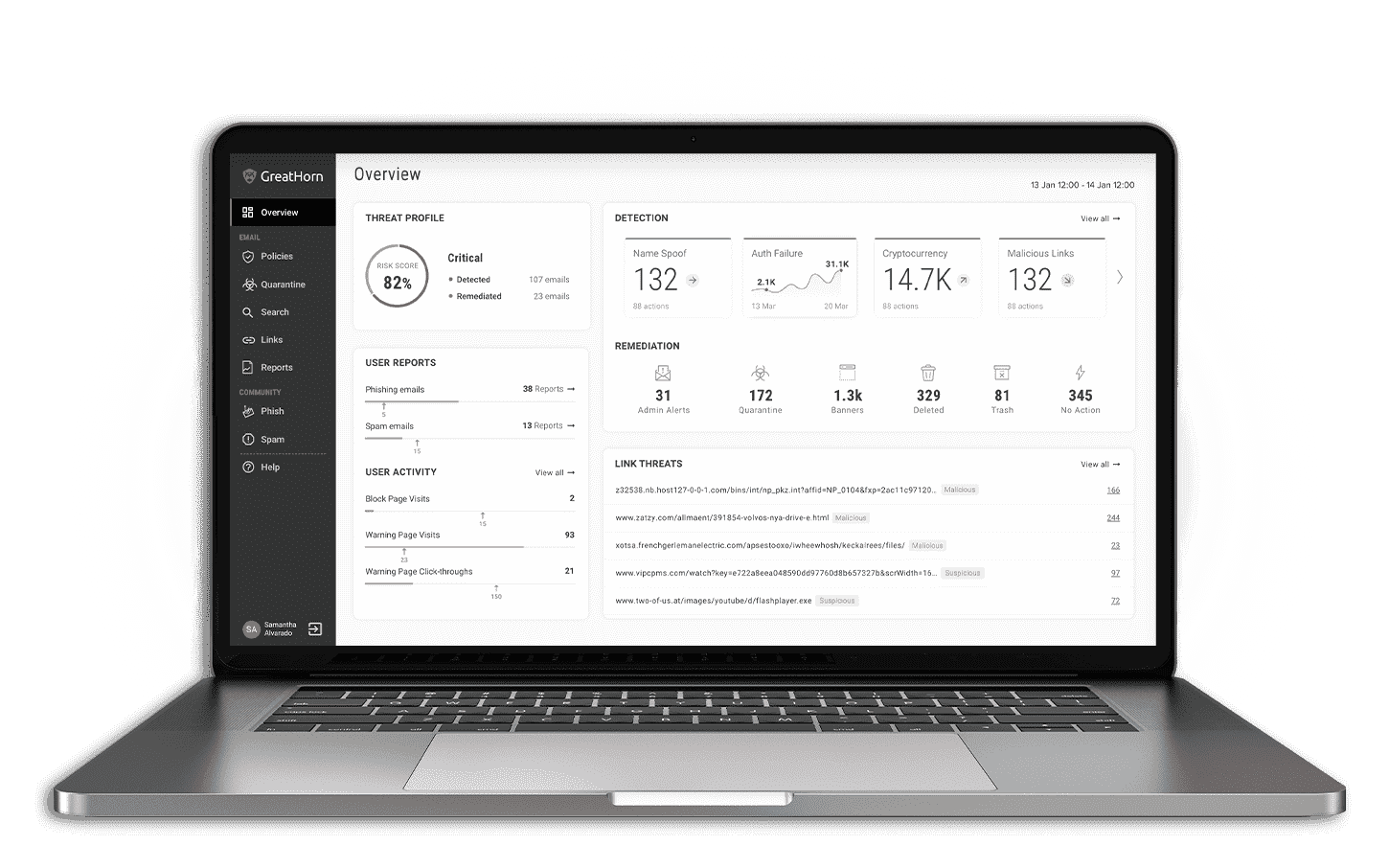
Advanced Cloud Email Security Solution
Reshaping Cloud Email Security to Address Today’s Risks
If your organization has shifted to a cloud-native email platform it’s time to reevaluate your email security to address today’s sophisticated zero-day attacks, and complex social engineering tactics like business email compromise and email account compromise.
GreatHorn Cloud Email Security Platform changes the way you manage risk, layering sophisticated detection of polymorphic phishing threats with user engagement and integrated incident response, allowing your organization to address advanced threats at the moment risk enters your environment.
Built on the Cloud, For the Cloud
No changes to mail routing or MX records, 5 minute deployment, and out-of-the-box default risk types give you the immediate protection you require.
