GreatHorn’s second annual Email Security: Trends, Challenges, and Benchmark Survey Report includes insights from over 1,000 information security and white-collar professionals.
Today, we released our annual benchmark survey report on the state of email security. Conducted every year (well the last two years anyway), this report provides a way for IT and InfoSec professionals to understand what’s “normal” when it comes to email security and identify the areas where they can improve. Here’s a snapshot of a few of the key questions, but you’ll want to download the report to get the full picture.
“Which of the following types of email do you/your users see in your inboxes (NOT what gets quarantined)?”
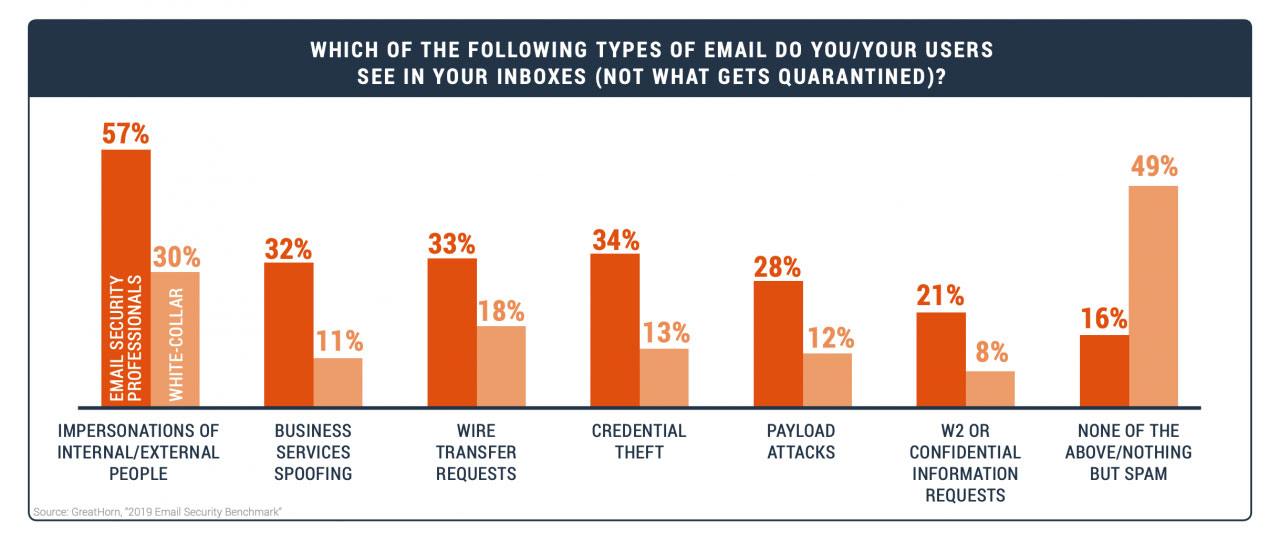
As you can see in the chart, it’s not just the sophisticated and personalized phishing attacks that evade email security filters.
