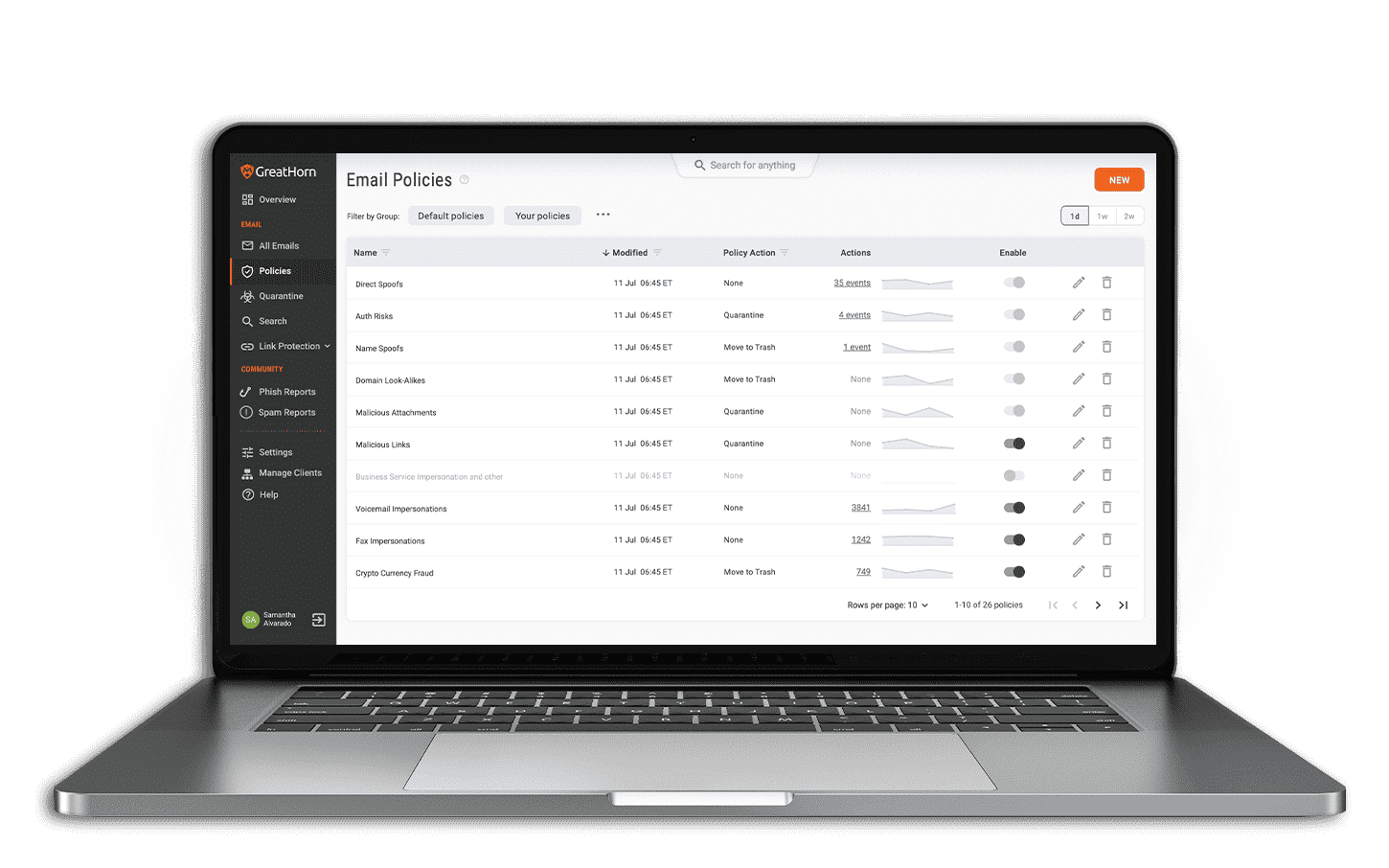
Proactive, Managed Email Security
End-to-End Cloud Management to Protect Your #1 Threat Vector
Phishing is rapidly and continuously morphing, creating exponential risks to every organization. Whether it’s traditional malware, zero-day threats, or links to recently compromised sites, your email security relies on ongoing management to keep pace with the evolving threat landscape. Many organizations have limited resources or lack the expertise in-house to optimize your email security to minimize your risk of advanced phishing attacks. GreatHorn can help by extending our team of email security experts to support your organization.
