STOP PHISHING
WITH LAYERED CLOUD-NATIVE EMAIL SECURITY
Email Security: It’s more than just blocking & detection rates.
See How GreatHorn Can Help!
Phishing is the #1 Threat Vector Used in Breaches
And they aren’t going away
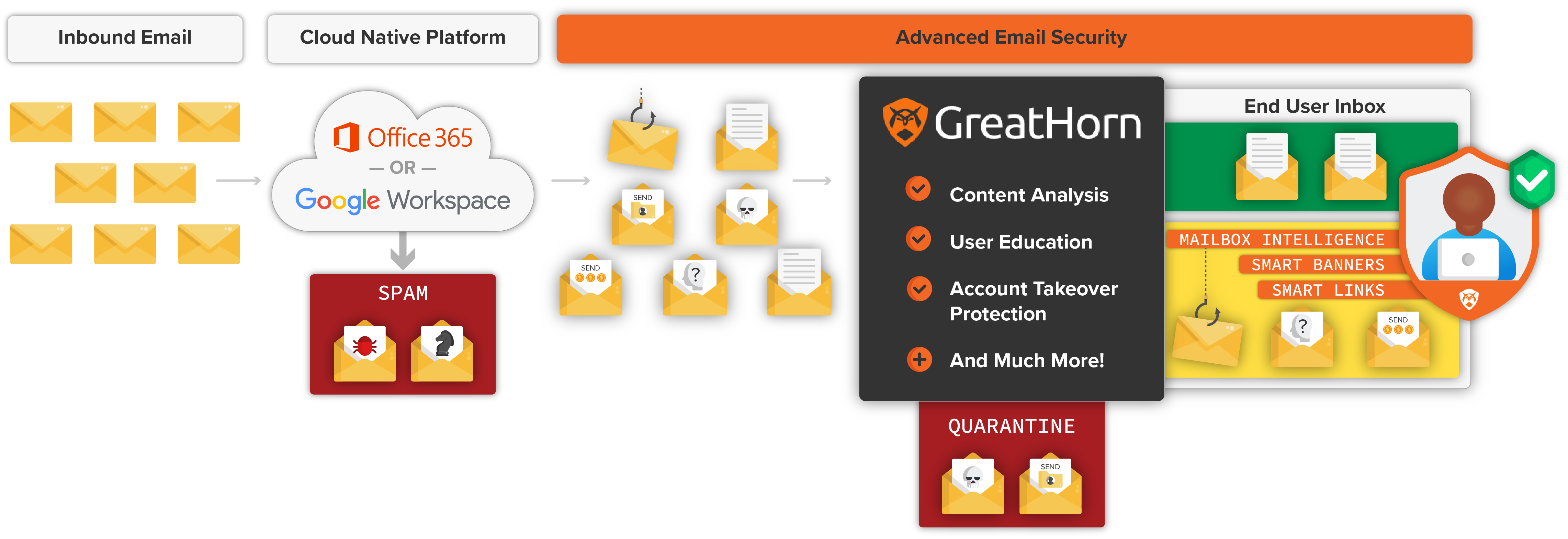
GreatHorn is an integrated, cloud-native email security platform that layers sophisticated phishing detection with user engagement and incident response for improved efficiency and outcome.
