Times of change are also times of opportunity. This is true for most businesses, and it is also true for cyber criminals.
We’ve written previously about how the good habits built up by people in your organization–opening urgent-seeming attachments, responding quickly with information requested by a supervisor–can turn into liabilities when an attacker puts them to work within an email phishing scam.
The same is true of times when habits are disrupted. With COVID-19 changing the way we work, we see organizations trying new and unfamiliar technology platforms to meet emerging needs. Individuals, too, look for solutions on their own, even if it’s not the best or the most secure. Management must distribute new instructions and protocols for new ways to behave, and these communications, too, are vulnerable to interception and attack.
Cyber criminals have been quick to try to exploit this time of change, with email phishing attacks aimed specifically at COVID-19-related situations. As work that formerly took place in a central location moved to a distributed network of people working remotely, GreatHorn tracked the number of COVID-19-related email phishing attacks. As you can see from the chart below, attackers did not waste time, quickly getting into email inboxes with millions of attacks.
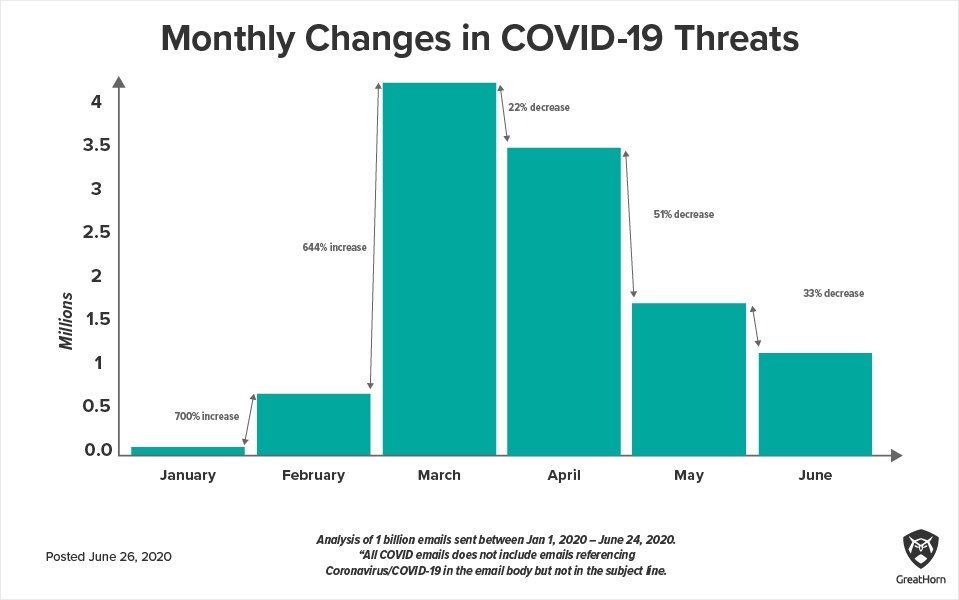
As people adjusted to working from home, these attacks became less successful, and attackers adjusted their strategies: note how rapidly the number of COVID-19 phishing emails declined from April to May, as working remotely became a new normal that people had adjusted to.
Now, change is in the air, again. Many organizations are bringing workers back into their offices and other facilities. Managers are communicating about new protocols and employees are looking for guidance. GreatHorn is seeing a new surge of COVID-19-related phishing attacks that seek to exploit this situation.
In particular, GreatHorn has identified prominent phishing attacks with the subject line, “Mandatory Covid-19 Assessment for Employees.” These COVID-19 phishing attack emails attempt to get users to click on a link to the same malicious URL: https:/\afzan.co/wp-content/themes/1/1.
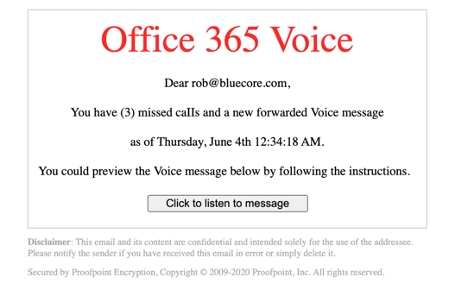
However, this same malicious URL was used in subsequent phishing attacks where attackers hide in a fake voicemail alert, which we’ve reproduced below. The “click to listen to message” button actually points to the malicious website, served from a compromised computer located in the UK.
Cyber criminals often reuse elements of a phishing campaigns for subsequent attacks. It’s vital for organizations to detect and remediate phishing attacks as quickly as possible to minimize the impact. We often see IT professionals taking the first step to develop policies on specific phishing campaigns, but fail to take a more proactive stance by further refining policies to protect their end users based on the variables detected. In this instance, IT professionals should leverage the capabilities within their email security platform to search for any emails with the malicious URL, not just the specific phishing campaign itself. This would remove all phishing emails associated with these related campaigns.
With so much extra stress and uncertainty already on people’s minds, how can an organization prevent its users from clicking on these malicious links? There are three things you can do:
- Mass remediate and create email security policies in real-time: Once you detect phishing attacks, identify and remove the emails across your organization. It’s also important to develop a policy to mitigate subsequent attacks as well.
- Investigate and detect similar phishing attacks in real-time: Search your organization’s emails beyond the initially detected phishing attacks based on the malicious variables (e.g. domains, sender, etc) to mass remediate and further refine email security policies.
- Understand the context that is specific to the user and organization: Is the name someone who the user has communicated with, before? If it is, do the email address and email domain match those prior communications? If not, the message should be treated with suspicion. If the meta-data in a message doesn’t match normal correspondence, it may not be legitimate.
Email phishing attackers are looking to gain access and do damage to sensitive systems inside your company. By using COVID-19 related messages, they’re trying to exploit your employees at a time when they are most vulnerable. When you are tracking the context around those messages and educating your users in real-time about suspicious content, you are turning those users from vulnerable targets into valuable protectors of sensitive data and systems.