End User Education at the Moment of Risk
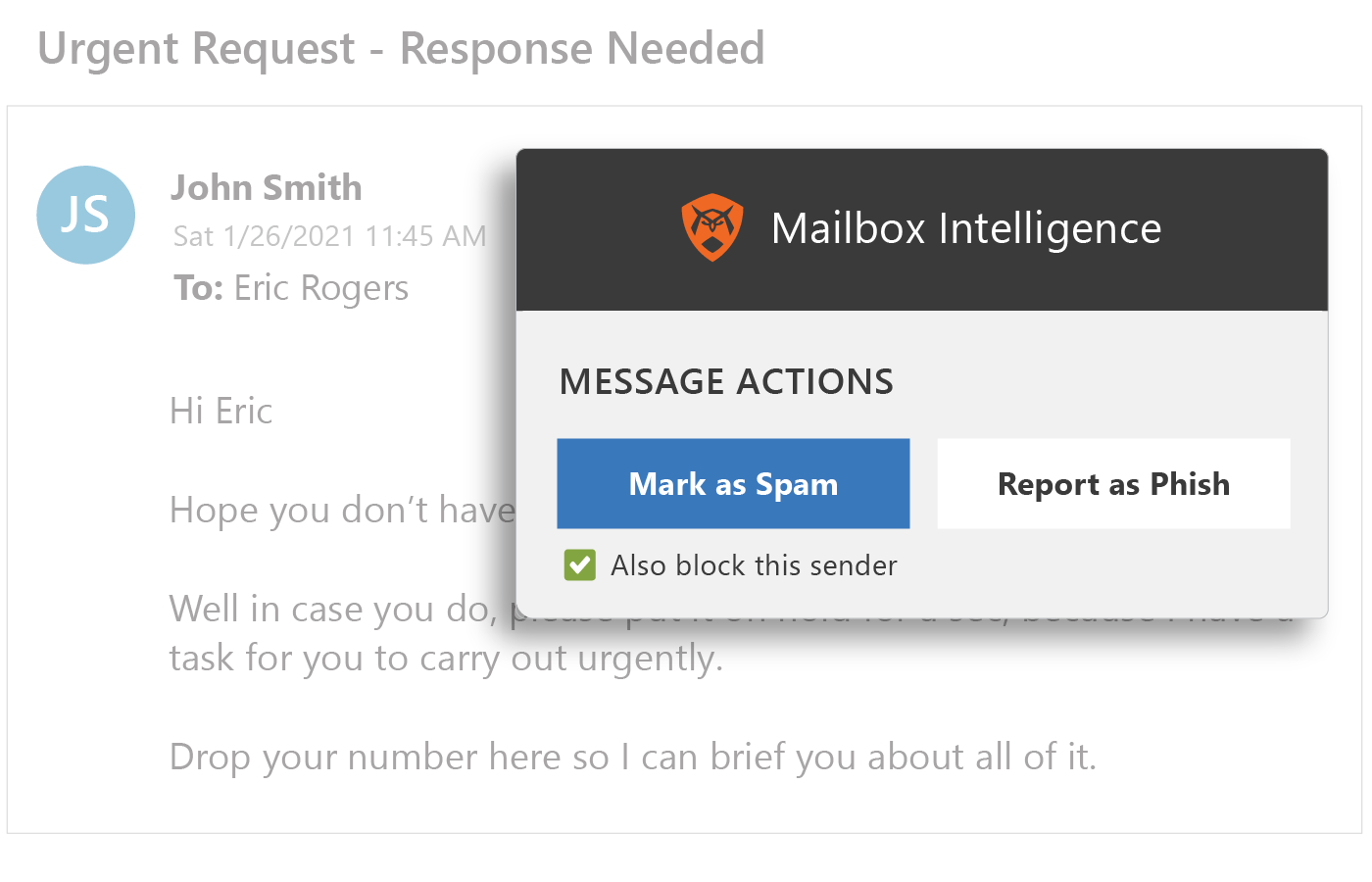
Continuous engagement helps train end users at the moment a potential phish enters their inbox.
Comprehensive Facts to Detect and Respond
Using artificial intelligence and machine learning, accurately identify risk areas, threat patterns, and zero-day phishing attacks to reduce response time.
Get Your FREE Email Threat Assessment
Learn what advanced threats are currently getting through your existing email security and into your end users’ mailboxes.