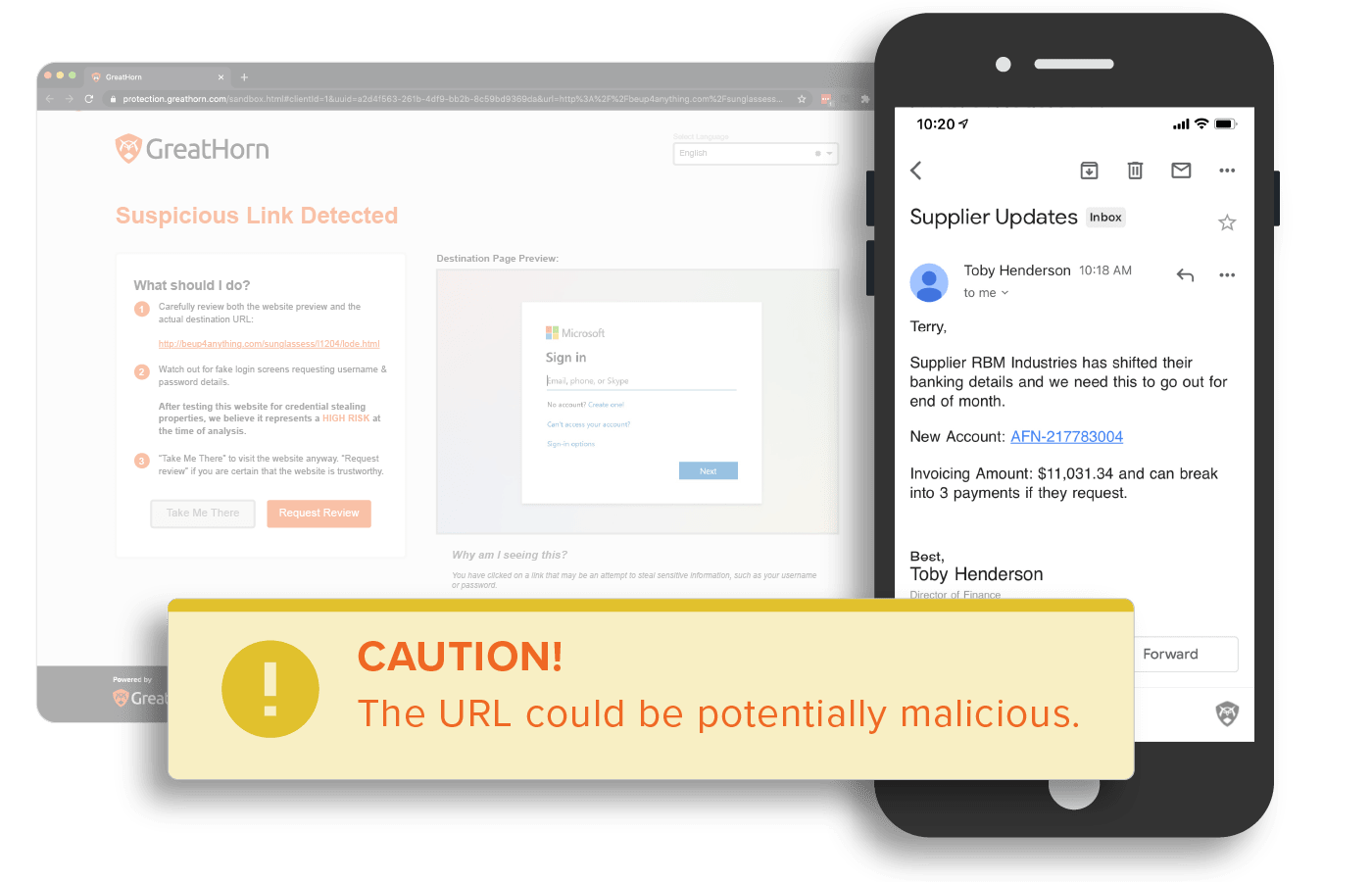
Protect Against Phishing Attacks and Data Loss
Eliminate the worry of business email compromise (BEC) attacks and account takeover with the most comprehensive solution to identify and mitigate phishing attacks. Protect your organization from the time an email is received through each potential user action. With effectiveness well beyond native email security, stay protected against credential theft and malware incidents.
