Our global supply chain includes all the people, companies and countries that need to work cohesively to manufacture, process and ship goods. Disruptions in the global supply chain are increasingly impacting organizations, with logistical problems crossing most industries. As a result, the continued strain on the supply chain puts added pressure on businesses as they attempt to maintain revenue streams.
Attackers are accustomed to taking advantage of timely and relevant issues. Whether it’s vaccine notifications or tax deadlines, attackers understand the topics that have some form of emotional trigger, thus creating urgency when an end user is interacting with an email. And, when a user is caught off-guard, they are more likely to fall victim to the phishing attack. With the significant disruptions in the global supply chain, this makes a tempting target for attackers to use when developing the content to craft in their phishing attacks.
The GreatHorn Threat Intelligence Team have identified a 53% increase in shipment-related phishing attacks to organizations between the first half of 2021 through October 2021. In fact, there has been a 202% increase in use the term “Late Delivery” within the Subject Line and another 77% increase in the use of “Lost Package” within this type of phishing attacks. The GreatHorn Threat Intelligence Team has also seen an increase in the quantity of multi-touch phishing campaigns, whereby attackers send out an initial email informing the user that their shipment is late, and subsequently send an email with tracking information about their order being processed.
Examples of Attacks: Supply Chain and Shipping
This email appears to come from DHL Support, as shown in the Display Name below. It appears authentic in terms of DHL imagery, logo and overall structure of the body content. With the Subject Line positioned as a “Lost Package”, it further creates a sense of urgency for the user to find out more about the delivery that will be delayed. And, considering the 20% increase in lost packages, it’s no wonder why the use of this subject line is increasing in use by attackers.

Though the Domain Name of the Sender is not DHL-related, many users – regardless of security awareness training programs – still fall victim to email attacks that use legitimate-looking Display Names.
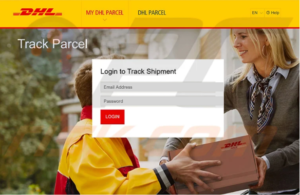
The Destination webpage also appears legitimate, requesting the user to log into the system.
A common trend used by attackers, as appears to have occurred in this attack, is to gain access to an authentic domain and create new pages to host malicious content. Because the hacked domain has been used by an entity for legitimate business purposes, the domains are not flagged by most email security vendors. In both of these examples, though the URL was malicious, it was not flagged within the native email platform controls prior to delivery to the end user, where they could fall victim to the attack.
The Malicious URL structure is: hxxp[://]origin-house[.]com/dullt[.]php?jgbbmca=ej&zcx=gs and hxxp[://]118[.]25[.]40[.]187/phpmyadmin/eightsh[.]php?hypowhhl=s&bolwowwx=du
DHL is a prominent shipping brand, and the company understands the importance of maintaining their brand integrity. In fact, they have a dedicated webpage on their website in an attempt assist users in reporting fraudulent emails.
For organizations looking to more effectively combat phishing attacks, a successful strategy always includes the combination of security awareness training and in-the-moment education for users to better understand the emails they’re interacting with at-the-moment a potential attack reaches their inbox. To better understand how to get a layered, defense-in-depth approach to email security, read this whitepaper.
Want to uncover if your organization is experiencing phishing attacks leveraging Google’s open redirects?
Try GreatHorn Risk-Free for 30 Days!