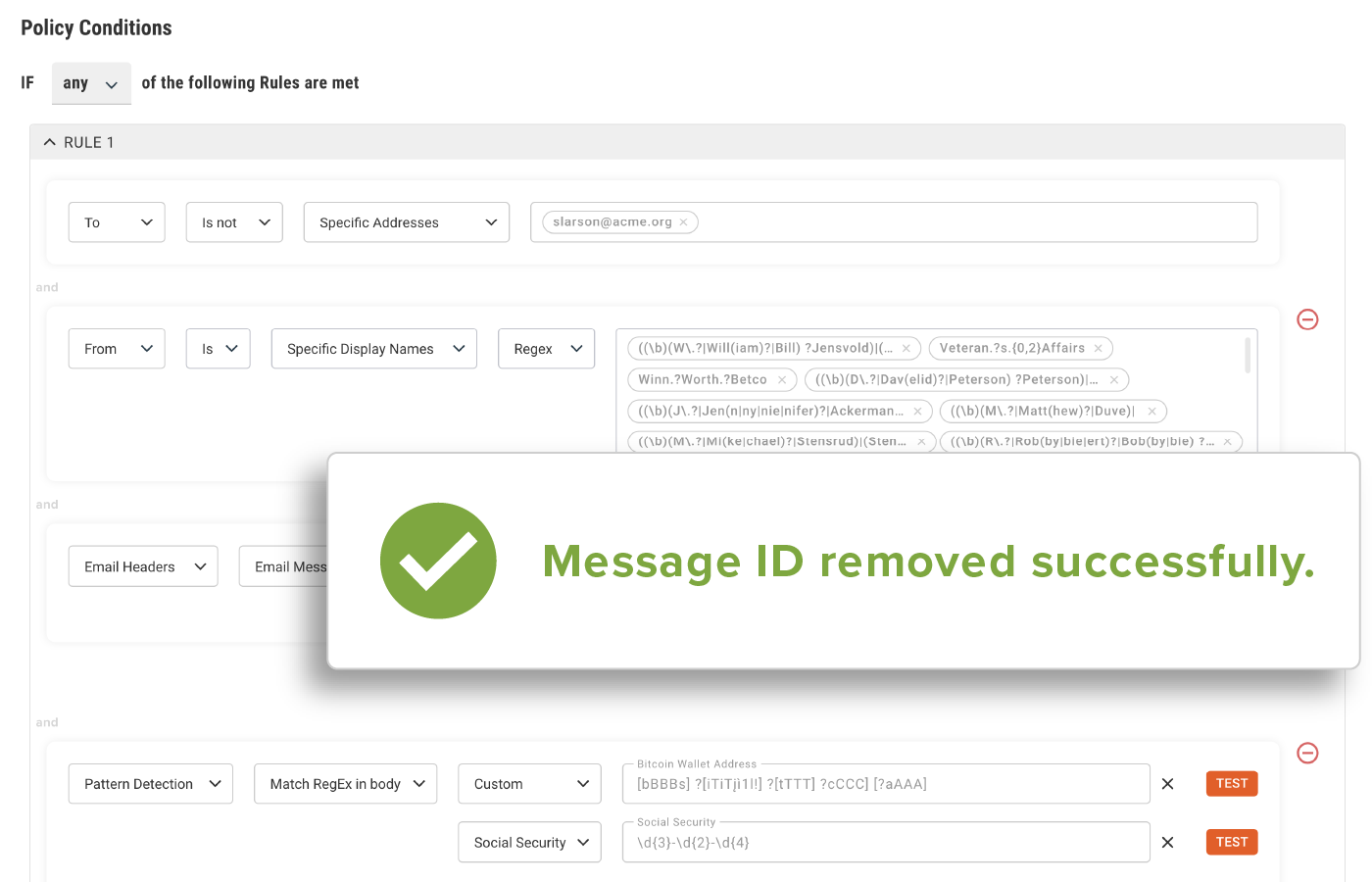
Advanced Anomaly Detection
Detect the most sophisticated phishing attacks and apply automated actions to every area of risk across the entire phishing attack lifecycle.
