Detecting Malicious & Suspicious URLs
Malicious & Suspicious URL Protection
With two to three new domain names being acquired and observed every second on the internet, URLs are a prime target for cybercriminals to leverage in their phishing campaigns. These URLs are used to deliver payloads automatically, harvest credentials, or collect other sensitive information. Even when a website isn’t malicious at the moment of delivery to a user, links can turn malicious any minute.
How Do You Know if a URL is Malicious?
With 3.7% of all emails containing a potentially malicious URL that evade native email platforms and legacy secure email gateways defenses, organizations are faced with users falling victim to phishing emails and clicking on links. Malicious URLs are links, often embedded within phishing attacks, created by threat actors whose goal is to download malware, steal credentials, personal information and/or money.
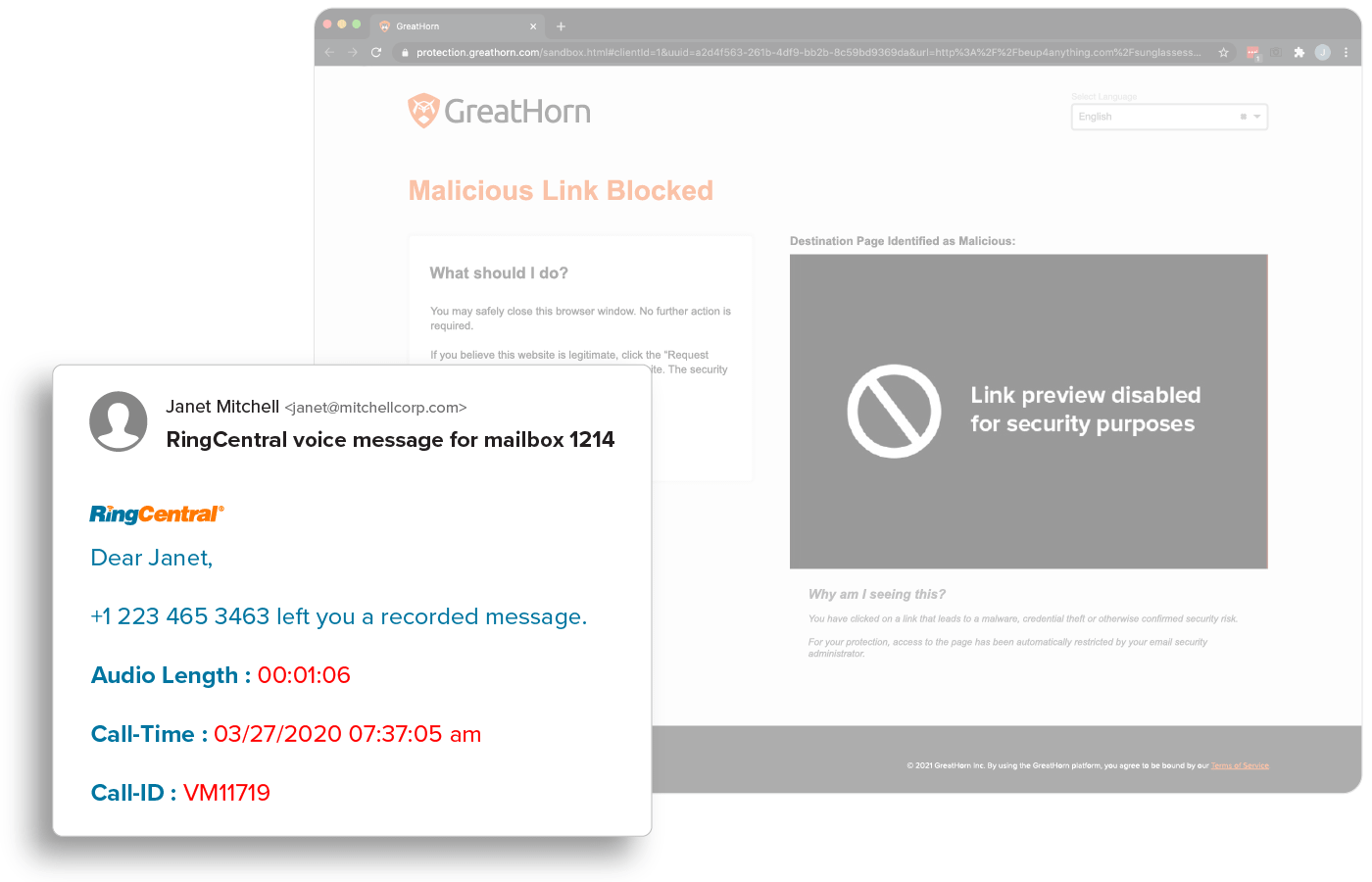
Malicious URL Detection
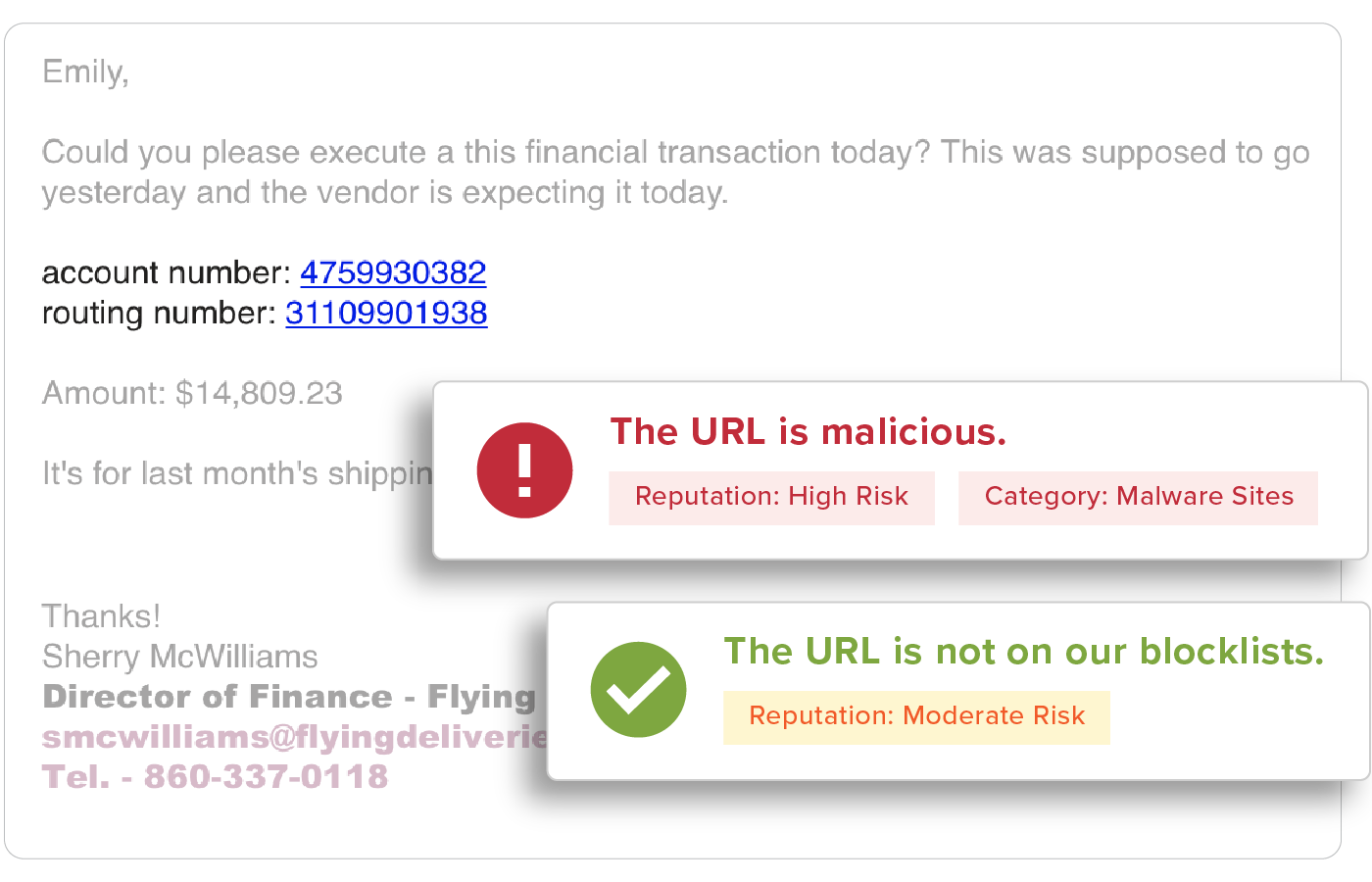
URLs are easy to manipulate so that no two are delivered the same and are a top threat vector within phishing attacks. All URLs are inspected upon delivery to identify and detect malicious websites. GreatHorn also provides an additional layer for suspicious URLs that turn malicious, using time-of-click analysis using computer vision to analyze suspicious links.
