Another Office 365 voicemail related phishing attack is here—and this time with a twist.
This is the second Office 365 voicemail related phishing attack GreatHorn has seen within the past few months. The first attack, which we covered in our Phishing emails, explained: “New Voicemail Message!” blog post, entered environments as a false voicemail notification.
This new phishing campaign utilizes the inner workings of CSS to mask the true indicators of malicious content from both Secure Email Gateways (SEGs) and the human eye.
Secure Email Gateways (SEGs) perform a simple pass-fail test on every email before it enters your environment. Typically, SEGs determine whether or not an email is malicious by analyzing several criteria—the most significant being the email headers and metadata, as well as the source code of any attached files. We’re all familiar with the age-old trick of reversing text elements in the source code (and so are SEGs).
However, the attackers behind this new phishing campaign are actually utilizing the script mixing tools found in cascading style sheets (CSS) to create html that renders differently to a machine than the human eye. Because the rendered message is different than the text equivalent, pattern-detection and other malicious detection capabilities are ineffective.
CSS enables attackers to easily mask malicious content by rendering a SEG’s pattern matching capabilities ineffective and thus results in the successful delivery of a malicious email. There are two ways to do this:
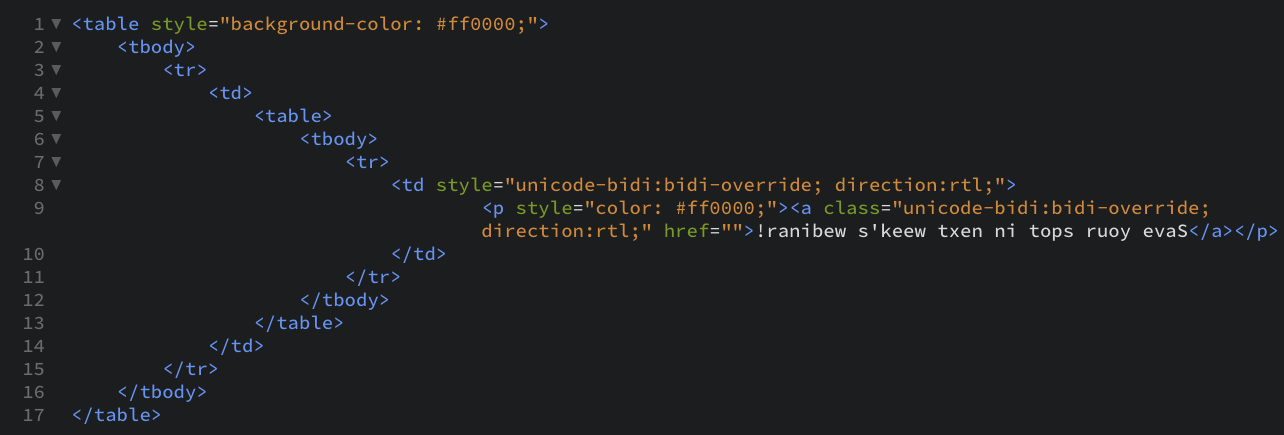
- Attackers can reverse the direction of text in the code, but have it render normally once the message is in a user’s inbox
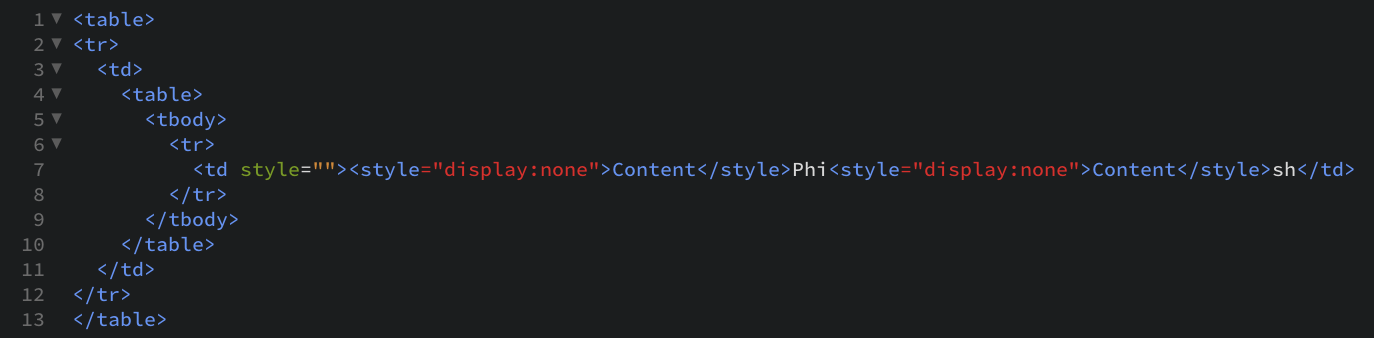
- Attackers can also hide invisible characters in between legitimate ones to disguise malicious attacks in what looks like a regular email.
Many secure email gateway (SEG) solutions still largely follow the authoritarian, perimeter-based security model that typified the pre-cloud world. Sure, SEGs can run in the cloud, but they do not draw on the cloud’s advantages.
In order to more effectively secure your email environment, you may want to look into an API approach. In contrast to SEGs, an API approach to email security uses cloud-native architecture to power a multi-layered approach and provides more visibility and greater control that cannot be achieved by a secure email gateway.
Let us show you how GreatHorn’s API approach is different from traditional secure email gateways. View our Intro to GreatHorn webinar on demand, or if you’re ready to speak with a GreatHorn team member, schedule a personalized demo.




