People are used to getting emails from well-known technology service providers: the Amazon order confirmation, the Microsoft digital voicemail message. Email phishing attackers often exploit this familiarity, sending malicious emails designed to mimic the look and feel of a legitimate message from one of these services.
With the shift to work-from-home, attackers are increasingly adding remote collaboration applications, such as Microsoft Teams and Zoom, to the list of familiar services upon which they base these attacks.
Zoom became one of the top brands to impersonate in 2020 by cybercriminals and it’s holding its unenviable ranking there, into 2021. What’s changing is how attackers are going after users with these well-known techniques – and the kind of users they are targeting is changing, too.
In particular, a new class of Zoom attacks seem to specifically target European users, who may be less likely to speak fluent English.
The “how” takes advantage of Zoom’s recognizable URL structure. The authentic Zoom domain is www.zoom.us, regardless of whether a user or company is located in the U.S. or elsewhere. As a result, Zoom users across the world have become familiar with this brand and URL structure. Now, attackers are using malicious URLs that conform to that structure, with subtle differences. For example:
The cybercriminals who developed this campaign have acquired domains that appear authentic at first glance, matching Zoom’s standard URLs. The impersonated domain adds a “b” onto “web”, an extra “o” into “zoom”, and an additional “us” – all subtle differences the average user or email filter might miss.
In a further attempt to signal legitimacy, the campaign also incorporates the targeted user’s company name into the URL structure.
The originating return path of many of these attacks leads back to “.es” domains, which indicate they originate in Spain. Users targeted with these newly identified phishing campaigns are also located in Spain and surrounding countries in Europe, primarily Spain, France, Italy and Germany.
For GreatHorn customers, the GreatHorn Email Security platform has a protective policy that specifically addresses this form of phishing attack. The policy is providing global protection, across all users.
The phishing attacks are characterized by misspellings that would likely raise suspicions of fluent English speakers, but might go unnoticed by a less-fluent speaker. Here’s an example email, sent with the subject line, “Sheduled Zoom Meeting” (sic):
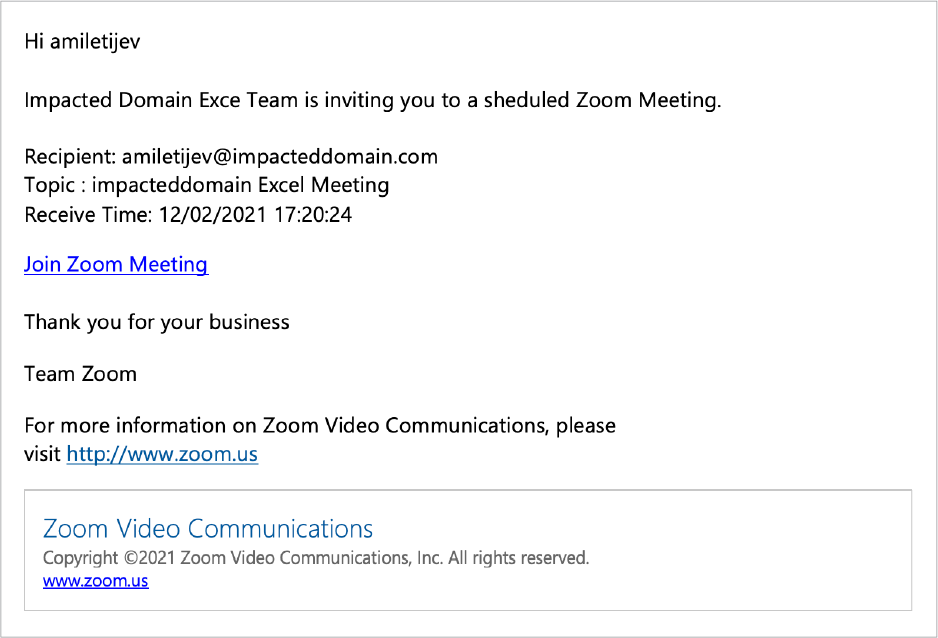
The goal of this email, as with many phishing campaigns, is credential harvesting. Once the attacker gets a hold of a user’s login and password, it can be used to gain access to sensitive files, or as the jumping-off point for internal spearphishing attacks.
In this particular phishing attempt, the unsuspecting user clicks, taking them to a page that mimics the look of an Outlook signup page. Since many services use Outlook for authentication, this is likely to be a very familiar screen for the user.
