Email Security Considerations for Google Workspace Users
Show the Value of Your Email Security Solutions: Don’t Just Measure Detection Rates
Universities and Colleges Face Multi-faceted Email Security Challenges
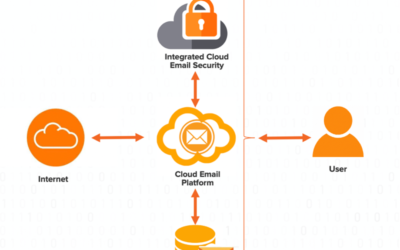
Native vs SEG vs ICES: What You Need to Know About Email Security
The shift from on-premise email platforms to cloud email platforms has taken shape, with the...
Microsoft 365: You’ve Migrated, So What Can You Optimize?
Over the years, Microsoft has made its cloud offerings more attractive, motivating more and more...
How Email Security Can Align to the MITRE ATT&CK Framework
In our previous post, What is the MITRE ATT&CK Matrix, we explained what the matrix is and how...
What is the MITRE ATT&CK Framework?
The MITRE ATT&CK Framework is a complete knowledgebase of tactics and techniques cyber...
Can We Continue to Function Without Facts?
In today’s world, disinformation is common, skewing reality from fiction. It’s a place where...
How to Balance Productivity and Security in Your Email Environment
[Ask Me Anything Wrap-Up] On September 16, 2020, GreatHorn’s CEO, Kevin O’Brien, moderated an...