At GreatHorn, we spend most of our time and effort on the most sophisticated email attacks that are threatening organizations and end users. We’re constantly dealing with new attacks and layering defense strategies to combat them.
In our 2021 Email Security Benchmark Report, we detail how mimicking well-known business-related applications is the most frequent tactic seen in the impersonation attempts used in phishing attacks. Sometimes, these attempts can be comical.
Not all attackers are sophisticated. In fact, sometimes the cybercriminals who are phishing for personally identifiable information (PII) or attempting to deliver malicious payloads can be downright bungling and inept.
This month, one email attack in particular caught our eye for the way it stacked one fail atop another, making it almost comically easy to distinguish as a suspicious message. Let’s run through this comedy of errors.
Phishing Phail #1: Don’t loose the bonuses!
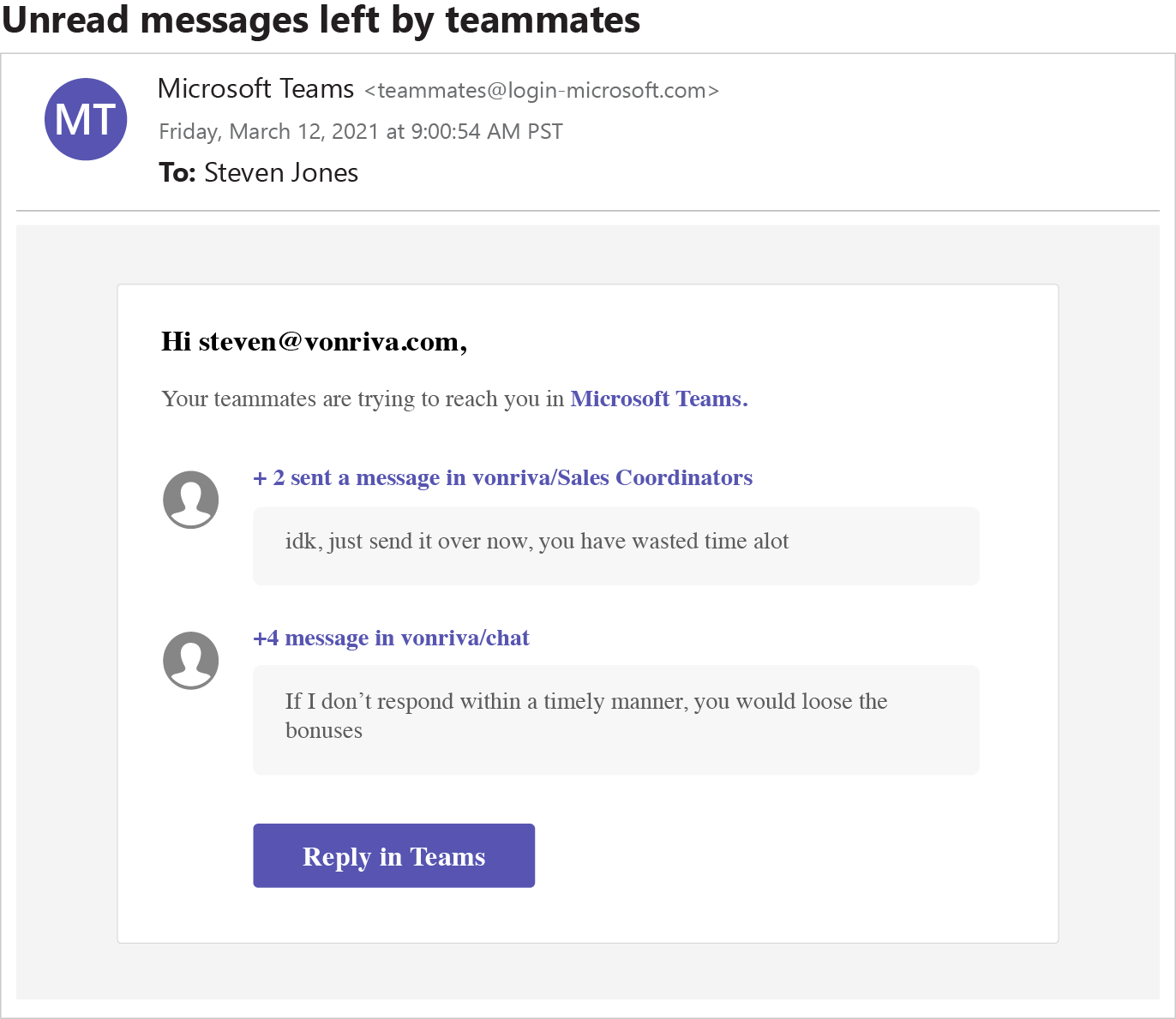
This phishing attempt tried to simulate an alert message from Microsoft Teams, notifying the user about new message activity. Of course, GreatHorn intercepted it – but even if it had gotten through, it’s hard to imagine a user falling for the attacker’s effort to induce a sense of urgency.
