Over the last 18 months, phishing and advanced threats have become a significantly more dangerous >threat for many businesses. As we discussed in our look back at 2019 , 50% of the information security professionals whom we interviewed reported that email threats and malicious messages reached their end users’ inboxes, despite their investments in traditional email security technology. In fact, those legacy Secure Email Gateway (“SEG”) solutions carry with them significant technical and operational risks and drawbacks, including:
- Downtime – if a gateway goes offline, it becomes impossible for businesses using them to receive or send any email
- Mail Delivery Delays – many SEG tools require more than a quarter of an hour to process records; users often report significant reduction in their ability to use email for real–time communications, even when their email security tools aren’t struggling with outages
- Visibility to Attackers – traditional email security tools require modification of DNS records (MX gateways, in particular), which are easily discoverable by attackers, and can lead to specific attacks known to bypass weaknesses in these tools
- Limited Remediation Capabilities – given the “in-line” nature of SEGs, once messages have moved into user mailboxes, there is often no ability to do post-delivery modification or remediation without expensive and poorly integrated add-on tools
- Outdated, Static Rulesets – because traditional SEGs are based on technology that is often decades old, and operates on a perimeter security model, there is no capability for them to detect advanced attacks that mutate during the attack window (“polymorphic attacks” is how these are most often referred to by vendors)
Over the past few years, however, novel and innovative solutions have been created which address these shortfalls, and, unlike SEG tools, can be operationalized in minutes and eliminate all the drawbacks described above.
Secure Email Gateways have been around since just before 2000, and while they still perform traditional tasks well like preventing traditional email attacks and providing continuity, their cracks begin to show as unplanned outages and modernized, targeted spear-phishing and whaling attacks evolve.
Comprehensive cloud native email security solutions, with no interruption to email delivery and zero visibility to the outside world, also allow for a full set of remediation capabilities. Unlike block/quarantine/allow options available from legacy SEGs, adopting a cloud-native approach means that organizations can build fine-grained controls, including:
- Full protection over modernized URL, Impersonation and Phishing attacks
- Rapid Incident Response: Full post-delivery remediation capabilities, meaning that attacks can be identified both at time of delivery and at any point thereafter, and easily removed from inboxes even in bulk.
- Protecting users by having the ability to remediate a new security incident based on any criteria in seconds.
- GreatHorn’s customers often cite the ability to manage threats at scale as a major difference from their legacy tools.
- User Engagement:User-specific banners that describes exactly what type of threat they are currently seeing, instead of a generic “PHISHING” or “EXTERNAL” banner in the message itself.
- Easy SOAR and SIEM integration
- Realtime phish alerting and reporting, not simulations
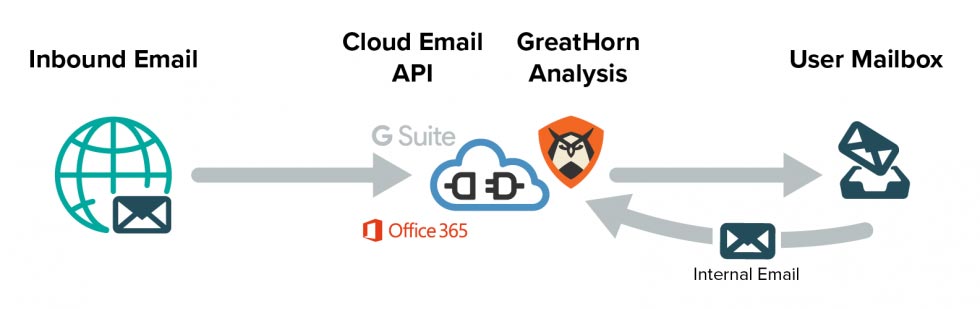
GreatHorn is an API based solution that has been built to provide an agile, aggressive threat detection platform, with no risk to business interruption caused by downtime because emails are not processed as a separate hop prior to delivery. With GreatHorn, there are zero environmental changes that need to be made that publicly expose the elements of the security stack an organization is leveraging to bad actors.
GreatHorn is the world’s leading cloud-native email security platform, and in addition to the technical advantages over a legacy gateway outlined above, we also provide best-in-class security over our own platform. With multiple years of SOC II Type II audits in place, GreatHorn uniquely addresses modern email security threats without the security, operational, or deliverability risks that come with traditional tools.
GreatHorn takes 5 minutes to authorize and has a prebuilt, ready to protect environment out of the box so your security team can be up and running nearly instantly and fully protected as you scope us to your unique environment.
If you’d like to learn more about how GreatHorn’s API approach to email security keeps your environment secure without ever going offline or delaying email, schedule a personalized demo. Don’t want to commit to a demo? Join us on Tuesday, April 28th for our Intro to GreatHorn webinar it’s like a demo with no strings attached.