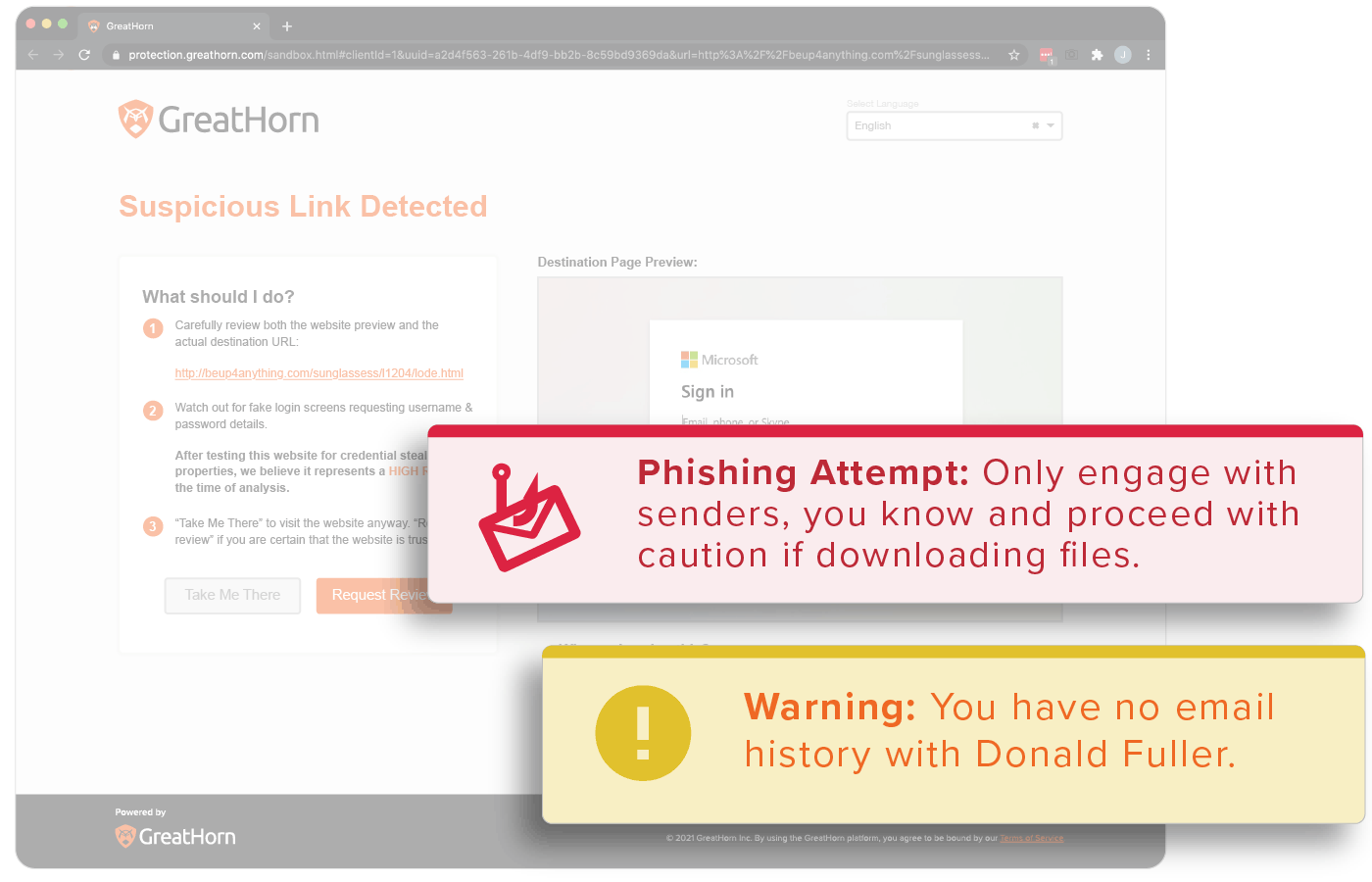
Spend Less Time Managing Threats
Spot real threats using advanced threat intelligence to immediately detect and automatically respond. Review, remove and manage threats across the entire environment in seconds with profile-driven granular engagement and visual intelligence for risk data. What’s more, simplified integration with existing SIEM/SOAR means less management.