Traditional email security can’t keep up
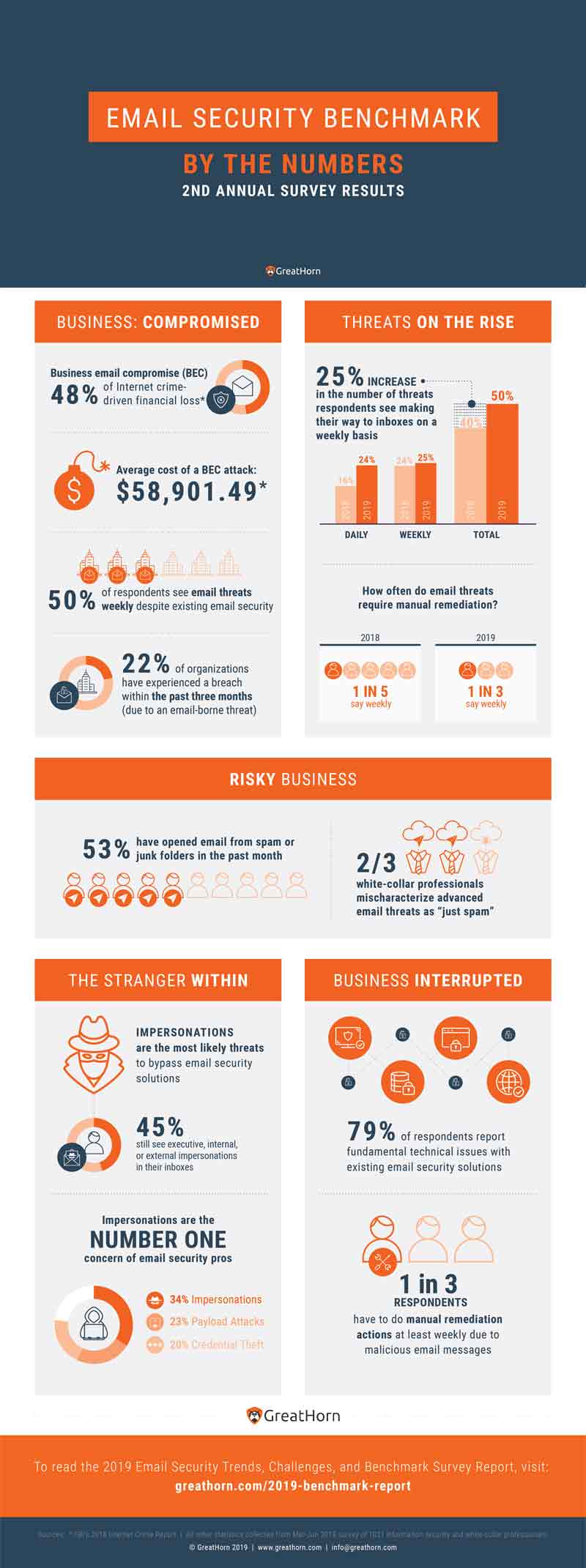
Despite a multi-layered defense strategy that includes an average of more than two email security solutions, 49.8% of respondents see malicious emails reach their inboxes every week. In the past three months, more than 1 in 5 respondents (22%) reported experiencing a data breach (defined as a compromised account, loss of confidential data, credentials, fraudulent financial transaction) due to an email-borne attack. Since last year, there’s been a steep rise in email remediation rates from 20% of respondents needing to take direct actions every week to more than 34% this year. More than one-quarter of email security professionals report that payload attacks (e.g. malicious/suspicious attachments or links)—despite being the threats most heavily guarded against—are still making it through their cybersecurity defenses.
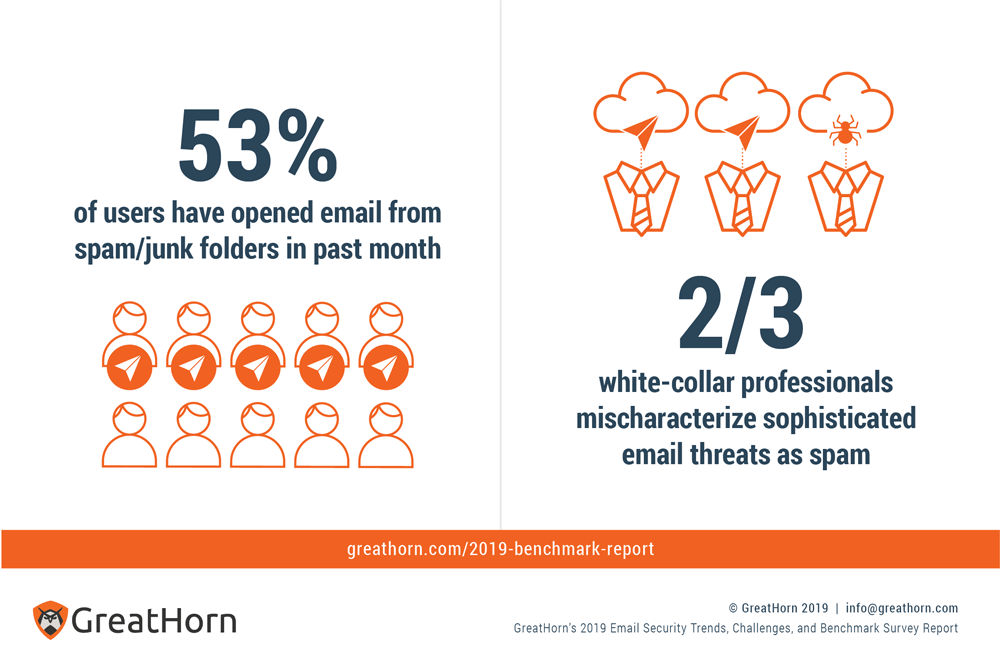
Nearly half of white-collar professionals reported “nothing but spam” in their inboxes
Frighteningly, our data also shows that nearly half (48.5%) of white-collar professionals reported “nothing but spam,” but only 16.4% of email security professionals said the same. That means that two-thirds of white-collar professionals mischaracterize sophisticated email threats as “just spam.”
Individuals with limited or no involvement in email security are 3x more likely to say “I don’t see anything but spam in my inbox” compared to those respondents involved in email security (48.5% vs. 16.4%). This illustrates a clear exposure to risk despite the large sums of money having been spent on cybersecurity awareness training programs. According to recent research, since 2015 more than $1.2 billion has been spent on computer-based training* (Gartner), but simulated phishing click-rates have dropped by only 1% from 2017 to 2018* (2019 Verizon DBIR).
Our findings from this year’s survey beg the question: How can we improve the state of email security?
It’s not an easy task, but a good initial step is to take a step back from the tools and technologies that we so heavily rely on and reconsider how we – as an industry and as IT/security leaders– approach securing email. Email is deep-rooted. It’s been around for decades and so have the security methods. As an industry, we’ve fallen into a pattern.
