False Positives are an Email Security Nightmare
Minimize false positives by first understanding your organization’s risk tolerance in your cloud email security environment. Then, apply layers of protection across each level of email risk.
 Learn how you can improve your response to sophisticated threats, with:
Learn how you can improve your response to sophisticated threats, with:
- Leveraging fact-based AI engine to assess risk
- Applying levels of controls for employees, to optimize quarantine
- Customizing Smart Banners to reduce quarantine requests by 75%
- Incorporating email security best practices to prevent zero-day and social engineering attacks from
Download the Whitepaper
"GreatHorn perfectly combines power and flexibility with the simplicity of an API solution."
— Director Of IT in the Services Industry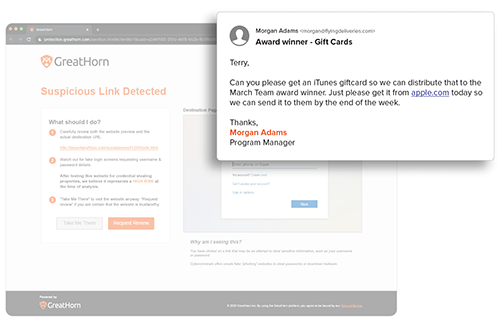
Suspicious URL Detection
URLs are analyzed using machine vision to detect any anomalous content on the destination. With GreatHorn’s Link Protection page, users are educated with a preview of the destination, the risk of credential harvesting, and steps they should take to minimize their risk.
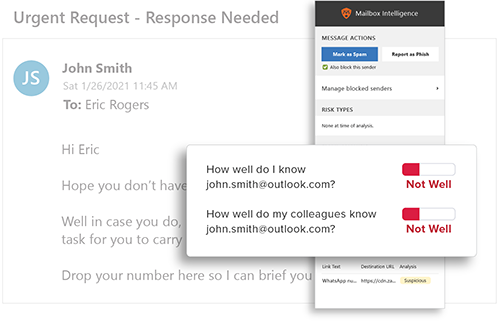
Behavioral Analytics
GreatHorn analyzes all communication patterns between senders and recipients using behavioral analytics within our AI and ML models, providing organizations with immediate detection and insight into anomalous emails.
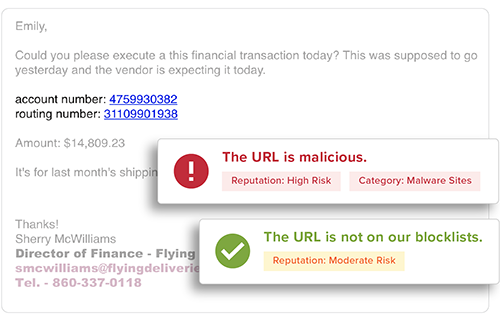
End User Education
Provide users with the context they need to help them make better decisions by applying automated and customized banners, Mailbox Intelligence, Suspicious Link pages, and more.