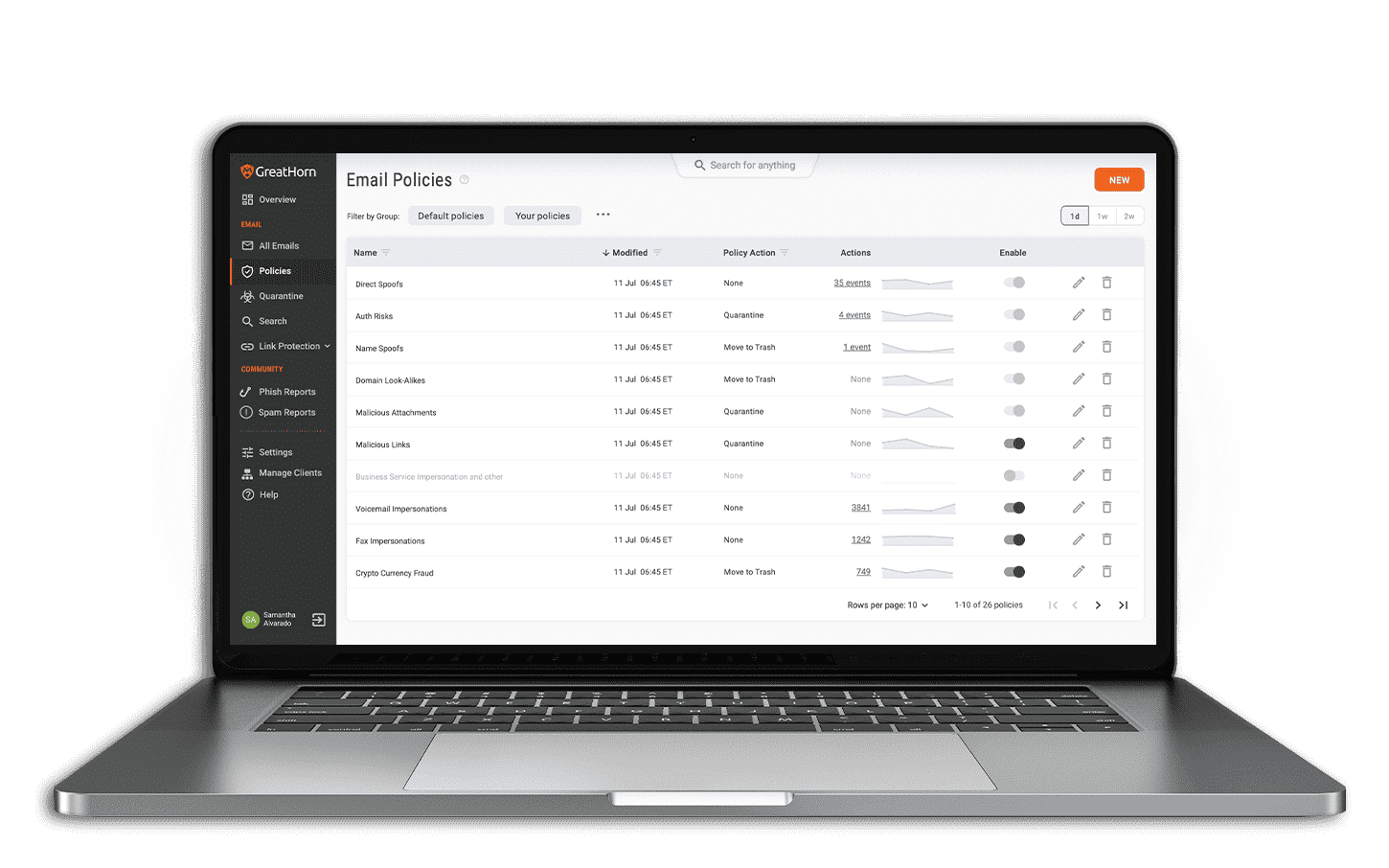
Reduce your Time to Detect and Respond To Advanced Threats
When a Phishing Attacks Hits, Every Second Matters
Every minute an incident response takes is one minute closer to a click and a potential breach. And yet today’s security professionals have to rely on time-consuming and often inaccurate scripting or a simplistic and manual search and remove process. GreatHorn’s incident response makes it easy to find and bulk remove threats from user inboxes in just seconds.