Even before opening the email, the ransom-letter style random letter capitalization is a giveaway. Of course, we all make typos, and sophisticated attackers sometimes use this tactic to add veracity to a message that is supposed to have come from a hurried coworker. But this message is supposed to simulate an automated alert from Microsoft. Pretty sure Microsoft QA would catch this typo before including it in their product.
![]()
In the body of the email are two angry-seeming fake Microsoft Teams messages.
- The first message urges the user to “just send it over now, you have wasted time alot.” Never mind the slightly off wording and misspelling of “a lot.” Is this kind of angry accusation normal at workplaces? At GreatHorn, a communication like this might lead to an “HR moment.”
- The second message also attempts to establish urgency, but trips and gets tangled up in words even worse: “If I don’t respond within a timely manner, you would loose the bonuses.” Loose the bonuses … Is that like “loose the hounds”?
OK, let’s say after all that, the user, flummoxed by the angry tone and preoccupied with an approaching deadline, clicks the link anyway. We tried it out in quarantine, just to see what would happen …
and sat through a long waiting period while the page redirected.
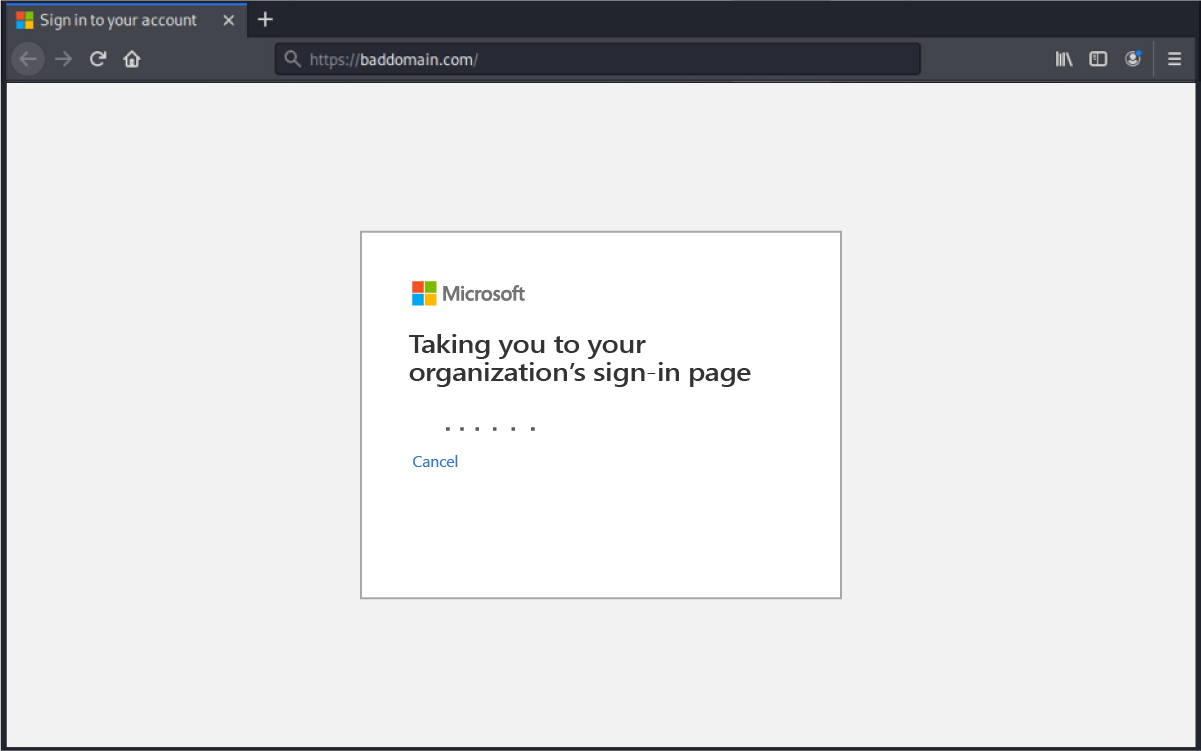
This attacker was really making us work, in order to get to the place where we could provide our PII. And after all that, the simulated “Microsoft Teams” login page is a page hosted on Google.

Phishing Phail #2: I need help moving this cash$$!