- “Out-of-the-box” spoofing detection using AI, ML and data science
- Evaluate relationships, communication patters, and technical fingerprints
- Automatically apply controls, eliminating the “one-size-fits-all” approach
- Access to emerging malicious attacks, including zero-days, with policy updates and recommended actions
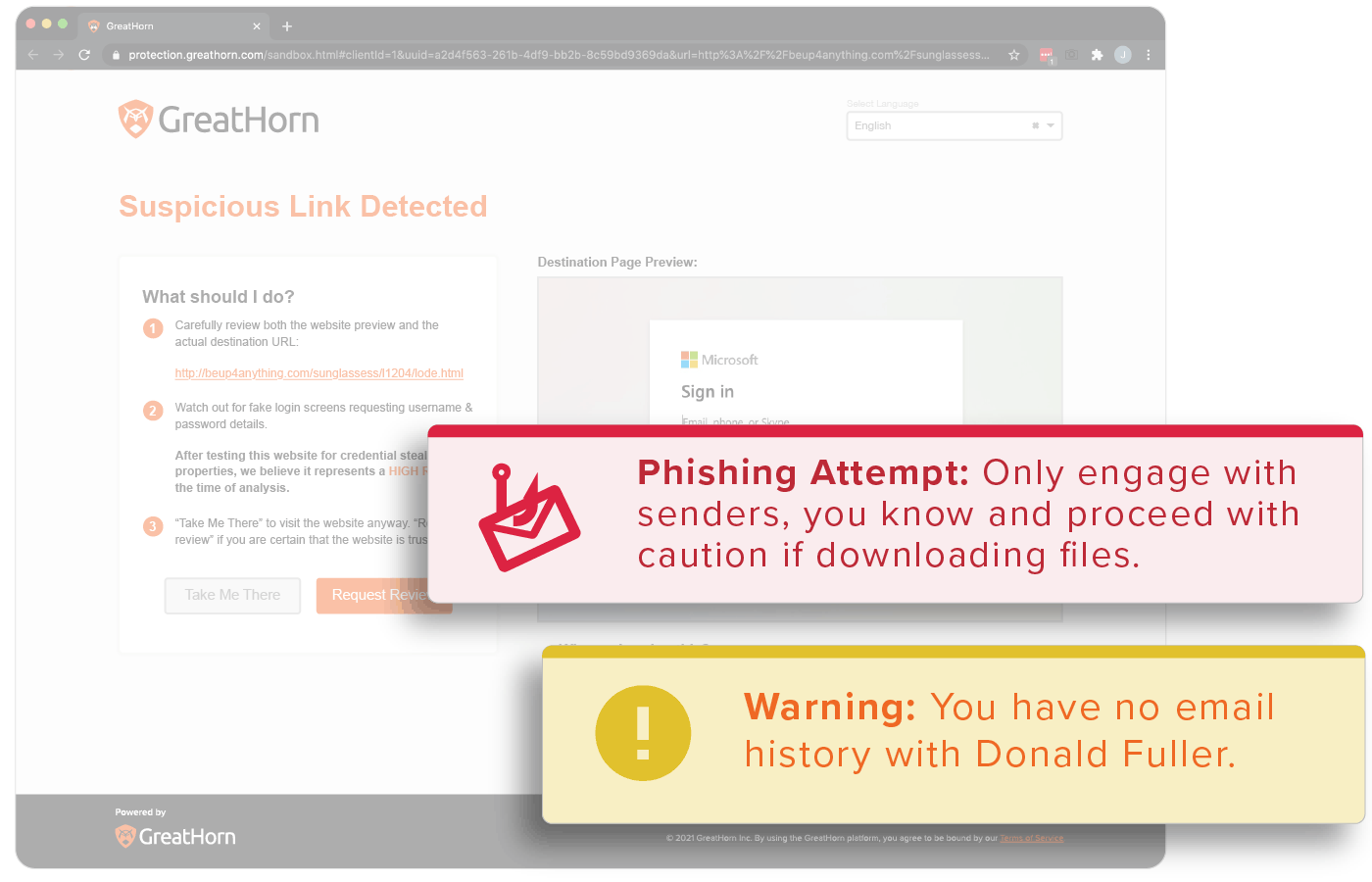
Empower Your End Users
Provide your end users with the contextual information they need to make the most informed decisions.
