Many organizations, across many supply chains, use Amazon’s Simple Email Service as an inexpensive and high-scale cloud email service provider.
Now, cybercriminals are using return-path features provided by this popular service in order to quickly and effectively bypass traditional email security checks. It’s not easy at first blush to distinguish between legitimate uses of these URLs and non-legitimate uses.
In February alone, the GreatHorn Threat Intelligence Team identified BEC (business email compromise) attacks numbering in the millions, using amazonses.com return paths. Many of these email attacks targeted security professionals within large organizations, where these types of return paths are commonly received in authentic emails. These attack emails were sent to organizations, bypassing native email platform providers’ security checks, and made their way into users’ inboxes.
How return-path works
Organizations that send mass emails use return paths to process bounced messages. When an outbound message bounces, instead of clogging the sender’s inbox, the bounced-message reply goes to a return-path address. This is an SMTP address, distinct from the sending address, used specifically to handle bounced messages.
Amazon Simple Email Service return path addresses include:
- “eu-west-1.amazonses.com”
- “amazonses.com”
- “us-west-2.amazonses.com”
Example attacks
Here is an example of a phishing attack identified by the GreatHorn Threat Intelligence Team. In this BEC attack, the cybercriminal is attempting to harvest credentials to takeover the account of this user.
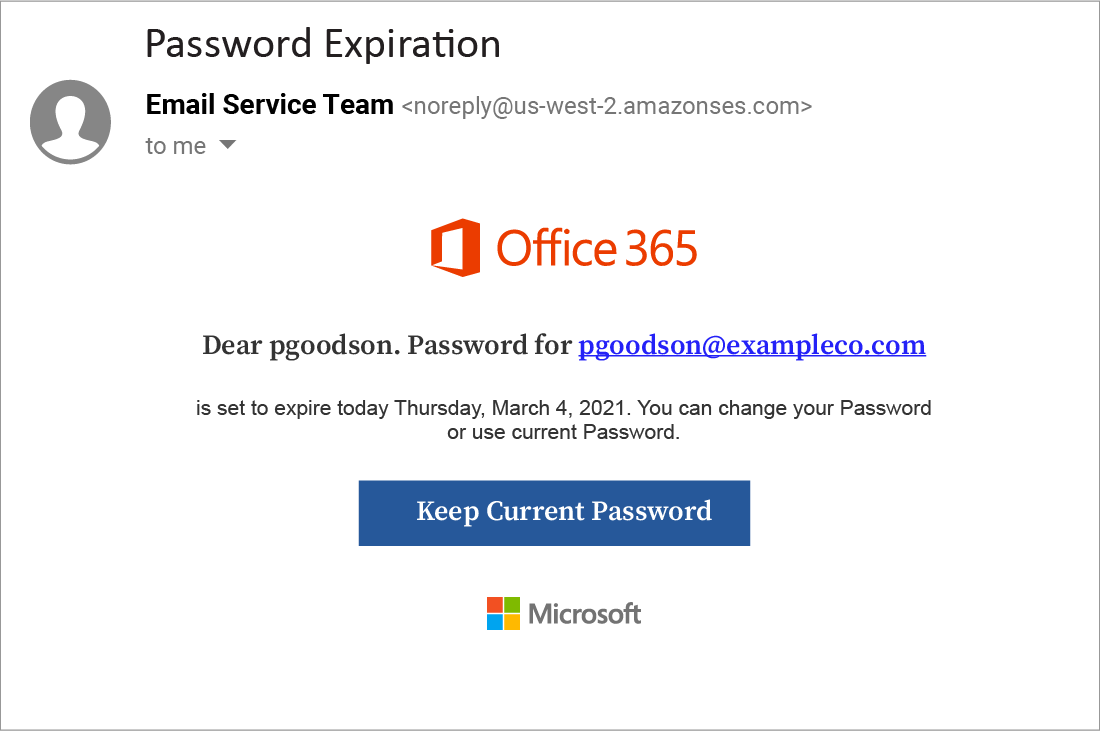
This specific phishing attempt impersonates a voicemail service, informing the recipient that they have a voice message. It emulates the appearance and behavior of many email platforms that use cloud-based voicemail services.
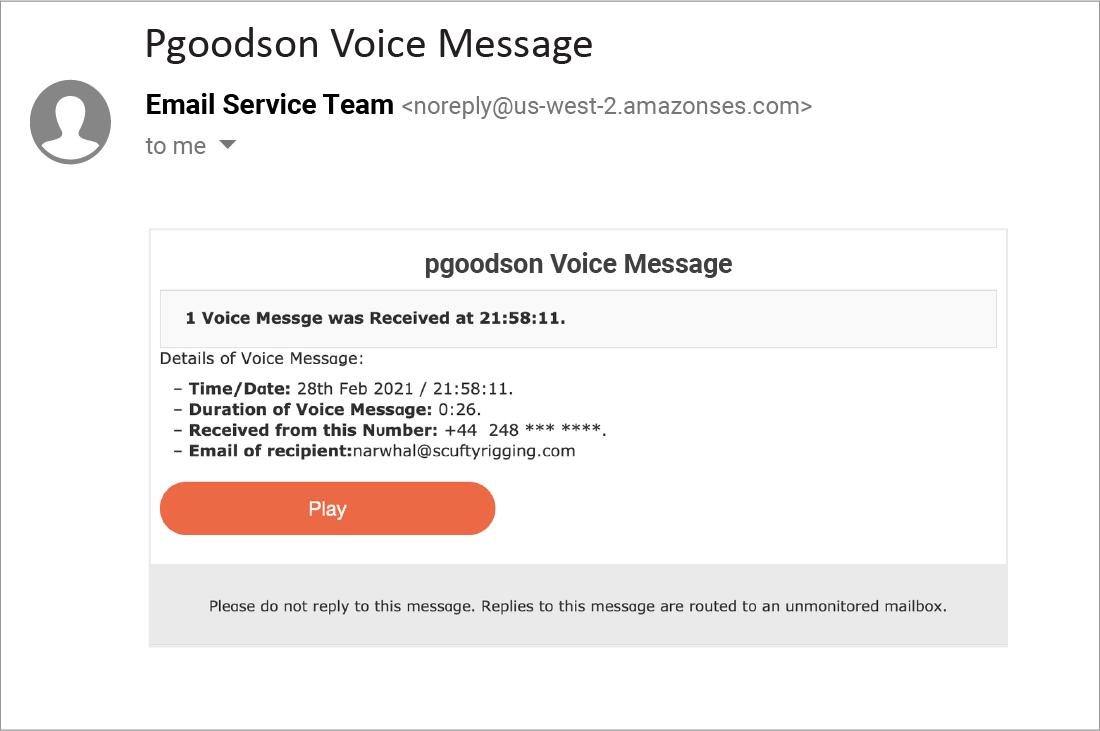
If the recipient continues, they will come to a landing page that is nearly identical to a Microsoft Office login page. The recipient’s email address is already entered, and they are prompted to hit “next.”