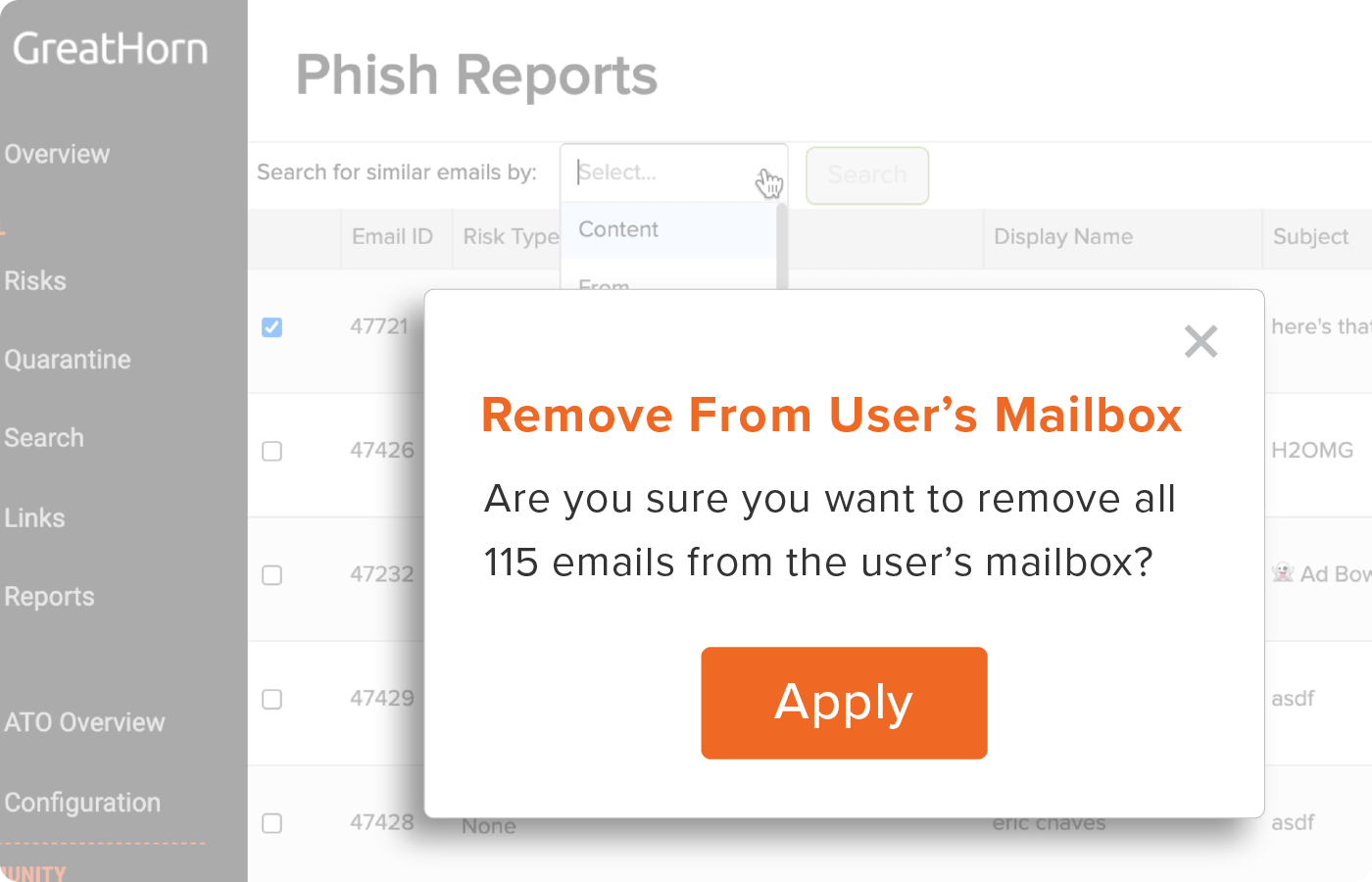
Educate Users in the Moment with Automated Smart Banners
Educate your employees on types and levels of email security risk using ‘smart banners’ for added awareness and protection. Easily integrate with security awareness vendors and build Report Phish buttons into a continuous workflow. Automation of these tasks help users better understand risk and enable them to make more informed decisions in the moment, learning well beyond traditional security awareness training.
