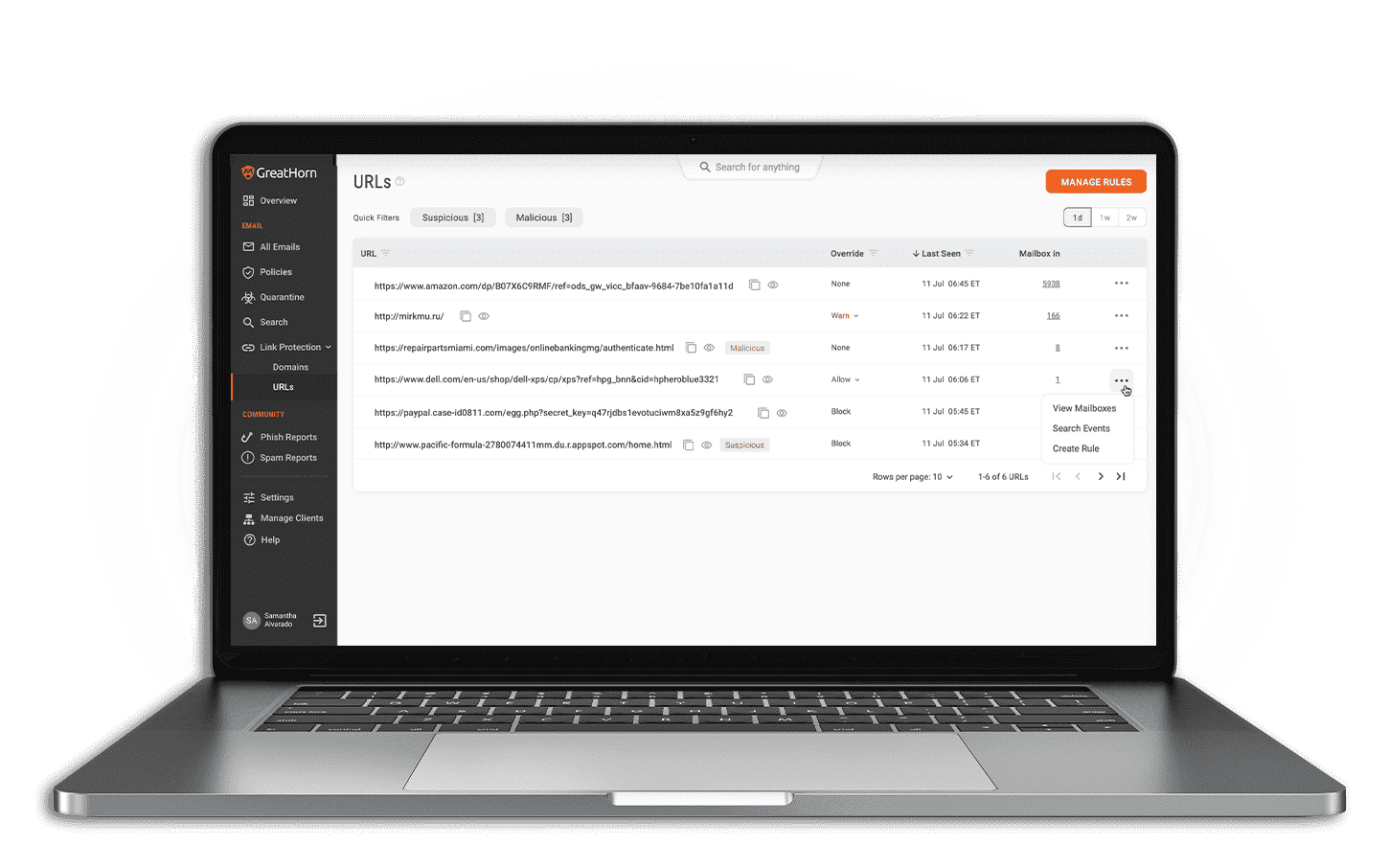
Identify Threats Faster with Advanced Threat Detection
Don’t Rely on Good/Bad – Detect Every Type of Threat
Legacy email security products rely on outdated, inaccurate, and inadequate threat detection models that put your organization at risk. Simple good/bad techniques struggle to identify more advanced threats such as business email compromise, impersonation, brand lookalikes, and advanced business service spoofing attacks.
GreatHorn’s Adaptive Threat Analytics uses machine learning and data science to quickly and automatically learn the legitimate communication patterns specific to each sender and recipient, making it easy to spot the anomalous emails, attachments, and links that typify suspicious content.
Relationship Strength
Strength of a sender’s individual relationship to the recipient, as well as a “friends of friends” system that accounts for the sender’s overall relationship with others in the recipient’s organization.
Spoofing Likelihood
Analysis for employee display name spoofs, domain spoofs, and domain look-alikes, including comparison against known email addresses, executive impersonation tactics, and email authentication standards.
Technical Fingerprint
Sophisticated analysis of domain reputation, sending IP, and header information, including determining variations in expected authentication results for DMARC, DKIM, and SPF.
Content Analysis
Deep content inspection based on keywords, regular expressions (RegEx), attachments, and URLs, to identify common spear phishing tactics—wire transfer and W2 requests, credential theft attacks, business service impersonations—all without storing the content or the mail.
Communication Patterns
Establishes an understanding of communication patterns unique to a specific individual and a specific organization, such as email frequency, volume, recipients, sending patterns and more.
Get Your FREE Email Threat Assessment
Learn what advanced threats are currently getting through your existing email security and into your end users’ mailboxes.
Because Every Second Counts
Detect challenging threats, such as:
- Zero-day threats
- Links to recently compromised sites with good reputations
- Links that are only active for a small window of time
Zero-Day Threat Identification
Identification of emerging threat patterns using data from millions of emails within the GreatHorn community — typically more quickly than traditional threat intelligence feeds
Community Threat Data
Community-sourced data on new and existing threats based both on automated collection and analysis of threat patterns and on proactive reports from GreatHorn Mailbox Intelligence
Threat Intelligence
Malicious URL and milicious file detection using both third-party and proprietary threat intelligence sources

DevOps Company Strengthens Security Resilience
“We’ve gone from an initial turnaround time of 48 hours at best to detect and respond to business email compromise to having instant alerts on our phones and desktops, catching the events in near real-time and preventing them from escalating. Using GreatHorn, we can now mitigate phishing attacks in five or so minutes.”
![[eBook] Things to Consider: Microsoft 365 + GreatHorn](https://www.greathorn.com/wp-content/uploads/2023/05/eBook-Microsoft-365-GreatHorn.png)
![[eBook] Things to Consider: Google Workspace + GreatHorn](https://www.greathorn.com/wp-content/uploads/2023/05/eBook-Google-WorkspaceGreatHorn.png)
![[Whitepaper] Measuring the Value of Email Security Solutions](https://www.greathorn.com/wp-content/uploads/2023/05/Whitepaper-Measuring-the-Value-of-Email-Security-Solutions.png)
![[Report] 2023 State of Email Security: Key Trends and Insights](https://www.greathorn.com/wp-content/uploads/2023/03/Report-2023-State-of-Email-Security.png)