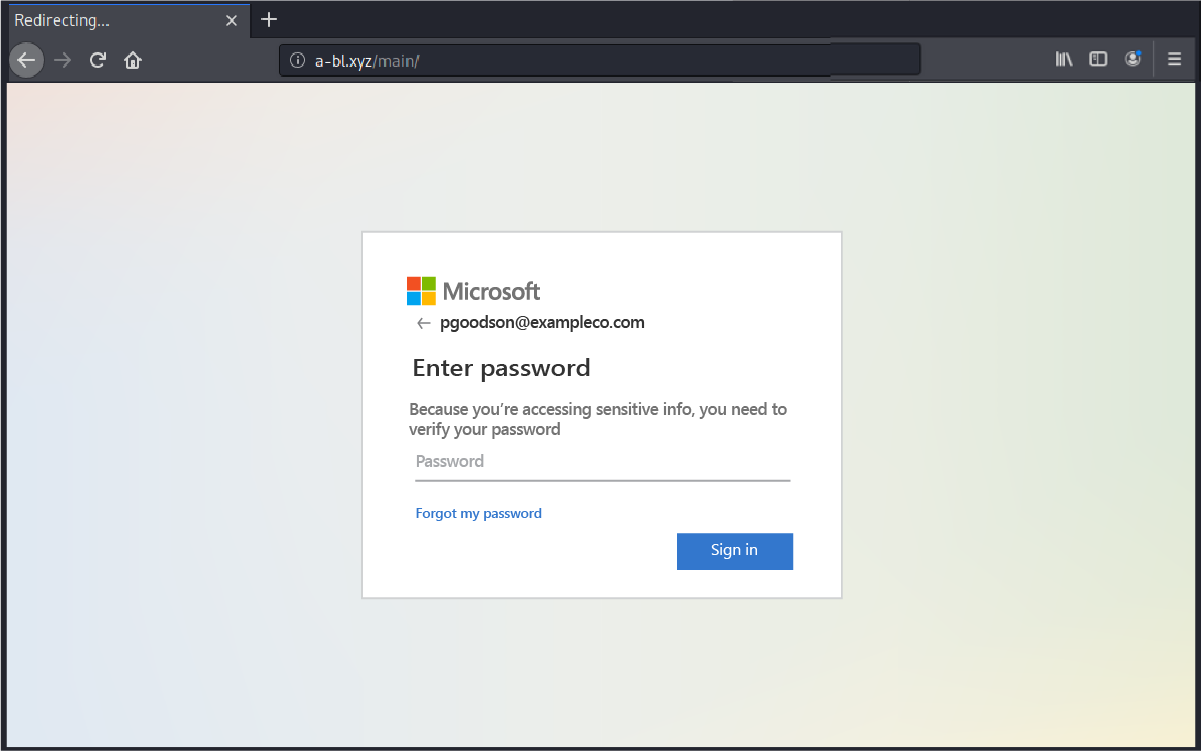
If the user’s email is autopopulated into the destination URL, where only the password is required. As a result, the user will be providing scammers with their login credentials. The attackers can then gain access to the recipient’s email contact lists and other sensitive data, including cloud storage.
How to prevent return-path attacks
Organizations rely on return-path. They are an essential tool in communicating with customers and prospects. An organization would be unable to block ALL email from these senders. However, organizations can do a lot more to detect and protect users from attacks that make use of return-path addresses, by using additional data to establish when an email is suspicious. For example:
- Relationship Strength: GreatHorn measures the strength of a sender’s individual relationship to the recipient, as well as a “friends of friends” system that accounts for the sender’s overall relationship with others in the recipient’s organization.
- Spoofing Likelihood: GreatHorn analyzes each email for phishing attacks that hide behind legitimate-looking identities. These include employee display-name spoofs, domain spoofs and domain look-alikes – including comparison against known email addresses, executive impersonation tactics and email authentication standards.
- Content Analysis: GreatHorn performs deep content inspection based on keywords, regular expressions (RegEx), attachments and URLs. These inspections identify common spear phishing tactics (like wire transfer and W2 requests), credential theft attacks and business service impersonations – all without storing the content or the mail.
- Communication Patterns: Over time, GreatHorn establishes an understanding of communication patterns unique to a specific individual and a specific organization, such as email frequency, volume, recipients and sending patterns. Anomalies in these patterns are combined with other data to gauge the likelihood of a threat.
Learn more about how GreatHorn allows you to safely use the email services your organization relies on, by layering intelligent email security on top of existing service platforms.