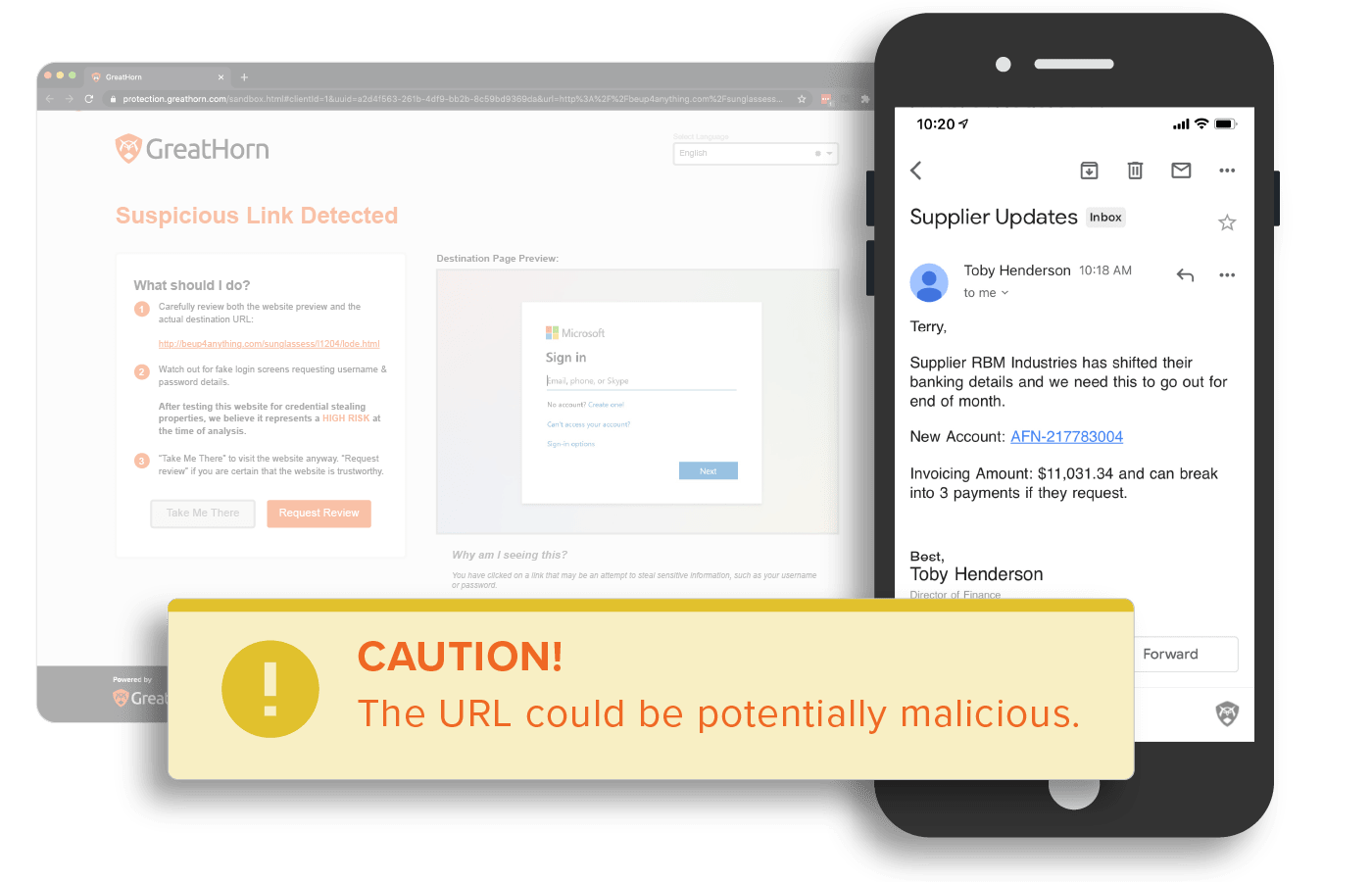
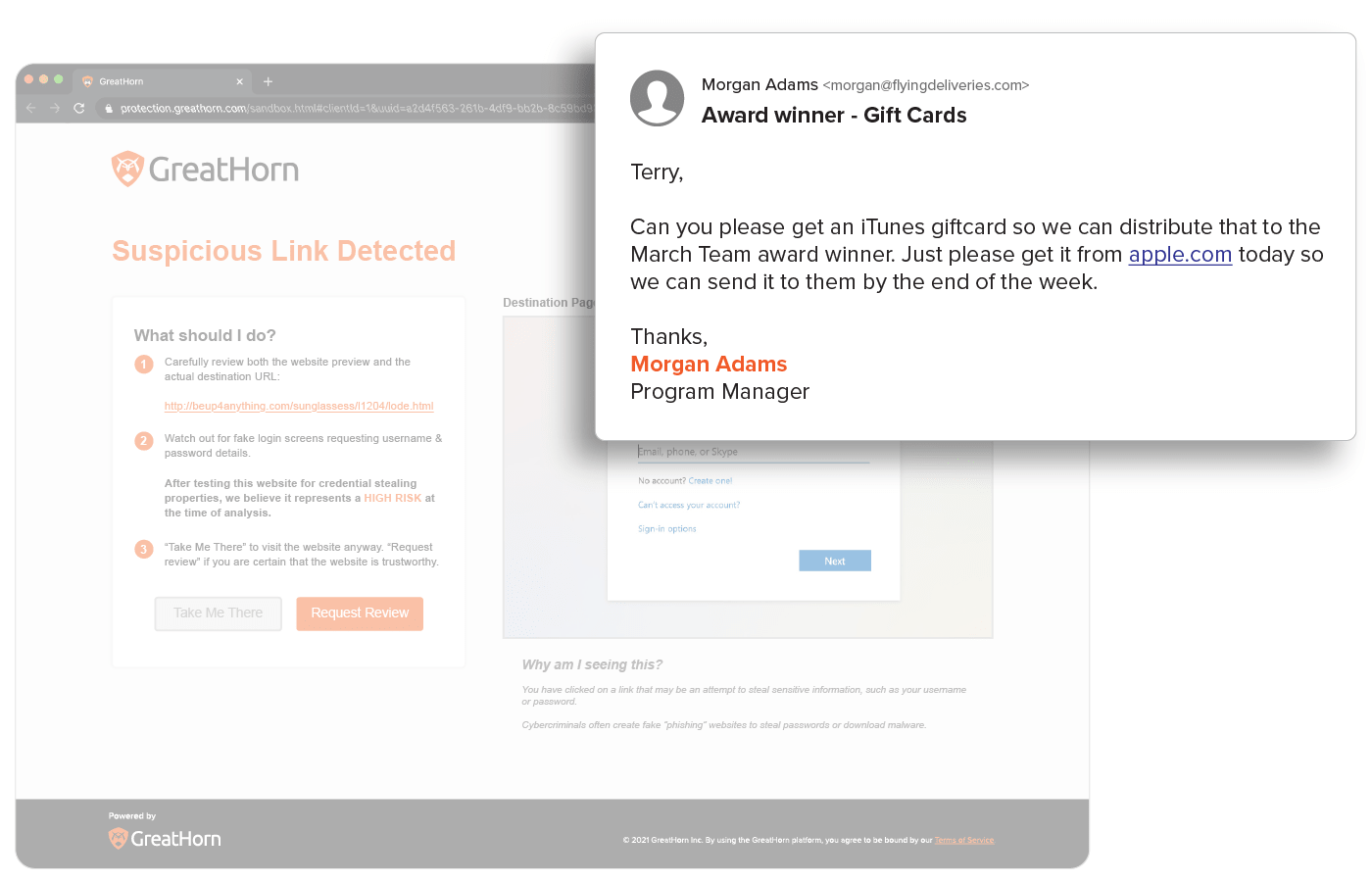
Suspicious URL Detection
URLs are analyzed using machine vision to detect any anomalous content on the destination. With GreatHorn’s Link Protection page, users are educated with a preview of the destination, the risk of credential harvesting, and steps they should take to minimize their risk.