Many individuals have been arrested in the “Nigerian Prince” scams, and the emails have since become a joke that has gone mainstream (a monologue on Saturday Night Live even gave the audience a laugh in 2008). But these unsophisticated attacks still rake in over $700,000 a year! So in the same vein, we thought we’d provide another spinoff of a similar phishing phail.
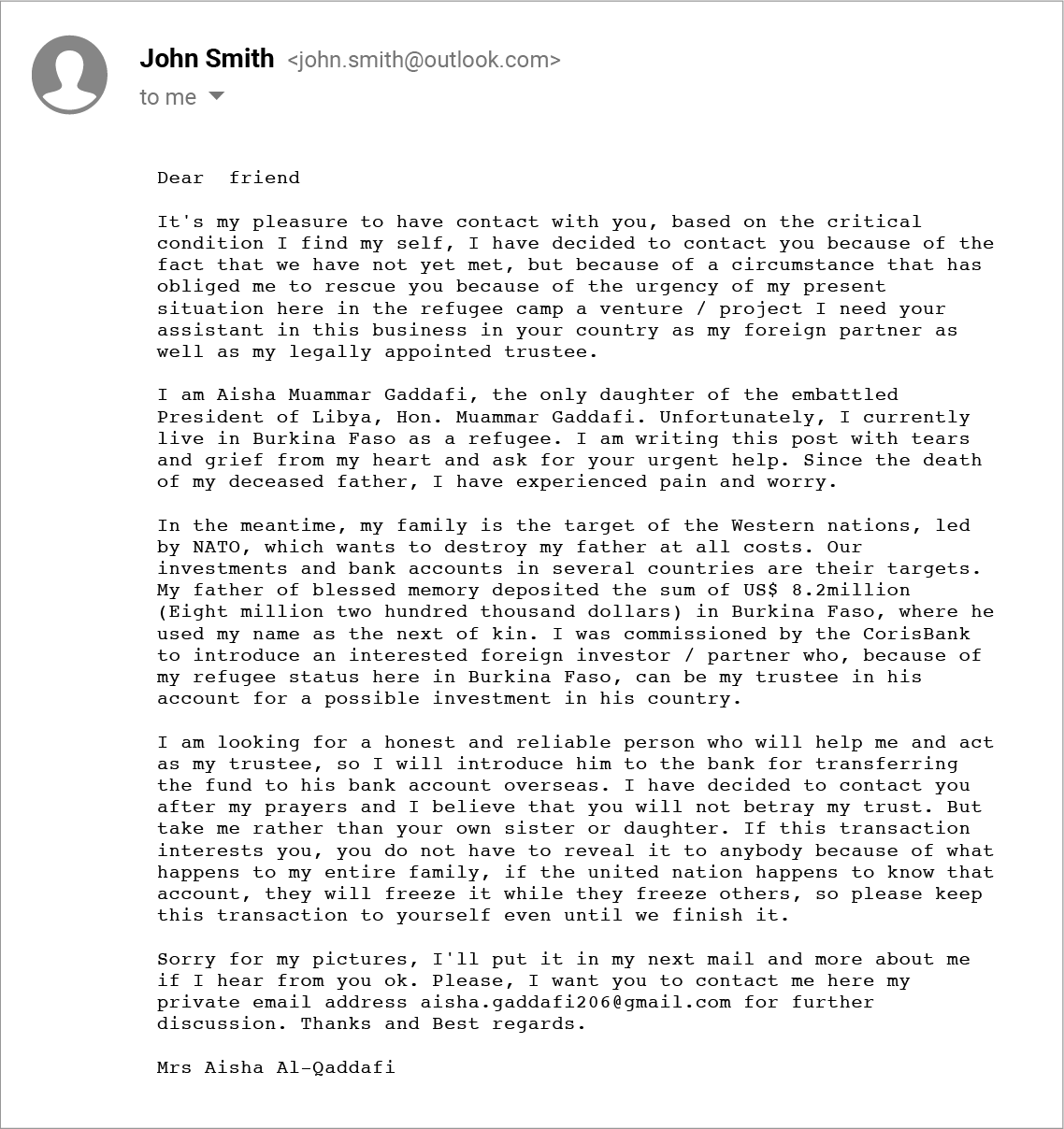
Unfortunately, this email was quarantined for us, here at GreatHorn, so we missed the opportunity to claim millions. But don’t worry, it gives us the ability to continue to bring more Phishing Phails to you!
We get to see some doozies, and IT security professionals who use GreatHorn do, too. Have a Phishing Phail that beats this one? Submit your Phishing Phails to [email protected]. And, learn more about how GreatHorn provides a layer of intelligent email security that makes sure no message, no matter how comical, ever becomes a threat.




