GMX (Global Mail eXchange) Mail is an email service where users may register up to 10 individual email addresses at no cost. As a result, threat actors are leveraging this service to easily spin up new email addresses and effectively delivering phishing attacks that bypass Microsoft o365 and Google Workspace, landing in an organization’s email environment.
This type of free email service is difficult for organizations to defend against. Because many organizations have legitimate reasons to communicate with personal email domains, like Gmail, attackers take advantage of this security loophole and use the same personal email domains. In fact, approximately 1% of all mail delivered to an organization is received from personal email addresses.
In recent months, attacks specifically being delivered to organizations from the GMX.net domain have increased from May 2022 to July 2022 by 768%, then from July 2022 to September 2022 by an additional 103%. This increase is often a result of the success attackers are experiencing by users taking action on their emails after they were delivered to inboxes.
In the most recent phishing attacks from GMX.net domains, the recipient appears to receive an email from a delivery services, such as FedEx (as depicted in the email below). As is common by attackers, the use of well-known brands are being impersonated and visual appear authentic. In fact, 6 brands are responsible for 92.8% of all brand impersonation attacks in 2022, including FedEx, Docusign, DropBox, Amazon, Zoom and WeTransfer.
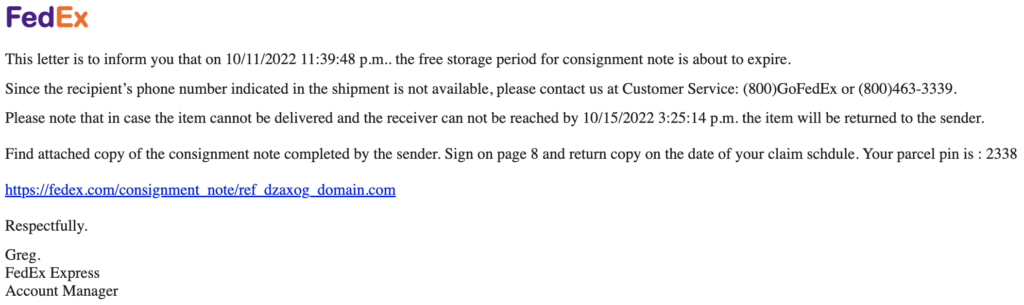
The displayed link text within the email appears as a secure (https://) connection, followed by a FedEx. com domain. Creating urgency, the threat actor is requesting the user claim the shipment, stating a “phone number was not indicated in the shipment.” As is common by attackers, using a Google Drive link underneath the display link, allows the links to bypass native Microsoft o365 and Google Workspace protections and land in the email environment, creating risk to the organization.
If the user is tricked into clicking on the link, the destination page (https://drive.google.com/uc?id=1) in Google Drive automatically downloads a Zip file onto the user’s machine. Contained within the Zip file, disguised as a “Print_Label”, is a malicious batch file, as displayed below.
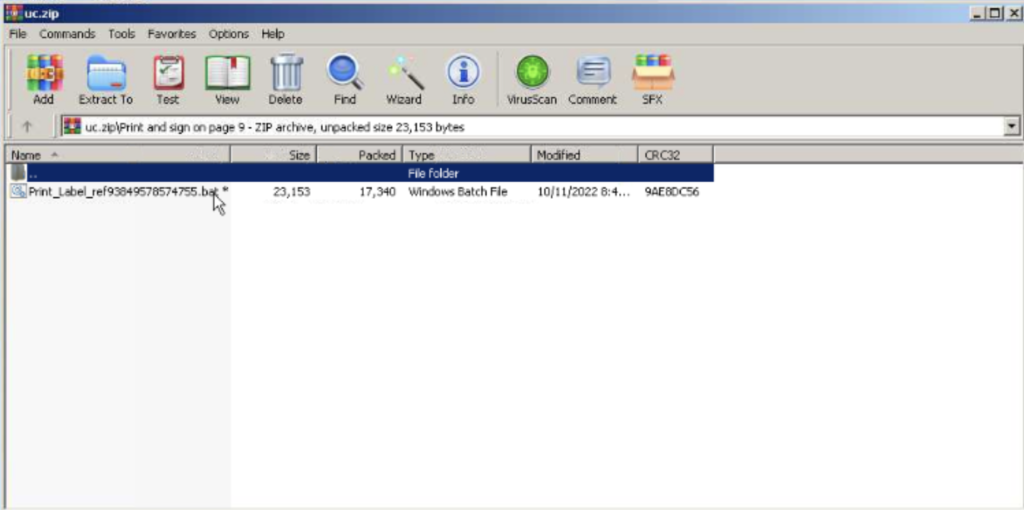
Though a link is represented in 88% of these types of attacks from the GMX.Net domain, 12% of attacks contain only the attachment with the zip file itself. What’s most concerning is that the malicious link and the malicious attachment are both bypassing the native security controls within Microsoft and Google and landing in an organization’s environment.
How organizations manage communication between their users and free email services is a frequent concern to organizations. These email domains are most used to spoof known brands and impersonate executives within the organization. When determining how best to manage the risk associated with these types of domains, it’s critical to have technology that not only provides advanced machine learning to analyze emails across the entire email envelope, but also provide users with layers of protection – all in an effort to inform user and prevent them from taking action in the moment they interact with an email.
Want to uncover if your organization is experiencing phishing attacks leveraging the GMX.Net domain?
Schedule your email security demo today!