Extend your Expertise
Leverage GreatHorn’s technical experts and receive dedicated resources to most effectively manage your email security, detecting and remediating more advanced threats.
Simplify Risk Exposure
Reduce complexity with up-to-the-moment management of risk types and remediation improve your Mean-Time-to-Detect and Mean-Time-to-Respond to threats.
Optimize Reporting
With weekly threat reports, your team has a turnkey understanding of trends, detection and remediated actions that reduced your organizational risk.
Get Your FREE Email Threat Assessment
Learn what advanced threats are currently getting through your existing email security and into your end users’ mailboxes.
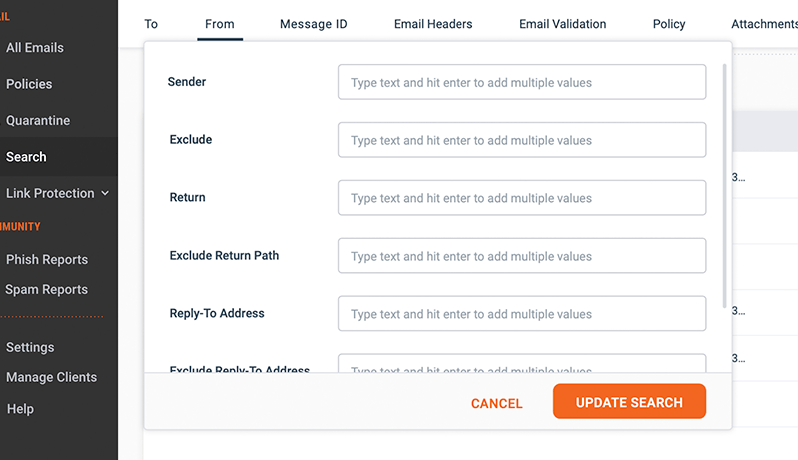
Improve Efficiency in Detection
Extend your defenses beyond your skilled security team with the support of GreatHorn’s Threat Response Team. With front-line defenses from the experts who see the threats first, your risk types are customized to automate detection and provide the highest level of defense against cybercriminals attacking your organization.
Maximum Response and Remediation
As emergent attack patterns are identified by GreatHorn’s Threat Response Team, GreatHorn immediately takes action to removes and remediate any threats sitting in user mailboxes. This is particularly helpful in situations where a link is weaponized after the initial threat scan has taken place. GreatHorn’s integrated incident response capabilities reduce your time to detect and respond, improving your ability to manage risk across your entire email system.

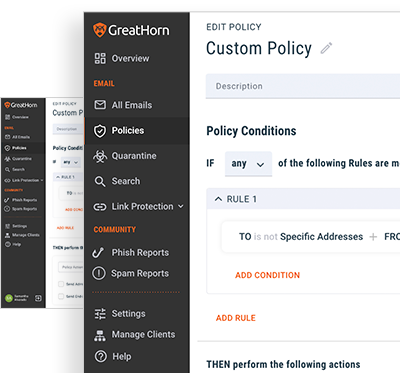
Ongoing Maintenance and Support
When your business is compromised by a phishing attack, every second counts. With GreatHorn’s proactive managed email security offering, you receive GreatHorn’s technical expertise, combined with our best-in-class cloud email security solutions, optimized to the level you need to maintain the most advanced email security posture.
![[eBook] Things to Consider: Microsoft 365 + GreatHorn](https://www.greathorn.com/wp-content/uploads/2023/05/eBook-Microsoft-365-GreatHorn.png)
![[eBook] Things to Consider: Google Workspace + GreatHorn](https://www.greathorn.com/wp-content/uploads/2023/05/eBook-Google-WorkspaceGreatHorn.png)
![[Whitepaper] Measuring the Value of Email Security Solutions](https://www.greathorn.com/wp-content/uploads/2023/05/Whitepaper-Measuring-the-Value-of-Email-Security-Solutions.png)
![[Report] 2023 State of Email Security: Key Trends and Insights](https://www.greathorn.com/wp-content/uploads/2023/03/Report-2023-State-of-Email-Security.png)