Cybercriminals are always sharpening and improving their malicious techniques. And organizations and continuously evaluating email security solutions to improve their ability to detect and mitigate risk from phishing attacks. According to Gartner’s 2020 Market Guide for Email Security, “Dramatic increases in the volume and success of phishing attacks and migration to cloud email require a reevaluation of email security controls and processes. Security and risk management leaders must ensure that their existing solution remains appropriate for the changing landscape.”
With this in mind, The Tolly Group, a global provider of third-party validation services for IT companies, was commissioned to undertake a head-to-head comparison for us against a competing product, Proofpoint Essentials.
You can read the full report here. Below is a summary.
Overall Comparison
Overall, and in specific areas, Tolly found GreatHorn’s efforts constantly improving, and maintains a leading offering in the email phishing security space. Their tests found that GreatHorn’s product “provides significant email security functionality not found in Proofpoint, while also being easy to use.”
Areas where GreatHorn provides functionality not present in Proofpoint Essentials include:
- Sophisticated relationship analytics
- Account takeover protection
- Impersonation detection
In features where both solutions overlap, GreatHorn frequently provides implementations that are both more feature-rich, and more robust.
Ease of Use
The comparison testing found GreatHorn’s system to be “demonstrably easy to navigate.” Proofpoint’s system is similarly constructed, but was found to lack several of the features that, in GreatHorn’s system, make it easy for the user to perform core functions like setting up policies, inspecting quarantined messages, remediation and search.
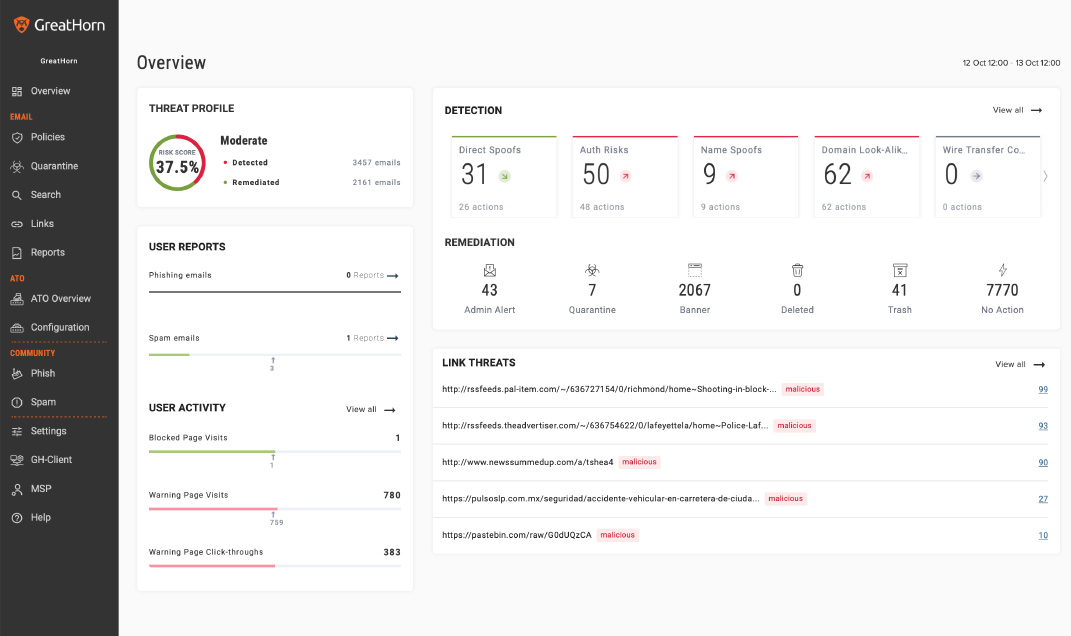
- Summary graphics and data provided on the GreatHorn dashboard provide single-click drill-downs. For example, a count of spam messages leads via a single click into a drill-down into the problem messages. On Proofpoint, only Log Search and Emergency Inbox are available via single click. Other functions are behind a drop-down menu.
- The GreatHorn dashboard is compact, making all core functions available in a single screen. Tests found the Proofpoint dashboard requires scrolling down 2.5 screens to see all data.