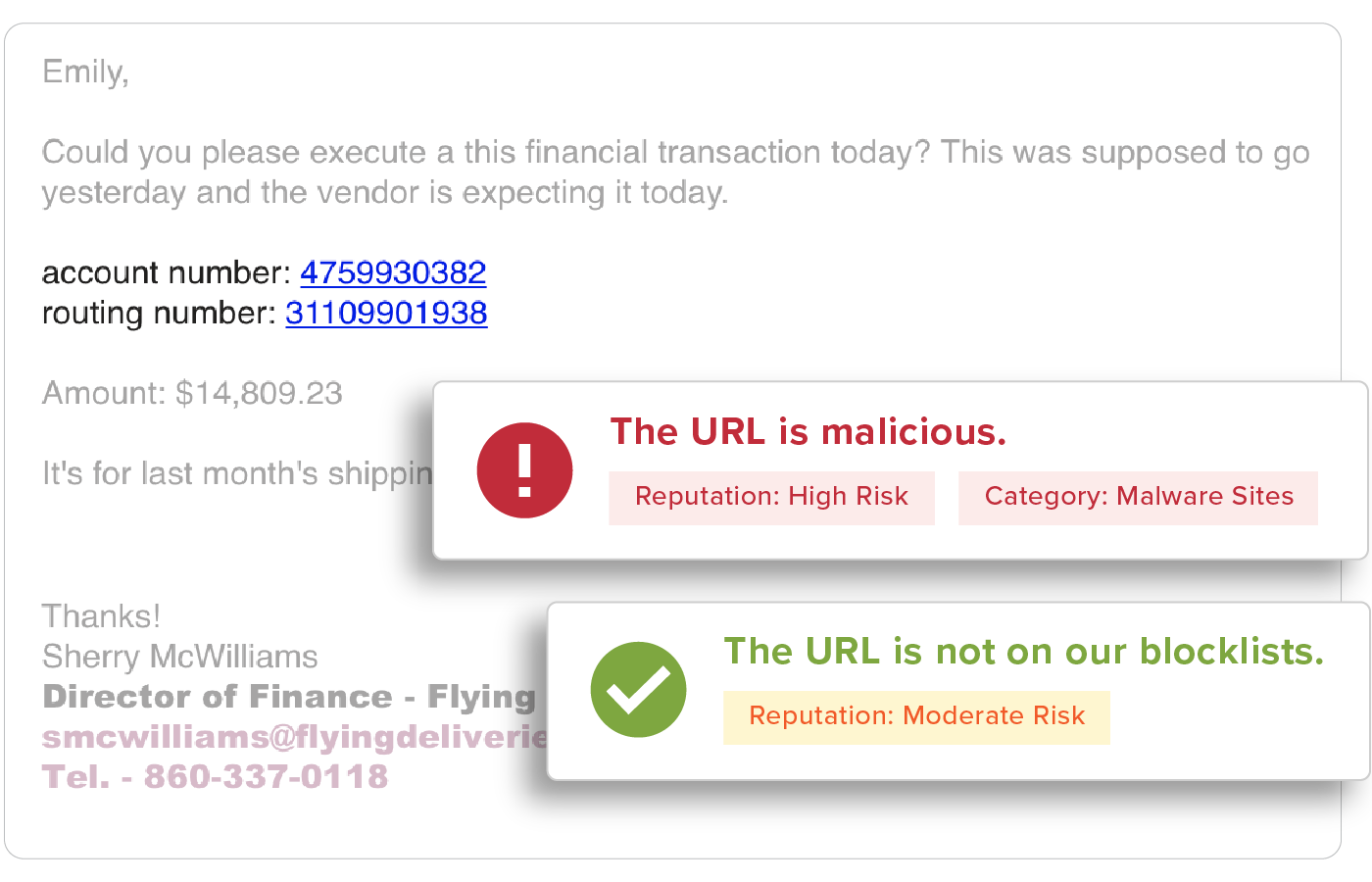
Eliminate Risk with Layers of Protection
Go beyond native controls with sophisticated ML/AI and granular, easy-to-use administrative capabilities
Microsoft Integration
A Seamless Experience with GreatHorn
- Deployment: Be up and running in less than 5 minutes.
- Policy Configuration: Out-of-the-box default risk types for immediate protection.
- No Downtime: No changes to mail routing or MX records, so mail always gets to your users.
- PreAnalysis: Detect and apply automated remediation prior to delivery to an end user’s inbox.
1 in Every 500 Messages
received by a user is a potentially malicious attack
What Threats Are Getting Through to Your End Users?
Get Your FREE Email Threat Assessment!
100%
Fewer account takeovers
89%
Reduction in user engagement with customized banners
100%
Decrease of malicious link clicks
“GreatHorn quantifiably reduced the risk of email by 99%, based on how many emails are quarantined versus the number of userreported suspicious emails.”
Industry Recognition