There is a new round of emails seen in the wild where attackers are attempting to steal credentials by convincing users that their terms of service through Microsoft have changed. The attack is similar to many common Microsoft spoofing attacks that have exploded in the past year but is noteworthy for a couple of reasons.
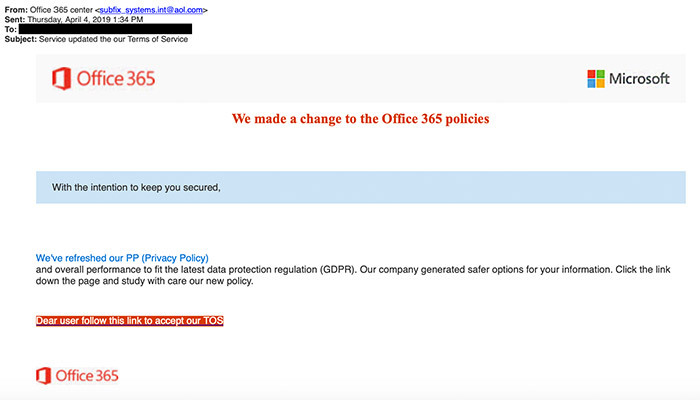 The GreatHorn threat research team has observed a number of instances across multiple client instances where a variety of subject lines referencing Microsoft’s Terms of Service and containing URLs to credential theft sites evaded Office 365’s own analysis. The emails predominantly utilized display names referencing either the Office Message Center (Оffiсе mеssаgе сеntеr) or Office 365 Message Center (Оffiсе З65 mеssаgе сеntеr), but the special characters were used as an obfuscation method and seemingly to great effect. In another attempt to fly under the radar, all of the emails originated from AOL addresses. This (and most any freemail service use for that matter) almost guarantees no SPF, DKIM, or DMARC issues.
The GreatHorn threat research team has observed a number of instances across multiple client instances where a variety of subject lines referencing Microsoft’s Terms of Service and containing URLs to credential theft sites evaded Office 365’s own analysis. The emails predominantly utilized display names referencing either the Office Message Center (Оffiсе mеssаgе сеntеr) or Office 365 Message Center (Оffiсе З65 mеssаgе сеntеr), but the special characters were used as an obfuscation method and seemingly to great effect. In another attempt to fly under the radar, all of the emails originated from AOL addresses. This (and most any freemail service use for that matter) almost guarantees no SPF, DKIM, or DMARC issues.
The URLs contained within the messages redirected to websites with a compelling version of a Microsoft login page, including the user’s pre-populated email. In addition, the malicious URL could easily convince an unsuspecting end user that the URL is real:
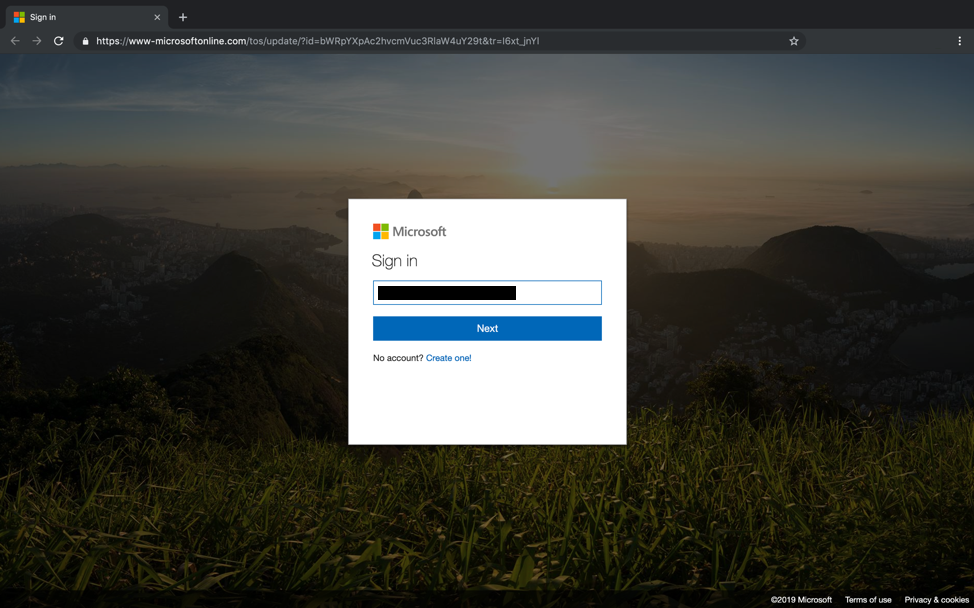
When checking the URLs identified within the attack up against well-known and publicly available threat intelligence sources, none of the URLs used in the attacks were classified yesterday while the attacks were ongoing. Additionally, all of the URLs identified now seem to redirect to Microsoft’s Services agreement. This means that while this particular tactic is not exactly new, the URLs can potentially be reused again in the future and most threat intelligence sources will not have them blacklisted. This underscores the need to move beyond an overreliance on threat intelligence when attempting to identify attacks via email.
GreatHorn recently announced new capabilities to proactively identify and block Office 365 credential theft attempts using computer vision. This technique does not rely on reactive identification of malicious sites. More details can be found in our press release and on our blog.




