Bad actors around the globe go phishing in emails twenty-four hours a day, seven days a week. Whether they are “guppies” like your local bakery down the street or big “fish” like Google, no one is immune to their attacks. Google, one of the largest, most well-known – and used – applications, will always be a top target by attackers attempting to impersonate its users. In fact, Google Workplace accounts for 19.2% of the native email environments running within organizations. Yet, even with their market share and world class investment in communication and collaboration tools, the ability to protect organizations and users alike still struggles to match up against sophisticated phishing attacks.
Hook, Line, and Almost Sinker: A Real-Life Attack
One of our clients was almost a victim of a phishing expedition. To show you how these bad actors operate, we are providing you with the details of a recent impersonation attack that bypassed Google’s native email security controls.
To start, the email sent to users had the subject line “Critical security alert for [NAME].” (It leveraged the personalization tokens that improve the credibility of the email being opened by a user.) The user saw the Display Name “Gmail Account”, though the underlying email address for the sender was “[email protected].” This sender address is designed for Microsoft customers to develop and email surveys intended to go to customers. However, attackers now utilize the capabilities to effectively target users and embed links to malicious sites.
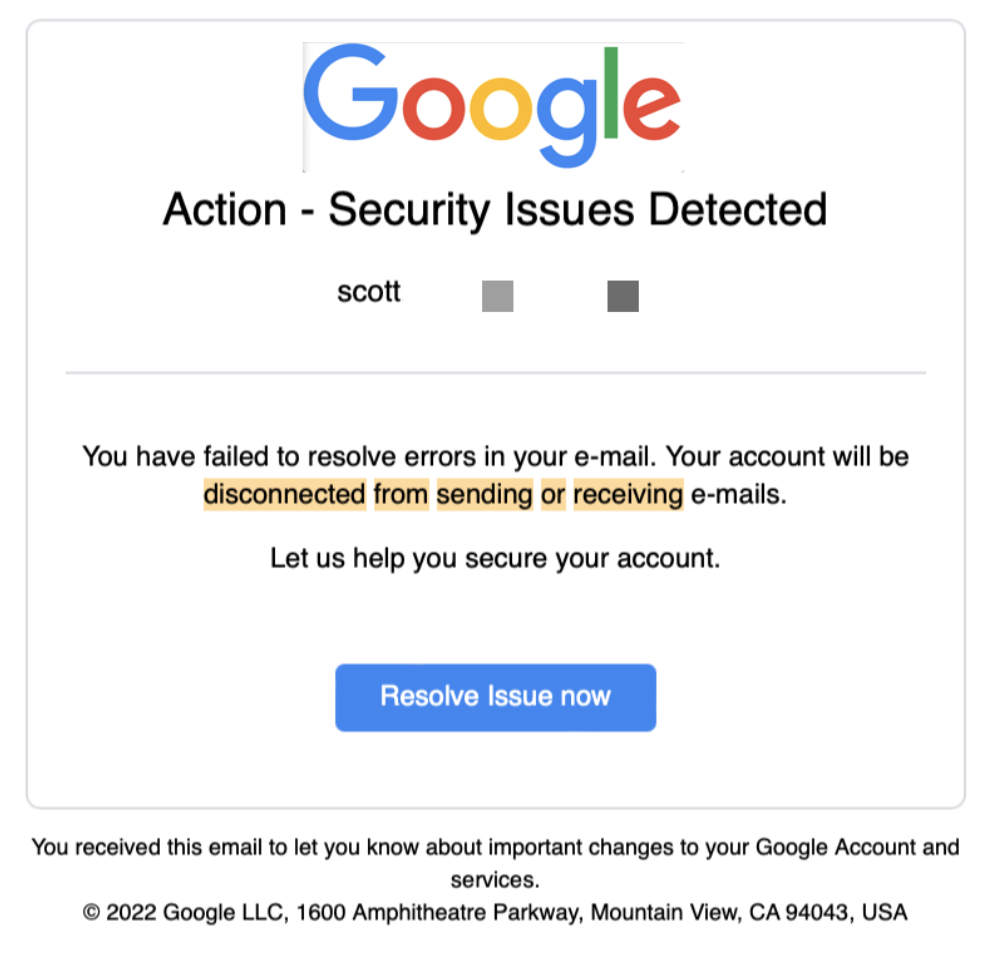
The link embedded within this specific email was meant to trick users into thinking it was an authentic Google domain. By transposing the “i” in “gmail” into a “1”, it gave the appearance of the intended impersonation.
