Community Threat Protection
Collective Intelligence to Improve Your Protection
Phishing attacks are continuously evolving to evade detection, many leveraging zero-day threats and suspicious links that turn malicious. Protecting your organization from these threats is a necessity. With GreatHorn’s Community Threat Protection, you receive the benefit from collective knowledge and experience, combining aggregated active phish data across the community with our Threat Intelligence Research Team, to identify risks before they can do damage.
Minimize Your Attack Surface
Identify threat patterns at the moment they emerge within the entire community, quickly detecting in your environment and remediating and reducing your risk.
Incorporate Community Intelligence
Using threat algorithms, set your individual risk tolerance threshold to balance notifications and automated action from community intel.
Improved Risk Management
Leveraging community data, shared across administrators, GreatHorn’s Threat Intelligence Team continuously builds risk types and actions that can block threats proactively.
Get Your FREE Email Threat Assessment
Learn what advanced threats are currently getting through your existing email security and into your end users’ mailboxes.
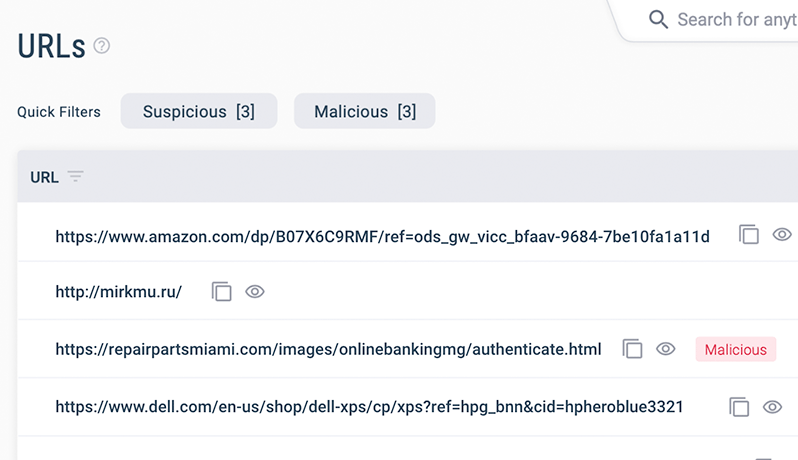
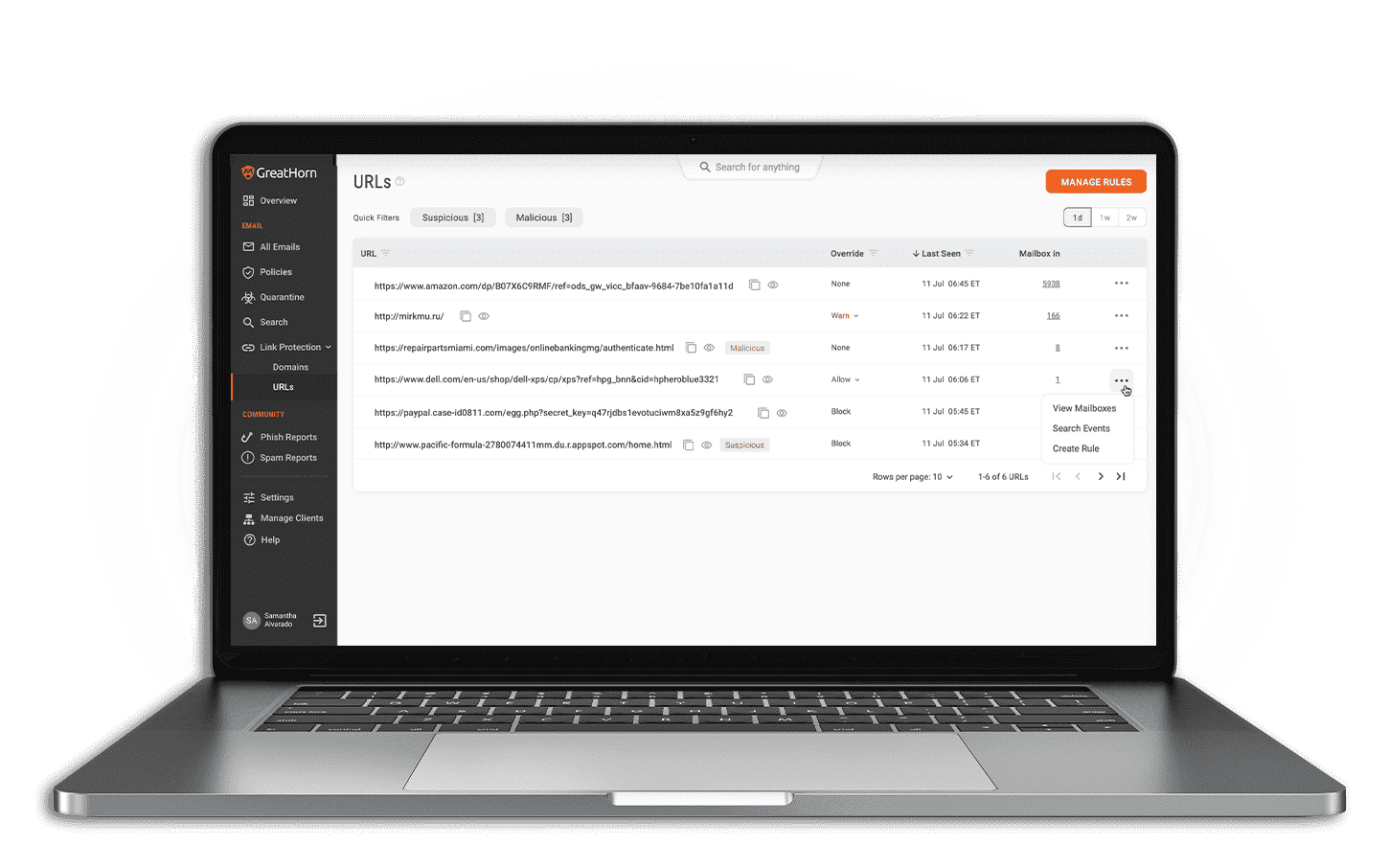
Zero-Day Threat Detection
Identify emerging threat patterns using data from billions of emails from within the GreatHorn community – quicker than traditional threat intelligence feeds.