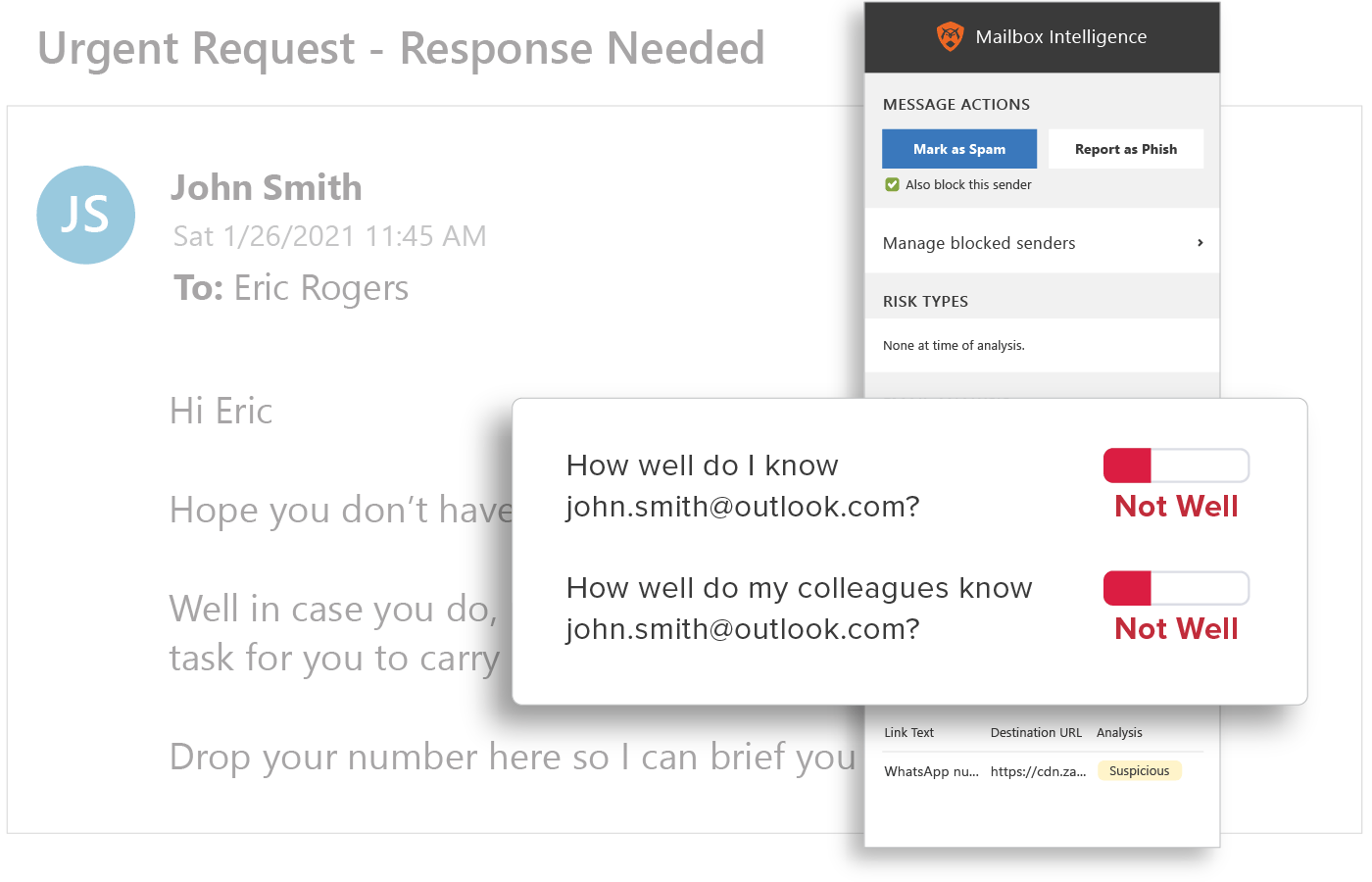
Behavioral Analytics
GreatHorn analyzes all communication patterns between senders and recipients using behavioral analytics within our AI and ML models, providing organizations with immediate detection and insight into anomalous emails.
End User Education
Provide users with the context they need to help them make better decisions by applying automated and customized smart banners, Mailbox Intelligence, Suspicious Link pages, and more.
![[eBook] Things to Consider: Microsoft 365 + GreatHorn](https://www.greathorn.com/wp-content/uploads/2023/05/eBook-Microsoft-365-GreatHorn.png)
![[eBook] Things to Consider: Google Workspace + GreatHorn](https://www.greathorn.com/wp-content/uploads/2023/05/eBook-Google-WorkspaceGreatHorn.png)
![[Whitepaper] Measuring the Value of Email Security Solutions](https://www.greathorn.com/wp-content/uploads/2023/05/Whitepaper-Measuring-the-Value-of-Email-Security-Solutions.png)
![[Report] 2023 State of Email Security: Key Trends and Insights](https://www.greathorn.com/wp-content/uploads/2023/03/Report-2023-State-of-Email-Security.png)