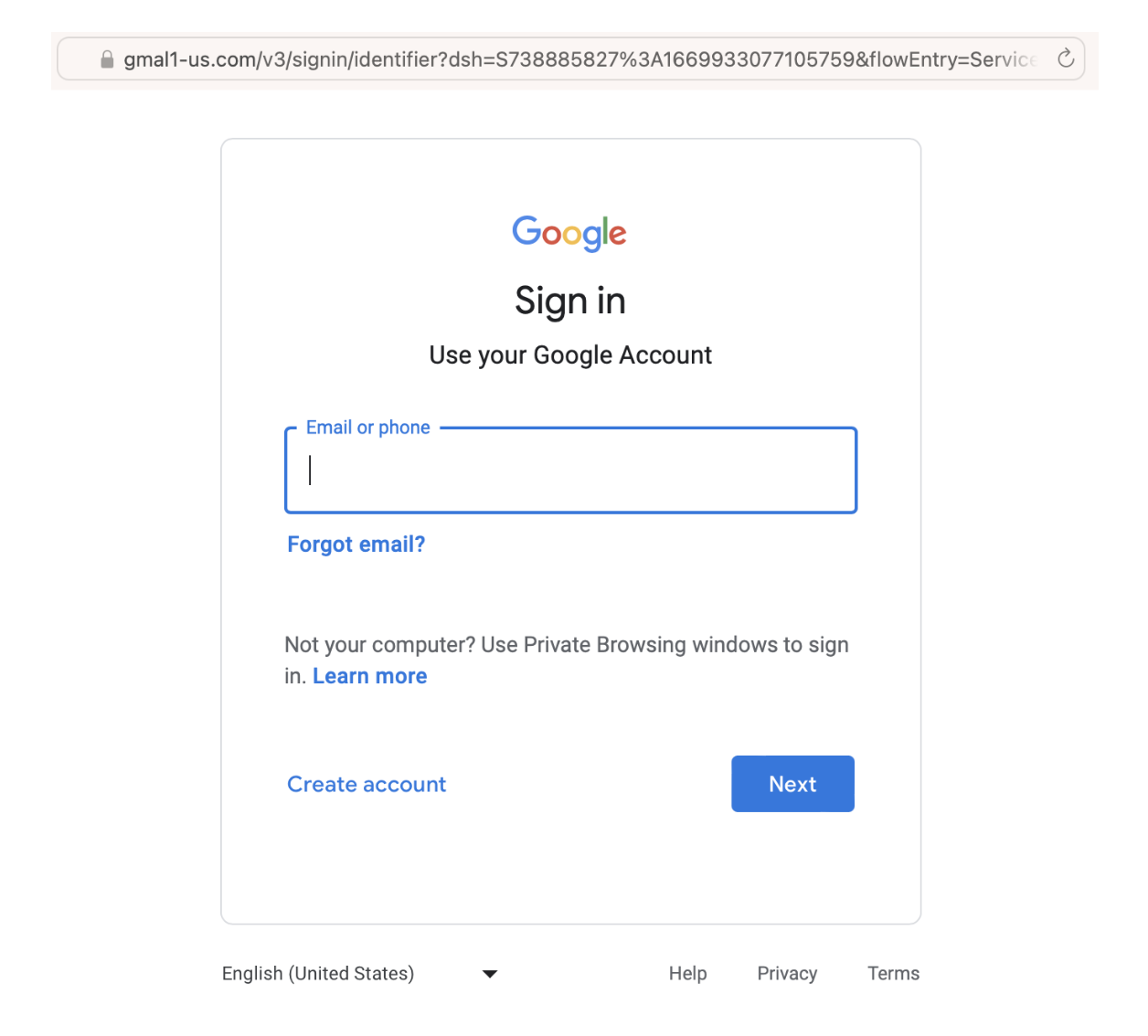
When the user clicked on the malicious link for https://us-gma1l.com/?gmail hidden under the “Resolve Issue Now” button within the email, they were redirected to the following “Google Sign in” page. It is here that they would unknowingly be providing their login credentials to the attacker, allowing them to perform an account takeover.
