Over the past few weeks, a tremendous number of changes have taken place around the world. For many, Zoom conferences have become a primary means of staying in touch with colleagues, prospects, and customers. Even school systems around the world are relying on Zoom for ensuring that students can still attend classes and partake in distance learning.
However, as with any new technology, there are new risks to contend with. In a recent Boston Globe article, journalists noted that given the relatively simple URL schema that Zoom uses (a ten-digit, randomly generated number) and a permissive set of defaults that reduce friction for meeting attendees, it’s possible for unauthorized attendees to join meetings, either disrupting them or stealing sensitive data.
Settings to Secure Zoom
Zoom Security settings can be set by both users and admins. On the user level, individuals can set their own security parameters. If an administrator makes changes under Admin Settings, they will apply globally to all users.
Zoom User Security Settings:
Log in to account, click Settings, and navigate to the Meeting tab.
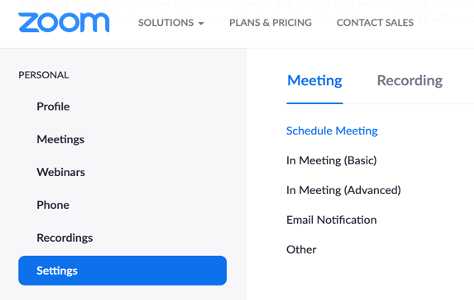
Zoom Admin Security Settings:
Log in to account. Under Admin, select Account Management, Account Settings, then click the Meeting tab.
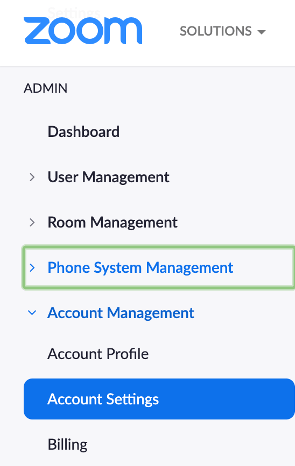
The following settings are recommended to be turned On:
- Require a password when scheduling new meetings

- Require a password for Personal Meeting ID (PMI)
- All meetings using PM

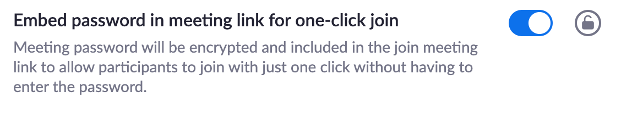
- Embed password in meeting link for one-click join
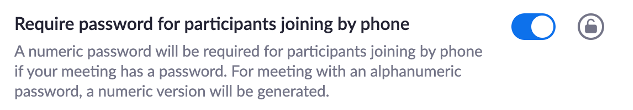
- Require password for participants joining by phone
- Screen Sharing
- Host Only
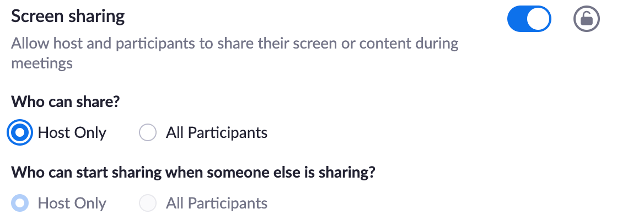
- Identify guest participants in the meeting/webinar

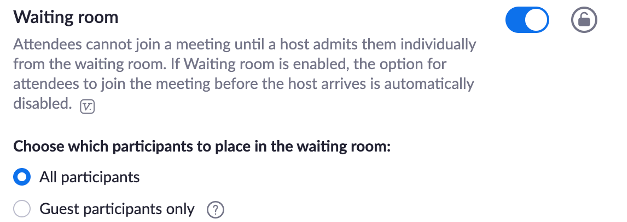
- Waiting room
- Guest participants only – this will mean that your co-workers are not required to go through the “waiting room” before joining, but outside attendees will
The following settings are recommended to be turned OFF:
- File transfer

From the Admin area, you can also click on the Lock icons to lock each setting. This locks those settings from being able to be changed at the user level.

Using GreatHorn to Detect and Stop Zoom Impersonation Attacks
When it comes to spotting these attacks in the wild, your basic email security training skills still apply. Make sure you are checking the actual sending address on inbound emails, especially if their Display Name appears to be Zoom.
Pay extra attention to spelling mistakes in domain names and mentions of Zoom in subject lines trying to grab your attention. Malicious emails try to entice the recipient with a compelling call-to-action, such as resetting a password or validating an account or subscription. Ensure that you are not downloading attachments or clicking on links without validating the sender. GreatHorn provides contextual analysis on your emailing relationship with the sending address, which helps hone in on first-time senders trying to impersonate your friends or colleagues. Combine relationship scoring with Zoom keyword detection and suspicious link identification to surface Zoom impersonation attacks in your tenant today.