Policy Definition
The ability to set policies that the system uses to identify and handle problem messages is a core function of any email security system.
- GreatHorn takes a universal approach to policy definition, providing a single policy creation screen where policies can be defined to protect users against an email attack in all its dimensions, including URLs, sender domains and message content.
- Proofpoint provides similar functionality, but core functions are divided into four separate screens or areas of the dashboard: Spam policies are set in the “SPAM Settings” screen; policies related to malicious URLs are set on the “URL Defense” settings screen; sender address filters are applied on the “Sender Lists” screen; and finally, a “Filter Policies” screen is provided for managing filters based on message content.
Default Policies
In order to get up and running quickly, without having expertise in a given system, default policies provide the foundation to build upon for an organization.
- GreatHorn provides more than 24 default policies. These cannot be deleted, but some parameters can be modified.
- Proofpoint does not provide any named default policies that are visible to the admin.
Policy Granularity
The more “granular,” or flexible, an email security policy is, the more sophisticated it can be.
- The Tolly Group found GreatHorn’s policy granularity to be “dramatically more sophisticated” than that of Proofpoint. Specifically, GreatHorn provides message policy controls in the following areas:
- Sender
- Relationship analysis
- Risk analysis
- Payload content and characteristics
- Keywords and/or patterns found in the message
Policy Defintion Options: Sender (From) Option Description GreatHorn Proofpoint Specific Addresses Specific user(s) Yes Yes Except Specific Addresses Exception for specific sender(s) Yes Not specified Specific Display Name Sender Name(s): can be exact text, contains text or Regex Yes Not specified External Return-Path Domains Yes Not specified Specific Return-Path Domains Defined via text or Regex Yes Not specified From Internal Addresses Options for selecting by "from" address characteristics. Each option can be chosen separately. Yes Not specified From External Addresses Yes Not specified With Internal Reply-to Addresses Yes Not specified With External Reply-to Addresses Yes Proofpoint allows a "Sender Address" to be specified. When selected, this presents the admin with an empty box with no specifications or context-sensitive help to provide information on what is allowed. Email Headers Classify By Header Select common headers or generate custom header profile Yes Yes (If contains any, all none) Specific IP Address Range Yes Can select country of client IP only
- Proofpoint’s filter policies were “more challenging to configure and maintain,” the tests found. While GreatHorn provides a single screen for policy configuration, Proofpoint required complex navigation, through multiple drop-down menus of hard-coded document types. This complexity introduced risk of human error, including the potential for policies that are actually logically impossible.
- Relationship analysis and risk analysis are missing from Proofpoint’s list of available criteria, the testers found.
Account Takeover Protection (ATO)
This feature, which uses biometrics for multi-factor authentication, is unique to GreatHorn. ATO uses the unique typing pattern of the user as a means to confirm identity. In a situation where a user password has been compromised, ATO can detect the unauthorized user and require biometric authentication at message send time.
Link Sandboxing
Link sandboxing addresses the time delay between the moment a malicious link is delivered to the moment it is clicked. In the intervening minutes, hours or days, a legitimate URL could turn malicious. Link sandboxing addresses this threat by checking a link at each point.
- GreatHorn offers sandboxing. Proofpoint Essentials does not, however sandboxing is available at the Proofpoint “Advanced” or “Pro” subscription levels, according to The Tolly Group’s report.
Security Event Analysis
Finding Events
The testing team from The Tolly Group looked into how easy it is for admins to discover information about a particular security event, once a policy is triggered and that event is generated and logged in the system.
