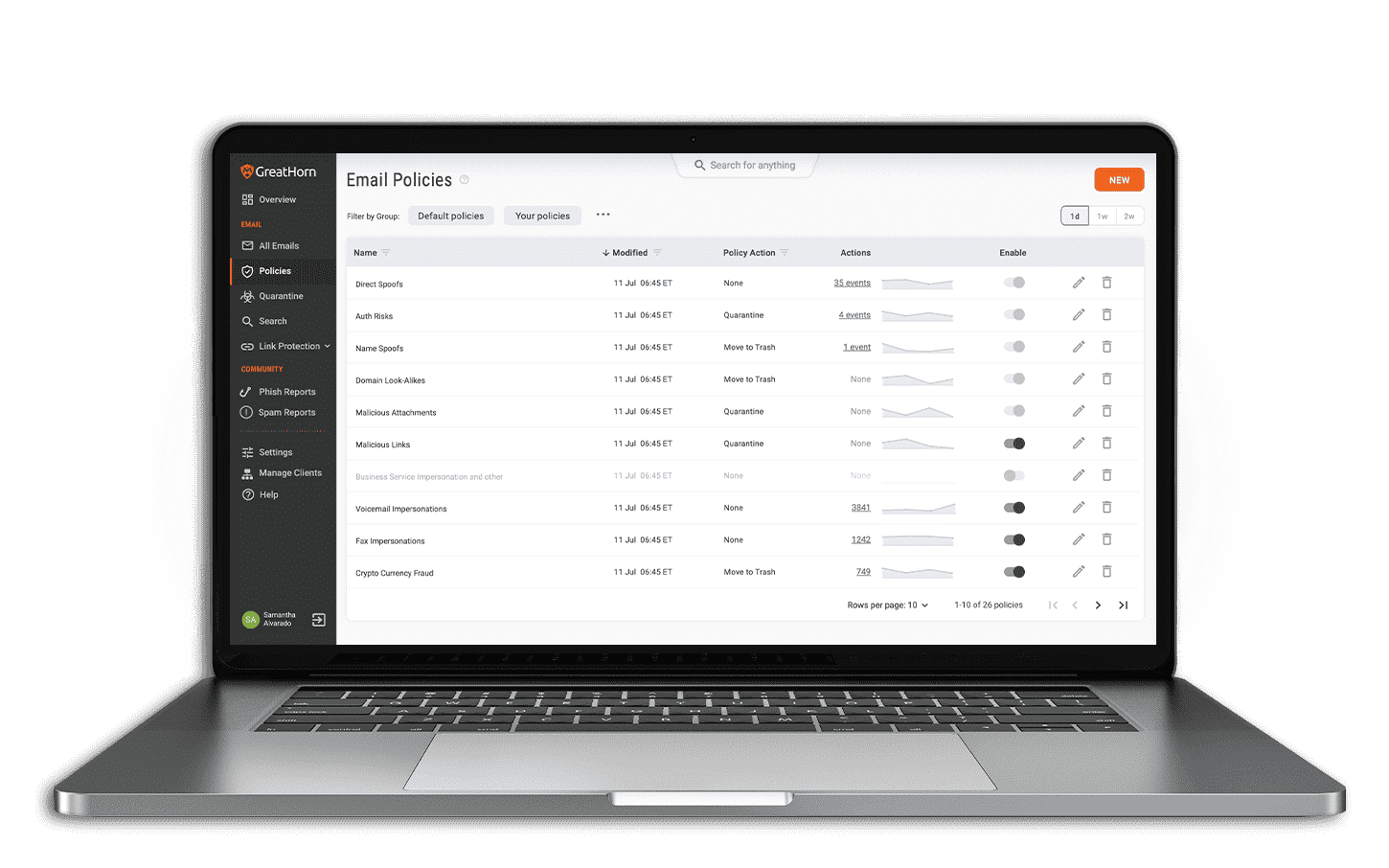
Safeguard your Employees from Credential Theft and Compromised Websites
Powerful Defense Against Today’s Most Dangerous Threats
The greatest dangers to your organization aren’t the attack websites added to an industry blacklist yesterday. They’re the ones that nobody has flagged as malicious yet. Unlike traditional blocking solutions, GreatHorn Link Protection integrates predictive analytics and multi-factor threat analysis with industry-leading threat intelligence to help you immediately detect credential theft and malicious website attacks.
Go Beyond Threat Detection
Initial Analysis
Compares against known malicious links and identifies suspicious ones.
Multi-Point in-Email Threat Protection
Contextual warnings, real-time alerting of threat, rewritten URLs.
Time of Click
Real-time link analysis, warning page, block page and time-of-click logging.
Incident Response
Full visibility into exposure, robust search engine, post-delivery removal.
Get Your FREE Email Threat Assessment
Learn what advanced threats are currently getting through your existing email security and into your end users’ mailboxes.
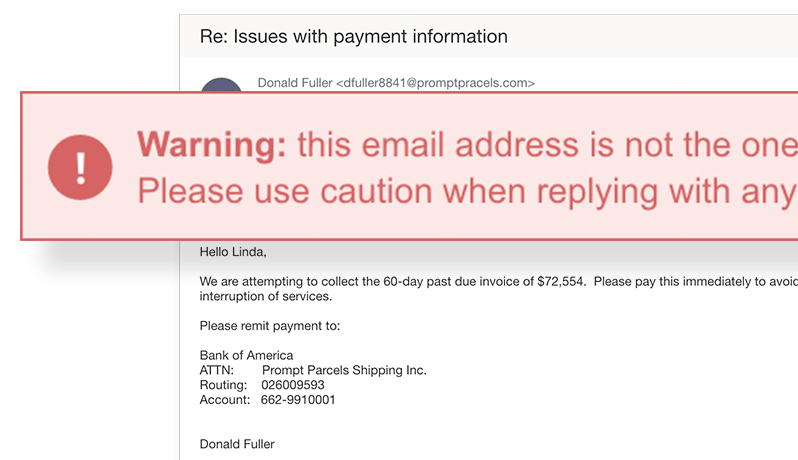
Beyond Malicious: Identify Suspicious Links
Not every malicious link announces its intent.
GreatHorn’s adaptive threat detection capabilities combine threat intelligence, advanced spoofing detection, and a deep understanding of your organization’s communication patterns to identify suspicious links as well as malicious ones.
Link Protection, Not Business Prevention
With GreatHorn’s turnkey link defense, you can rest assured that your employees have the context they need to make more informed decisions about the links they interact with. In the event a user was compromised, you have complete visibility into any users who interacted with an email, limiting the risk to the your entire organization.

“Do More Faster”
“Spend time in a Techstars office, and you’ll likely hear someone say, ‘Do More Faster’ – one of our favorite phrases. GreatHorn’s fully automated policy engine keeps us secure while allowing us to focus on delivering value to our companies, entrepreneurs, and communities.”
![[eBook] Things to Consider: Microsoft 365 + GreatHorn](https://www.greathorn.com/wp-content/uploads/2023/05/eBook-Microsoft-365-GreatHorn.png)
![[eBook] Things to Consider: Google Workspace + GreatHorn](https://www.greathorn.com/wp-content/uploads/2023/05/eBook-Google-WorkspaceGreatHorn.png)
![[Whitepaper] Measuring the Value of Email Security Solutions](https://www.greathorn.com/wp-content/uploads/2023/05/Whitepaper-Measuring-the-Value-of-Email-Security-Solutions.png)
![[Report] 2023 State of Email Security: Key Trends and Insights](https://www.greathorn.com/wp-content/uploads/2023/03/Report-2023-State-of-Email-Security.png)