- Block malicious URLs
- Layer warning pages on suspicious links
- Apply automated and customized smart banners, based on risk
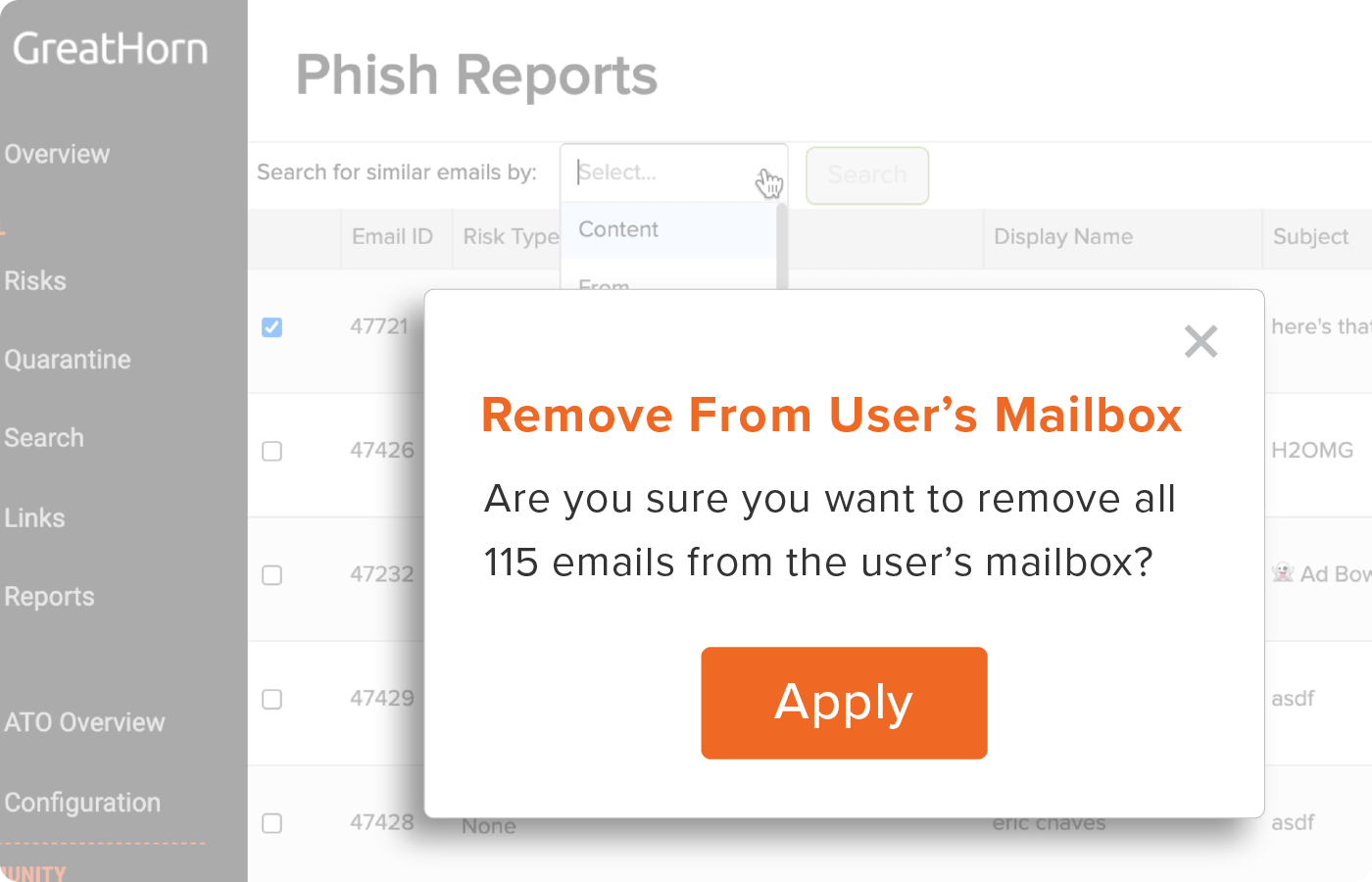
Simplified Detection and Response
Comprehensive incident respond allows organization to easily find and remove threats in just seconds.
- Granular search functionality across the entire email envelope identify all emails with matching criteria.
- Immediately identify and quarantine individual or bulk emails across your entire email environment.
- Preconfigured integrations and open APIs allow you to build workflows across your security solutions.
Enabling a Seamless Phishing Prevention Experience
Incorporate end users into your email security posture, with real-time reporting, notifications and seamless remediation.
- Enable users with “report phish” and “report spam” buttons with instant notifications.
- Give users the information they need as they interact with each email, using stoplight analytics.
- Receive real-time phish notifications and reporting, for bulk removal.
![[eBook] Things to Consider: Microsoft 365 + GreatHorn](https://www.greathorn.com/wp-content/uploads/2023/05/eBook-Microsoft-365-GreatHorn.png)
![[eBook] Things to Consider: Google Workspace + GreatHorn](https://www.greathorn.com/wp-content/uploads/2023/05/eBook-Google-WorkspaceGreatHorn.png)
![[Whitepaper] Measuring the Value of Email Security Solutions](https://www.greathorn.com/wp-content/uploads/2023/05/Whitepaper-Measuring-the-Value-of-Email-Security-Solutions.png)
![[Report] 2023 State of Email Security: Key Trends and Insights](https://www.greathorn.com/wp-content/uploads/2023/03/Report-2023-State-of-Email-Security.png)