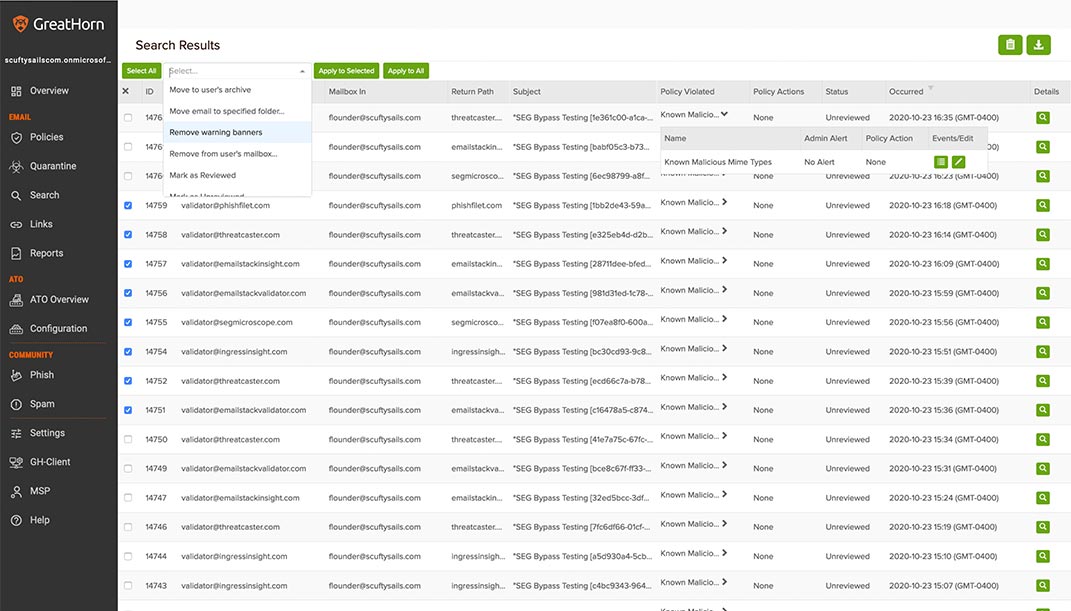
- GreatHorn makes this kind of discovery a one-click experience from its main dashboard, testers found. They highlighted three paths to more information on security events:
- Policies: The Policies view shows the number of times a policy was triggered over a time period. One more click on the event history total for a given policy shows all emails that triggered the policy.
- Quarantine: The Quarantine view opens a list of all messages that have been quarantined.
- Search: Allows flexible search for messages with any combination of criteria.
- In Proofpoint, The Tolly Group testers did not find a method to search all messages that triggered a particular policy. Proofpoint’s Log Search by default includes spam and clean messages, up to the most recent 1,000 messages matching the search criteria. A search for quarantined messages also includes spam mixed in with quarantined malicious messages.
Analyzing Events
To design effective email security policies, admins need to understand the kind of threats that are emerging. To achieve this understanding, they need to be able to see detailed information on each threat event.
- The Tolly Group found GreatHorn’s event analysis screens provide visibility into threat events at the same level of granularity as its policy options.
- For each field of a message that triggers a security event, GreatHorn provides detailed information, including reference to standard email security resources such as SPF, DKIM and DMARC. GreatHorn also uniquely provides analytics covering the prior relationship between user and sender, the testers found.
- Proofpoint lacks any method to retrieve messages that trigger a specific policy, according to The Tolly Group. Only by drilling down to the message level can an admin discover the conditions that caused the message to trigger an event. This information is limited: The name of the relevant filter is not listed; there is minimal threat information surrounding the message.
- Finally, testers found Proofpoint admins were able to view the entire contents of a specific message, without that action being logged. This introduces an internal privacy and security vulnerability that is addressed in GreatHorn. Should an admin attempt to open the contents of a message, they will see a warning that the action will be logged.
Remediation
Similar remediation actions are offered by both GreatHorn and Proofpoint, the testers found, including releasing from quarantine, resending (for outbound messages, classifying as spam or clean, reporting as false positive or false negative, and hiding the email from logs. Both allow individual and bulk remediation actions, applying an action to the entire group of messages returned from a search, or a single message.
Conclusion
The Tolly Group’s head-to-head comparison between GreatHorn and Proofpoint Essentials confirmed that GreatHorn’s approach to detecting and remediating phishing attacks is effective. As recommended by Gartner, “address gaps in the advanced threat defense capabilities of an incumbent secure email gateway (SEG) by either replacing them or supplementing them with complementary capabilities via API integration.”
Learn more about how GreatHorn’s machine vision and artificial intelligence technologies identify credential theft attempts and keep your users safe.