Community Threat Data
Using the network affect, sourced from aggregated actions of administrators and engaged end users, receive proactive notifications displaying matching indicators of threat or risk within your environment.
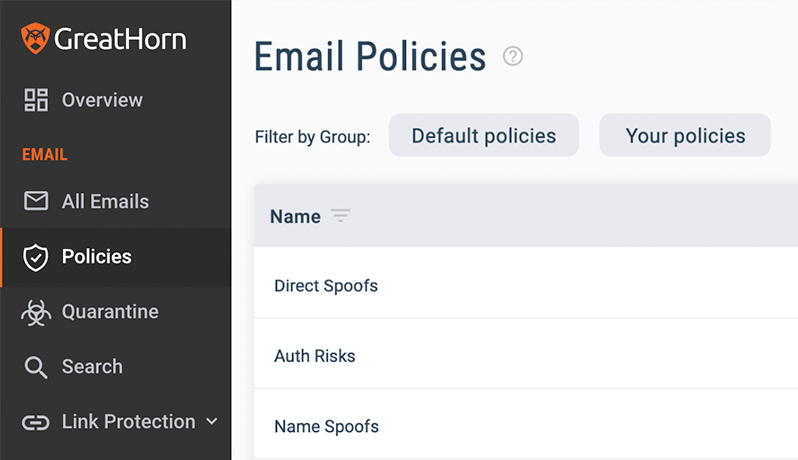
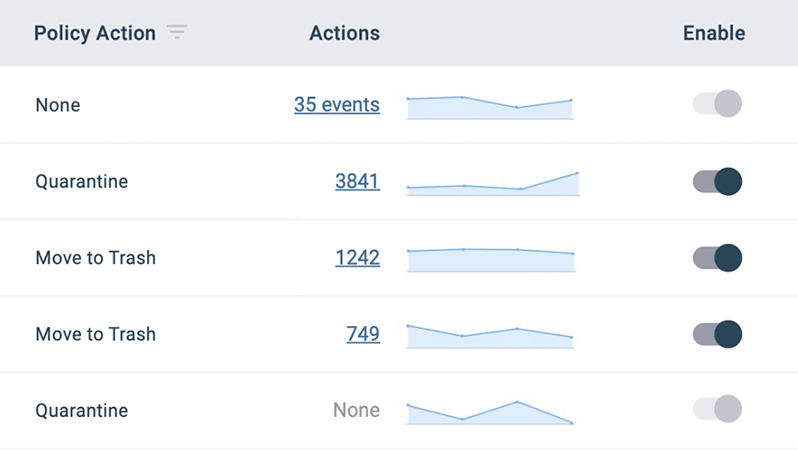
Threat Intelligence Research Team
GreatHorn’s Threat Intelligence Research Team identifies and curates trends and patterns in the emerging threat landscape, providing the context administrators need to further improve detection and automated action to remediate threats within their email environment.
Customized Actions to Improve Efficiency
Balance your organization’s risk tolerance with action based on aggregated threat indicators. Choose from notifications or automated actions to reduce your effort proactively managing risk within your email.
![[eBook] Things to Consider: Microsoft 365 + GreatHorn](https://www.greathorn.com/wp-content/uploads/2023/05/eBook-Microsoft-365-GreatHorn.png)
![[eBook] Things to Consider: Google Workspace + GreatHorn](https://www.greathorn.com/wp-content/uploads/2023/05/eBook-Google-WorkspaceGreatHorn.png)
![[Whitepaper] Measuring the Value of Email Security Solutions](https://www.greathorn.com/wp-content/uploads/2023/05/Whitepaper-Measuring-the-Value-of-Email-Security-Solutions.png)
![[Report] 2023 State of Email Security: Key Trends and Insights](https://www.greathorn.com/wp-content/uploads/2023/03/Report-2023-State-of-Email-Security.png)