Latest Release of Award-Winning Email Security Platform Combats All Forms of Phishing, Malware, and Malicious Links with Advancements in Detection, Defense, and Response
 Waltham, MA – November 14, 2018 – GreatHorn, the leading cloud-native email security provider, today announced the expansion of GreatHorn Email Security into a comprehensive Platform, designed to protect organizations from email threats at every vulnerable point – from time of delivery to any time post-delivery. This major new expansion of the Company’s flagship solution addresses every potential stage of a phishing attack with integrated threat detection, protection, defense, and incident response.
Waltham, MA – November 14, 2018 – GreatHorn, the leading cloud-native email security provider, today announced the expansion of GreatHorn Email Security into a comprehensive Platform, designed to protect organizations from email threats at every vulnerable point – from time of delivery to any time post-delivery. This major new expansion of the Company’s flagship solution addresses every potential stage of a phishing attack with integrated threat detection, protection, defense, and incident response.
Most email security solutions – whether native cloud protections or legacy gateways – were designed using a binary model that blocks messages with known threat characteristics and lets all other email through. Since such a method is principally appropriate for malware rather than the payload-free world of phishing, sophisticated attacks easily bypass such protections. By combining proprietary and industry threat intelligence with deep relationship analytics, technical and social fingerprinting, and anomaly identification, GreatHorn can more accurately detect a wider range of both emerging and targeted threats.
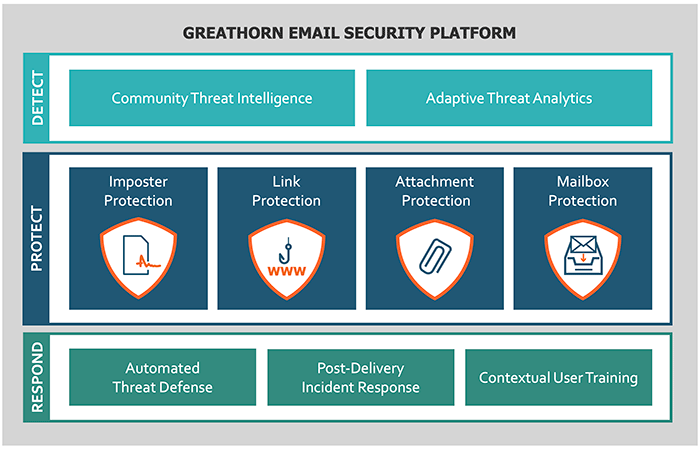
As part of this release, GreatHorn has substantially enhanced the company’s core adaptive threat detection engine, expansive threat defense actions, and robust post-delivery incident response capabilities. Most notably, the revamped platform introduces four new protection modules, customized by threat type, that protect enterprises throughout the email lifecycle:
- Imposter Protection – Automated protection against imposter attacks such as executive / employee impersonations, look-alike domains, spoofing attacks, and business email compromise.
- Attachment Protection – Automated threat identification and removal of malicious attachments / malware, as well as advanced protection and risk mitigation against zero-day threats with file isolation and both time-of-receipt and time-of-click analysis.
- Mailbox Protection – Personalized email protection for users based on individuals’ communication patterns and relationships, available as an Outlook or Chrome plug-in. The plug-in offers advanced functionality, including personal block lists and enhanced phish reporting capabilities.
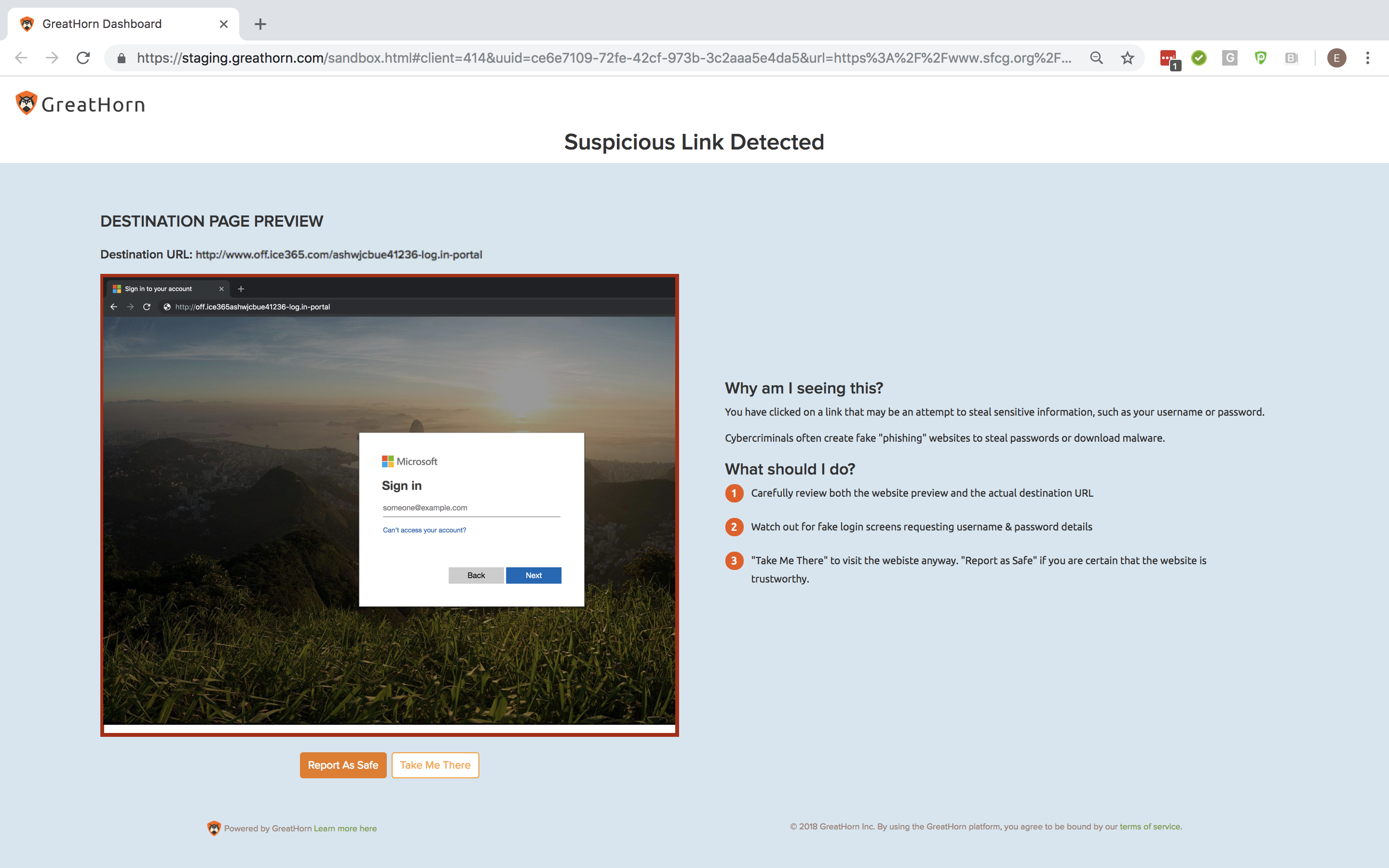
- Link Protection – Protection that will block both malicious URLs and credential theft attempts by using fully automated URL sandboxing, with mailbox- / user-level click-tracking, administrative alerting, and credential theft threat isolation.
“As one of the nation’s largest financial life management firms, United Capital Financial Advisers is always vigilant in its cyber security and is constantly striving for improvements,” said Brandon Gage, senior vice president of technology at United Capital. “Imposter Protection from phishing and other fraudulent cyber attacks is a part of our critical focus in the GreatHorn implementation. We’re pleased with our collaboration with GreatHorn and have already seen additional value with the solution’s improved spoofing detection.”