- We expect email security tools to catch all threats before they reach end-users.
- But, when our technologies fail to do so, we fall back on training and phishing simulations, reducing some risk, but not enough.
- Then, we rely on time-consuming remediation actions like PowerShell scripting to try to stop email attacks before they do more damage.
This pattern creates huge risk exposure – leaving organizations vulnerable. As email threats become more sophisticated, we need to reconsider how people, process, and technology intersect.
- Identify the business processes that are easily exploited by cybercriminals. Establish processes such as “wire transfers cannot be authorized over email” or “HR information cannot be transmitted over email” to narrow some of the most dangerous gaps. Work out additional policies that address your organization’s specific risk profile.
- Recognize that your employees are not your biggest vulnerability but your most valuable defense. When given the correct tools and context, people will often make the right decision. Educate your employees in the moment of risk, not just theoretically in big lectures, phishing simulations, or annual computer-based trainings classes. Contextually, within their actual inboxes, explain why a suspicious message may be a threat and also give real-world advice on what to look for to help determine legitimacy.
- Lastly, IT and InfoSec teams must view technology as an enabler – not a totality. Clearly, advanced technologies are necessary for threat detection and blocking, but can also be used to educate end-users in the moment of risk and to reinforce business processes by putting reminders on relevant emails. Teams should also realize that there is no silver bullet, remediation will always be necessary, so give your IT and InfoSec teams the automated tools necessary to quickly find and remove threats from inboxes. These automated tools are often an afterthought in traditional email security gateways.
We asked respondents how often direct remediation and/or incident response actions are necessary (i.e. suspending compromised accounts, PowerShell scripting, resetting compromised third-party accounts, etc.).
Since last year, there’s been a steep rise in remediation rates from 20% of respondents needing to take direct email remediation actions every week to more than 34% this year.