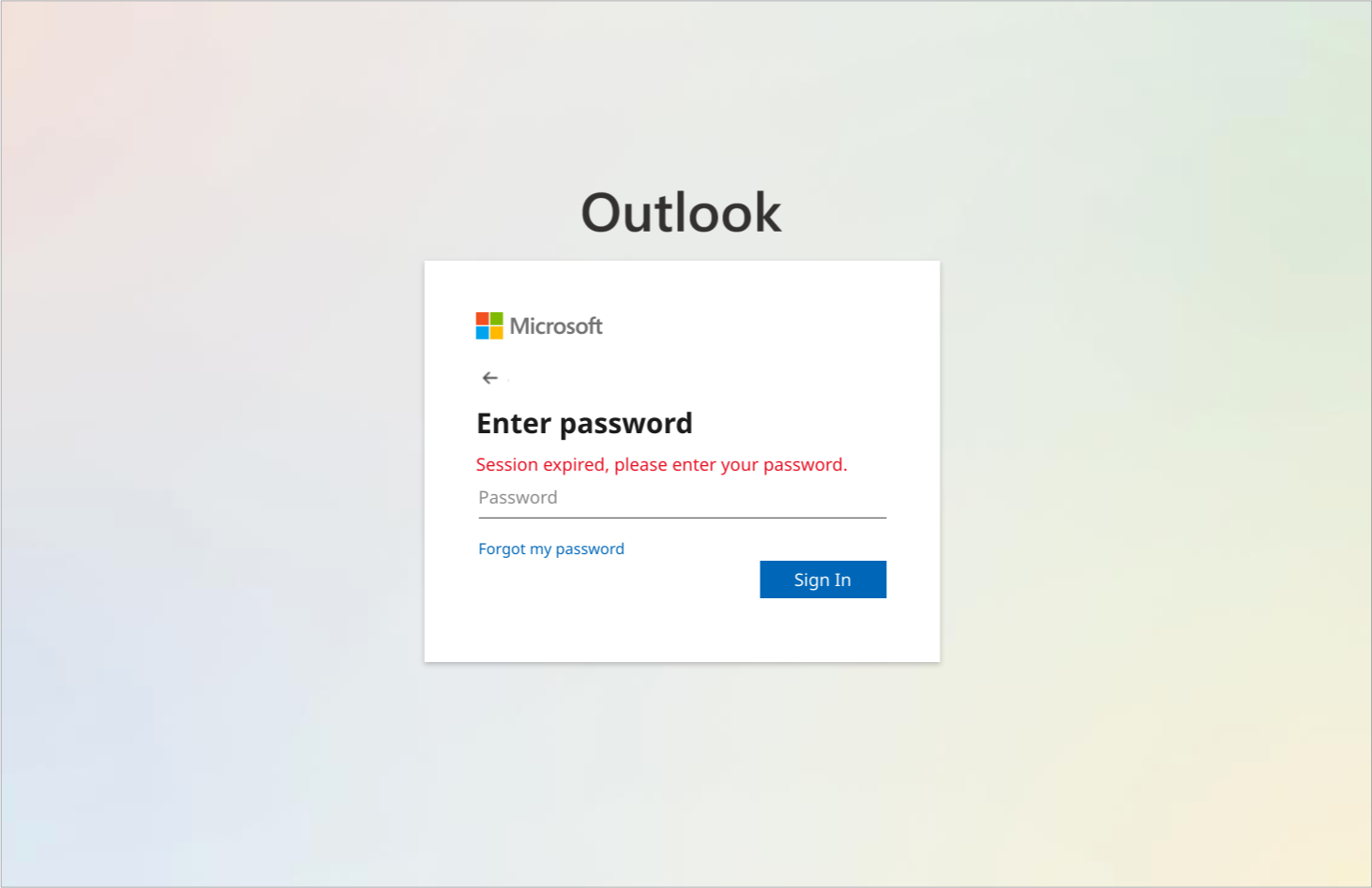
However, as we demonstrate weekly in this blog, cybercriminals continue to find new ways to bypass traditional email security solutions and induce users to let down their guard. Learn more about how GreatHorn’s machine vision and artificial intelligence technologies identify credential theft attempts and keep your users safe.