Adaptive Threat Detection
GreatHorn Email Security combines multiple sources of threat intelligence – both third-party and proprietary – with adaptive threat analytics based on an organization’s unique communication patterns. In this release, GreatHorn has:
- Added the ability to identify attachments and links as “suspicious” based on an analysis of multiple characteristics
- Strengthened behavioral and relationship algorithms to improve accuracy in calculating relationship strength and communication patterns; and
- Extended organizational and technical fingerprinting to identify more nuanced anomalies such as domain authentication drift.
Automated Threat Defense
Each of GreatHorn’s protection modules includes a wide variety of remediation actions that can be customized for an organization’s risk tolerance and business processes. These actions automatically defend against identified threats and reduce manual intervention time. Additional features include:
- Threat-specific context and warnings using configurable banners and user training options;
- Expanded email movement and removal options to customize threat handling; and
- Automated URL rewriting and sandboxing that will include analysis at both ingest and time-of-click, as well as administrative insight and management over user interaction with suspicious links.
Post-Delivery Incident Response
As part of its commitment to the entire lifecycle of email security, GreatHorn includes a robust post-delivery incident response module that makes it fast and easy to find and collectively remove newly identified threats from user inboxes no matter how long ago they were delivered. This latest release includes substantial improvements to this functionality with:
- Deep forensic capabilities with improved details and analysis of both user behavior and domain-wide exposure;
- Robust search interface to conduct complicated, multi-vector searches; and
- Simplified process for email removal with expanded functionality.
“GreatHorn is known for industry-leading phishing protection,” said Kevin O’Brien, CEO and co-founder of GreatHorn. “With GreatHorn Email Security, we have expanded that protection to offer enterprises a truly comprehensive email security platform, tuned to safeguard them from the full range of today’s advanced email-borne threats. We believe that email is the most critical business communication system in existence and that requires best-in-class protection, not just a small point solution, plug-in or add-on. That is what this new release uniquely provides.”
About GreatHorn
GreatHorn simplifies email security by automating the cycle of email security – through continuous threat detection, defense, and incident response. Office 365 and G Suite customers using GreatHorn not only gain enterprise-class protection against both sophisticated phishing attacks and traditional threats, they also reduce complexity, manual remediation time, and negative impact on business operations.
By combining deep relationship analytics with continuously evolving user and organizational profiling, GreatHorn’s cloud-native email security platform provides adaptive, anomaly-based threat detection that secures email from malware, ransomware, executive impersonations, credential theft attempts, business services spoofing, and other social engineering-based phishing attacks. More information is available at www.greathorn.com.