Email Removal – No Scripts Required
Automated Removal
Scans and removes any threats sitting in user mailboxes, even if a link is weaponized post-delivery.
Two-Click Bulk Removal
Integrated incident response to search and remove bulk threats in seconds.
Robust Search Interface
Identify the breadth of a given attack with robust search interface.
Get Your FREE Email Threat Assessment
Learn what advanced threats are currently getting through your existing email security and into your end users’ mailboxes.
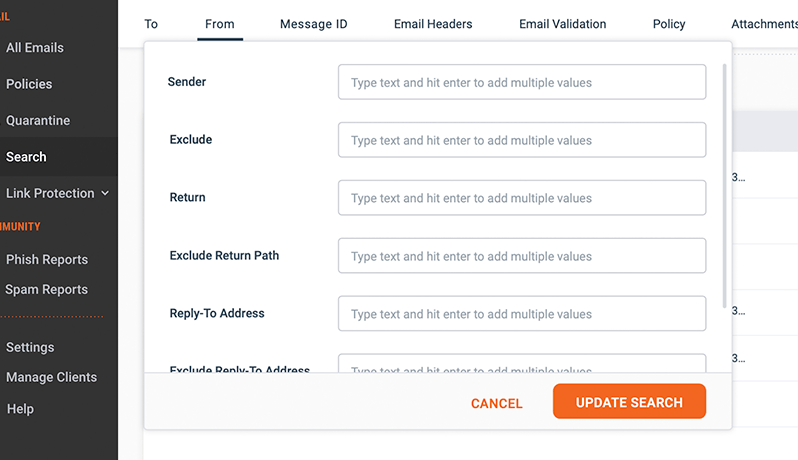
Search Beyond the Sender and Subject Line
Since sophisticated attacks can take many forms and often lack the sender and/or subject line consistency of more simplistic volumetric phishing campaigns, GreatHorn’s robust search engine enables you to search against any combination of factors from relatively simple content-based keyword searches to more technical metadata.
Make Informed Decisions When it Matters Most
GreatHorn’s Link Analysis provides additional time-of-click protection for users, and also tells you who clicked through to the destination page and when. This additional insight empowers you to make smarter decisions about the severity of your threat response, limiting the business impact to those users that are actually at risk.
Administrators have access to full-click tracking for suspicious and malicious URLs, post-delivery blocking capabilities, and enhanced detection of new threats—even those that have not yet been added to real-time blacklists or publicly available antivirus tools.
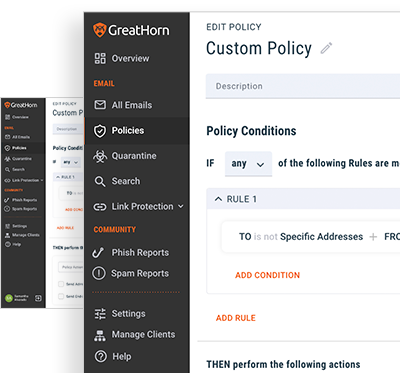
Visibility, Control, and Early Notification
Adjust how often employees are challenged based on frequency, time delay, communication pattern anomalies and more.
You can also configure actions based on authorization failures:
- Insert a warning smart banner to the recipient
- Remove the message upon send
- Alert the security team, or
- Simply log the event for later analysis.
Failed attempts populate into the GreatHorn dashboard providing context for faster incident response.

![[eBook] Things to Consider: Microsoft 365 + GreatHorn](https://www.greathorn.com/wp-content/uploads/2023/05/eBook-Microsoft-365-GreatHorn.png)
![[eBook] Things to Consider: Google Workspace + GreatHorn](https://www.greathorn.com/wp-content/uploads/2023/05/eBook-Google-WorkspaceGreatHorn.png)
![[Whitepaper] Measuring the Value of Email Security Solutions](https://www.greathorn.com/wp-content/uploads/2023/05/Whitepaper-Measuring-the-Value-of-Email-Security-Solutions.png)
![[Report] 2023 State of Email Security: Key Trends and Insights](https://www.greathorn.com/wp-content/uploads/2023/03/Report-2023-State-of-Email-Security.png)