The term “cloud-native” gets thrown around a lot, but in email security there are very few cloud-native solutions. It’s crucial to understand the difference between “running in the cloud” and a “cloud-native architecture.” While many secure email gateway (SEG) solutions claim to be cloud-based, the implementation style and architecture has not fundamentally shifted and still largely follows the authoritarian, perimeter-based security model that typified the pre-cloud world.
Companies are increasingly migrating to the cloud, so why aren’t email security solutions following suit?
- Secure email gateways still require the re-routing of mail through the perimeter, forcing administrators to make and maintain DNS changes and MX records. Not only is this inconvenient, it requires ongoing maintenance as IT and security teams incorporate new services and domains.
- Designed to interrupt email flow to “catch” dangerous threats before they reach an organization’s environment, secure email gateways have limited capabilities to warn or remediate threats once a malicious message “passes” the gateway. This limits the SEG’s ability to identify and stop zero-day threats, targeted phishing attacks, and account takeover attempts.
- The SEG’s position in an organization’s security landscape means that they have no visibility into intra-organizational email unless a separate module is purchased.
- Businesses are no longer willing to sacrifice productivity and agility in the name of security. A tightly tuned system negatively impacts business velocity as emails get stuck in quarantine, and security teams waste time releasing them.
- Despite IT and security teams’ concerted efforts to set up authentication correctly once a SEG is in place, the SEG repeatedly breaks authentication for both incoming and internal mail, often resulting in Office 365 “junking” legitimate email.
Sure, SEGs can run in the cloud, but they do not draw on the cloud’s advantages. In contrast, cloud-native architecture powers a multi-layered approach and provides two critical benefits that cannot be achieved by a traditional secure email gateway (even if it’s hosted in the cloud):
- Greater visibility: Across all intra-domain email, already delivered but newly weaponized email, and even rapidly moving, zero-day threats spreading across our client base
- More control: Unlike a one-size-fits-all email security solution, an API approach to email security is smarter, able to learn, adjust, and improve protection in a way that’s unique to your organization
Cloud-native protection requires unique architecture. GreatHorn is built from the ground-up to leverage cloud-native, cloud-first principles, using platform APIs to continuously identify and mitigate threats. GreatHorn won’t take your email system offline—unlike old-school platforms that rely on cumbersome quarantines and end-user interaction to retrieve mail.
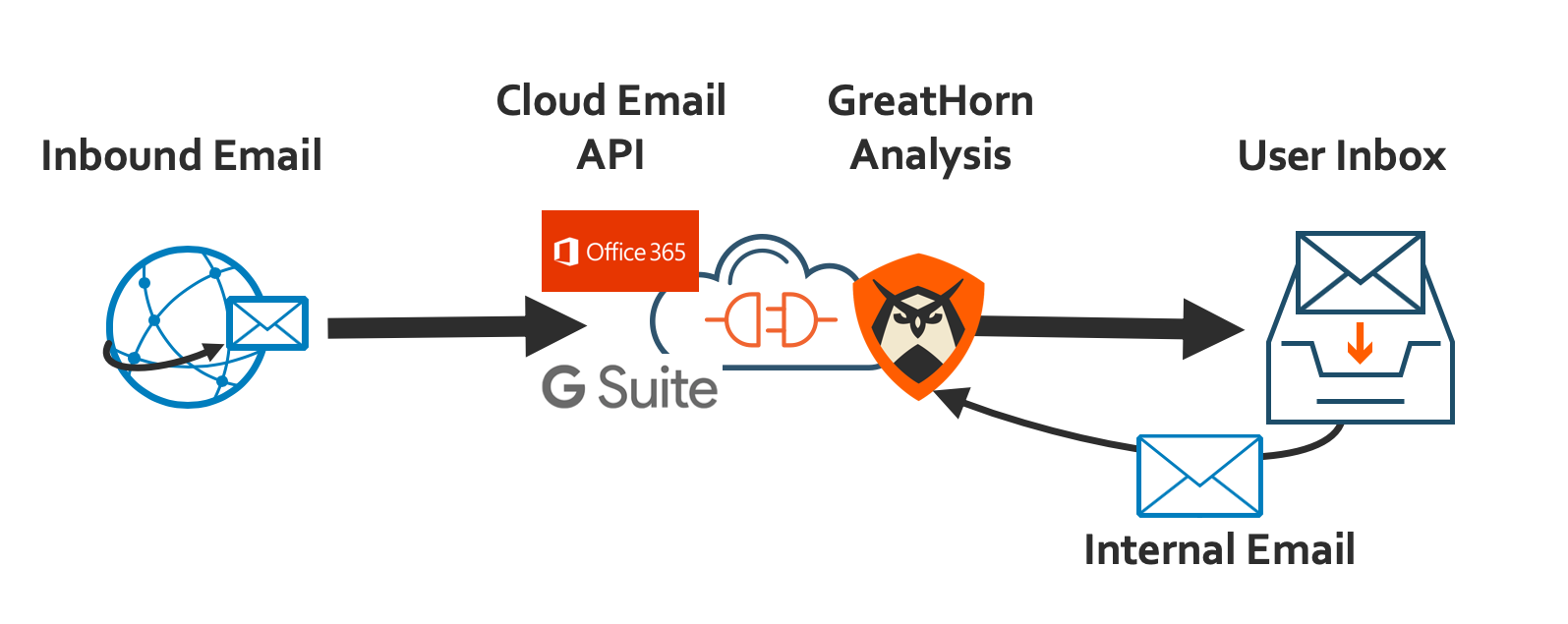
GreatHorn does not cause email to go offline, be delayed, or get lost in quarantine.
It may surprise you to learn that more than 80% of organizations think their email security tools are just “good enough,” according to a recent GreatHorn survey of 1,000+ professionals?
We don’t believe “good enough” is good enough. Let us show you how GreatHorn’s API approach is different from traditional secure email gateways. Register for our upcoming webinar, or if you’re ready to speak with a GreatHorn team member, schedule a personalized demo.





