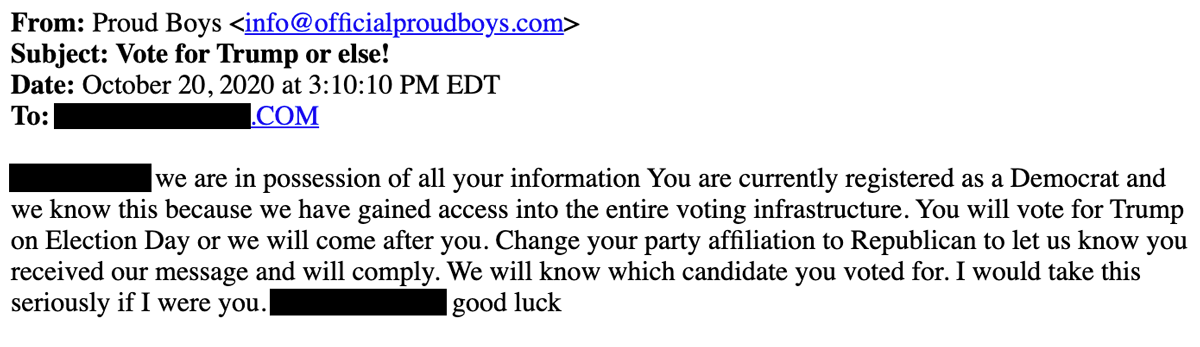
The entire population is talking about the threatening email campaign that reached American voters over the past 72 hours. Last night, Director of National Intelligence (DNI) John Ratcliffe attributed this email campaign to Iran, Russia interference with the 2020 election.
As threat researchers, we have three questions:
- What data do we have to support this conclusion?
- Is it accurate?
- What might have happened?
Email is the communication method. First, we need to look at what facts we have about the emails themselves. DMARC, SPF, and DKIM are authentication technologies that verify the sender’s identity for an email message. Only SPF exists for officialproudboys.com, as a DNS TXT record set to reject all mail that failed to pass the SPF check, but with no valid senders defined. In other words, no mail sent from this domain would ever be appropriately validated.
Next, we looked for an MX record (mail exchanger record), which specifies the mail server responsible for accepting email messages on behalf of the domain. There is no MX record for officialproudboys.com, which is more understandable when one sees that its registrar dropped the officialproudboys.com domain in 2017. Images of the old site are available via the Wayback Machine. Still, the domain is essentially being “squatted on” by an anonymous owner, presumably, the same owner as whoever held it when the site was live.
Why are we talking about this? Without MX record information, anyone could – right now – send an email claiming to be [email protected]. There is no actual email sender [email protected] because there is no officialproudboys.com, nor has there been since 2017.
Without actual email sender information, it becomes challenging for anyone to imagine how to attribute those messages. Rewriting the “From” address is trivial and quickly done via almost any email system. Since no mail authentication records exist at the domain level, literally anyone could send an email from [email protected].
These messages can be sent from anywhere, from any compromised email account or any legitimate email account anywhere in the world. The only source information that would be available would be the originating IP address, which is also easily spoofed – or which could point to a mail server that’s controlled by the sender.
How is attribution made?
To get to attribution, a researcher would seek to find a C2 network (Control and Command network) of compromised email senders, ideally, one that has been identified and attributed but not revealed to the attacker. While doable, this kind of attribution is often tricky because email inherently lacks strong authentication, saying, “this comes from here.”
Then we have to think about the timeline. The DNI comes out yesterday, commenting on attribution from an email campaign sent at the earliest late Tuesday. So in less than 48 hours, the DNI has supposedly completed attribution to Iran.
From a cybersecurity researcher perspective, attribution takes weeks, even months. We have historical context from previous attacks where the FBI or DNI does a good job figuring out who an attacker is. To attribute, during the evidence-gathering phase, one would have to know what the C2 network was, a view into the compromised server to validate the information wasn’t spoofed, then be able to look at it and say, “this came from this machine.” Then, one would require preexisting knowledge of who compromised that machine.
From a cybersecurity perspective, it is highly unlikely all of that happened in 24 hours.
Can intent be determined?
DNI (via Ratcliffe) said, in a concise six-minute press conference, there was direct attribution, as well as ascribed intent. For the DNI to attribute this event to Iran and speculate that it was done to damage a specific political candidate, it is highly unusual. Most investigative responses at the national level are factual. Moreover, in this case, the attribution doesn’t hang together from a technological perspective; the speed with which the press conference was held, and lack of information raise questions amongst information security professionals.
What do cybersecurity researchers think?
Paradoxically, this campaign is too simplistic. If we saw several voter registration systems running advanced malware that had been deployed by Iranian groups the government had been watching for six years, the assertion that a foreign nation-state was responsible would be inherently believable. However, this is an email from a nonexistent domain, sent over the internet, using publicly accessible information. There is no hack here. Voter name, party affiliation, mailing address, and email address are all public information.
Secondly, the simplicity of the attack reduces the likelihood that attribution is believable on account of DNI’s ability to leverage military resources or surveillance. By way of analogy, if an attacker places a threatening message on a postcard in a voter’s mailbox, military intel will not speed up the investigative work of determining who the perpetrator was. The functional work required takes time and cannot be expedited purely by throwing more resources at the problem.
It’s usual for DNI to ascribe intent, especially with an “attack” that happened. We put the “attack” in quotes because there was no evidence of cybercrime here, but rather criminal harassment. To ascribe this to Iranian hackers is dubious with respect to what we know about how Iranian hackers work. They don’t tend to engage in false flag operations, and their criminal capabilities are generally aligned towards advanced persistent threat attacks, not email campaigns.
Finally, DNI operating in this way is unusual. There is an influence campaign underway, but for the research community, the factual evidence of what happened outstrips the intentionality behind the effort. Was it Iran? Was it Russia? Was it domestic terrorists doing what they previously said they were going to do? Notably, the American people need to know that these are not legitimate emails, and no one is coming to homes. Unfortunately, DNI’s response did little to address the fears of the voters who received these messages, and instead appears to be focused on source and purpose, without adequate evidence or even the opportunity to ask questions.
Cybersecurity researchers do not discuss “why” this was done or the intent behind these types of activities. There is something in all of this that is abnormal, with respect to how quickly this occurred, the lack of data, the simplistic nature of the activities, and the fact that supposedly immediate attribution and full understanding of intent could be achieved.
We don’t know what happened yet. For those of us in the cybersecurity research community, this is all too fast without ironclad evidence, which we have yet to see presented.





