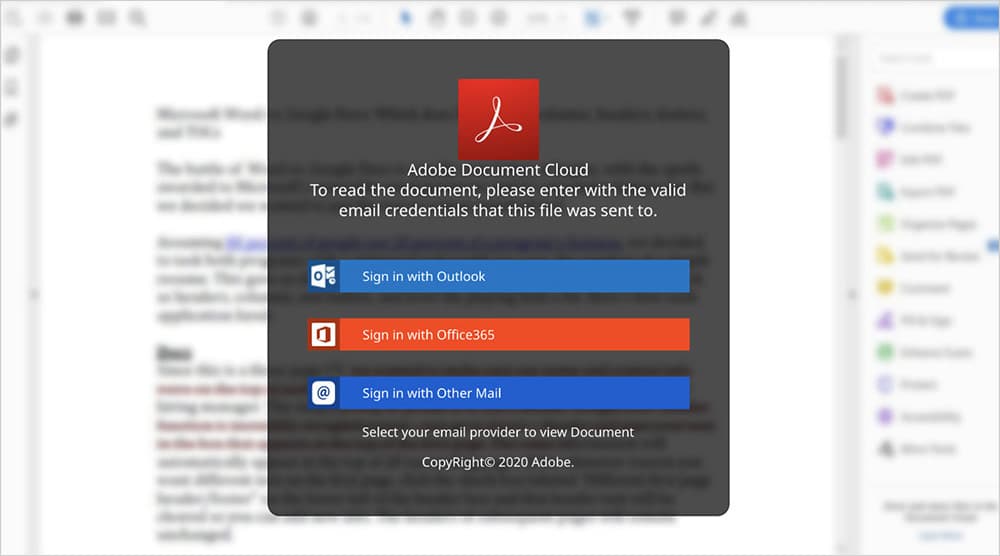
Step #3: Credential Harvesting and Account Takeover
In the last step of the phishing attack, users are prompted to sign-in to Adobe to view their files. Once they provide the cybercriminals with their User ID and password combination through either a sign in with Microsoft, Google or “other mail”, users are taken to the Google homepage. And, the cybercriminals have, by this time, successfully obtained access to the victim’s email credentials.
Once the cybercriminals have the users’ login credentials, they will be able to use the account to send emails, impersonating that user. Attackers can also perform Account Takeovers. They will also use your account to gain access to any file storing or file sharing apps connected with your account to steal your personal information and misuse your financial data.
Because of the sophistication used within this multi-pronged attack, it is important for IT administrators to develop policies within their email security solution that can detect advanced impersonation attacks before users fall victim to the attack. And, when an email appears to be from a legitimate company, it can be hard for users to know whether it is authentic or part of an attack.
GreatHorn aims to make email safer for organizations with anti-phishing, Advanced Threat Detection and Cloud Email Security solutions. By providing a single platform that streamlines email security needs, organizations can reduce the complexity of email management.
GreatHorn is also dedicated to helping organizations keep their networks and employees safe online. Our User Education tool helps email users identify attacks in the moment of risk. By analyzing email, domain names, and hundreds of other factors, you can keep your employees safe from email attacks.