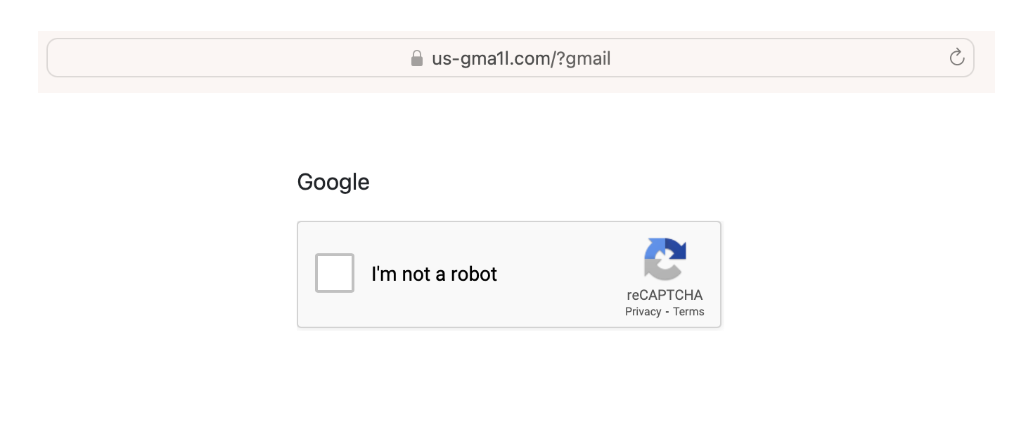
Once credentials are submitted, a Captcha is also incorporated into the attack, giving more credibility to the end user that this is an authentic Google page.
Catching the “Phish” Before the Attack
Thankfully, GreatHorn was able to prevent this attack before it happened. As you can see in the below dashboard for this individual email, the metadata clearly indicates the anomalous characteristics used to detect this type of Google impersonation attack.
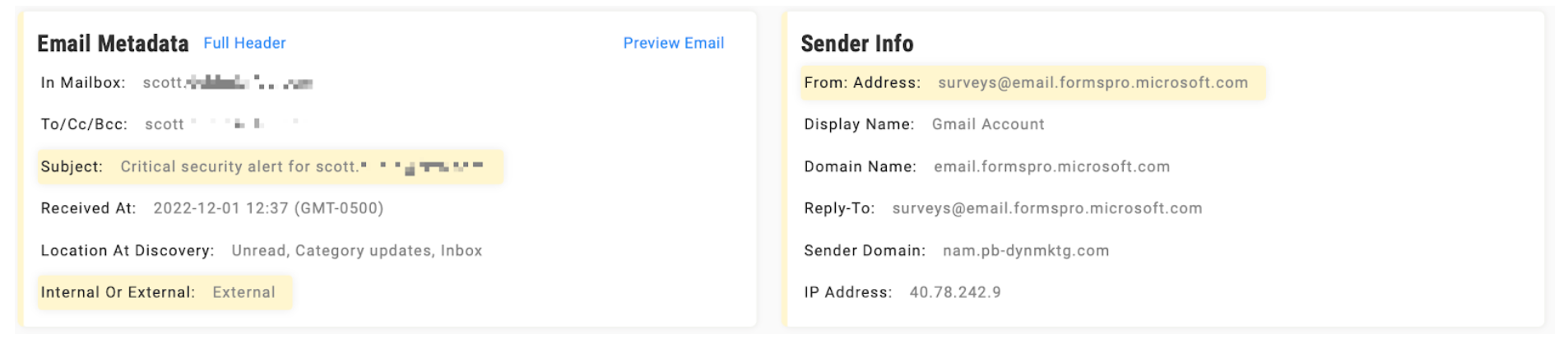
These types of attacks should be automatically quarantined based on industry best practices.
If an organization legitimately receives emails with the address @email.formsproo.microsoft.com and wishes to permit these messages into their users’ inboxes, there are ways to remain secure. We highly recommend leveraging customized banners to caution users about the risk associated with @email.formsproo.microsoft.com. By incorporating an additional layer of link protection warning users of credential harvesting’s potential on the destination site, users will reduce their interaction with these types of malicious emails.
If GreatHorn hadn’t taken action to protect and remove the message first, it would have landed in a user’s inbox. That unsuspecting user could have taken their employer on a phishing expedition no one signed up for or wanted. Google provides its users with a great first line of defense. But when bad actors cross that line, vigilance and preparation are what’s needed to prevent those inevitable attacks from moving any further.
Looking to strengthen your “phishing” lines of defense?
Contact us to learn more about GreatHorn’s Email Security Platform today.

