Employees are the first line of cyber defense, soldiers in a war that is being waged primarily in their inbox. In and amongst the hundreds of emails the average office worker receives each day, are spam and phishing emails.
Every security professional knows the difference between spam and phish. But that knowledge, regardless of how much effort is exerted into training, is rarely transferred to users. However, most firms have armed their employees with “Report a Phish” buttons to make it easier to alert security teams to these potentially malicious emails. As a result, security professionals must deal with a deluge of reports, manage the ongoing efforts to clean out their user-reported phish folders or close out tickets that are generated by these reports.
What is Spam?
Spam Definition:
Unsolicited, usually commercial, emails sent to a large number of recipients.
Example of User-Reported Phish: Actually Spam
This email was reported as phish by a user for the security team to investigate. As you can see, this email represents no risk to the organization. However, it may be an annoyance to the user.
Other common types of spam include political messages and chain letters.
Non-malicious spam emails like the example shouldn’t require security intervention. Users should be able to easily block these unsolicited emails.

Get the Ebook How-to Guide: Streamlining User-reported Phishing
In Microsoft 365, a user can right-click on a message. Then click on “Report Junk” and then click “Block”.
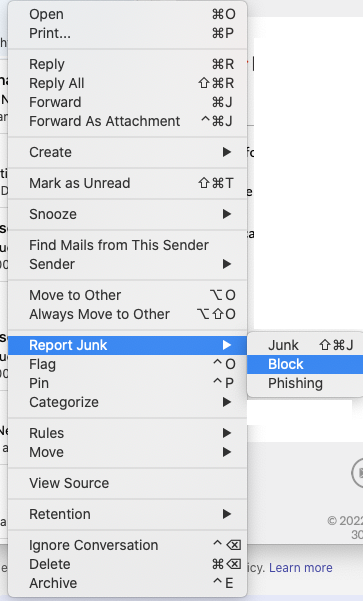
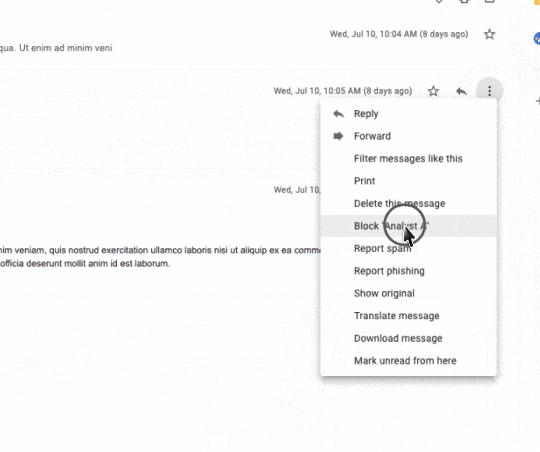
In Google Workspace (Gmail), a user can click on the vertical dots on the top of the email envelope and click “Block ****”.
What are Phish?
Phish Definition:
Emails appearing to be from a reputable company or known sender to steal personal information and/or achieve financial gain.
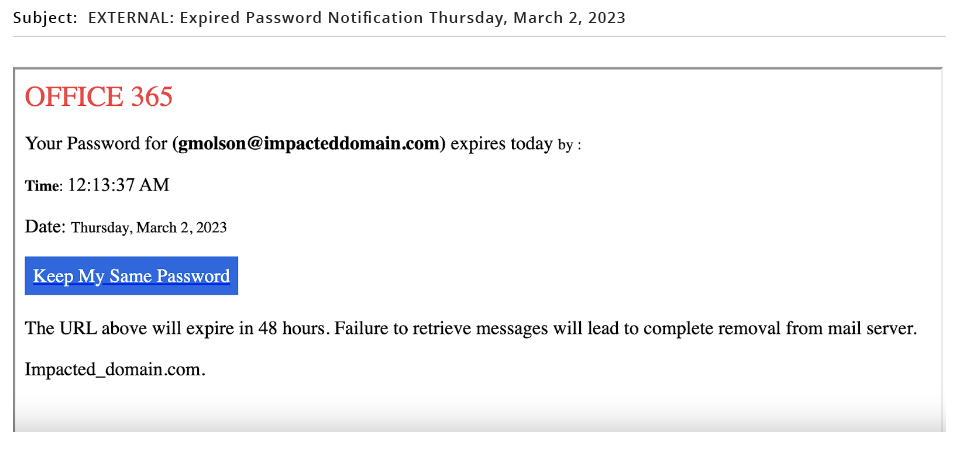
Example Phish
This email was reported as Phish by a user. As you can see, this email is coming from a sender who the recipient has no email history with and as a result the user is requested to use caution. If clicked by the user, they would be directed to an impacted domain used for credential harvesting. As part of the URL string, the user’s email is passed through to the destination site, appearing as a legitimate Microsoft login page where only the existing password must be entered.
In this case, the user reported the Phish for further investigation by the security team, who subsequently could Quarantine the email and any similar emails that may have reached other users’ inboxes.
Suspicious emails like this are what the user-reporting buttons were designed to address.
The Impact of User Reported Phish vs Spam
Reporting harmless spam may seem exactly that, harmless. But that’s not entirely true. Like the 911 system, when non-emergency calls tie up valuable resources, leaving true emergencies at risk of going unanswered, user-reported spam requires time and effort by the security team, delaying them from responding to true threats.
While the difference between spam and phish may appear to be minimal for some, as a security professional you know that only one represents risk and poses a threat to your organization. One must be investigated, identifying if any other users have a similar message in their inbox. And most important, has any user engaged with the email? Yet, because both emails have been reported as phish, they both require time and effort by the security team.
Learn more about how you can more effectively manage user-reported phish…
Download GreatHorn’s newest how-to guide,
“Streamlining User-Reported Phish.”





