On January 31, GreatHorn’s threat response team identified a widespread business email compromise campaign targeting senior executives claiming to be a Doodle poll required to reschedule an upcoming board meeting. The attack links directly to a well constructed Office 365 credential theft site.
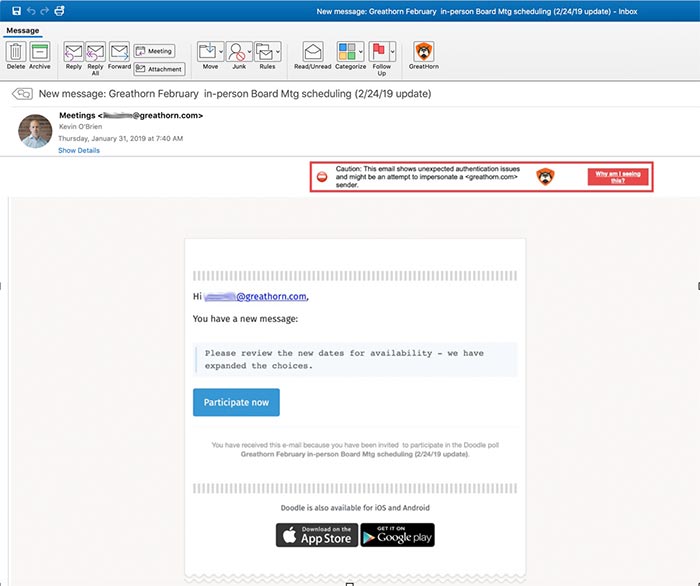
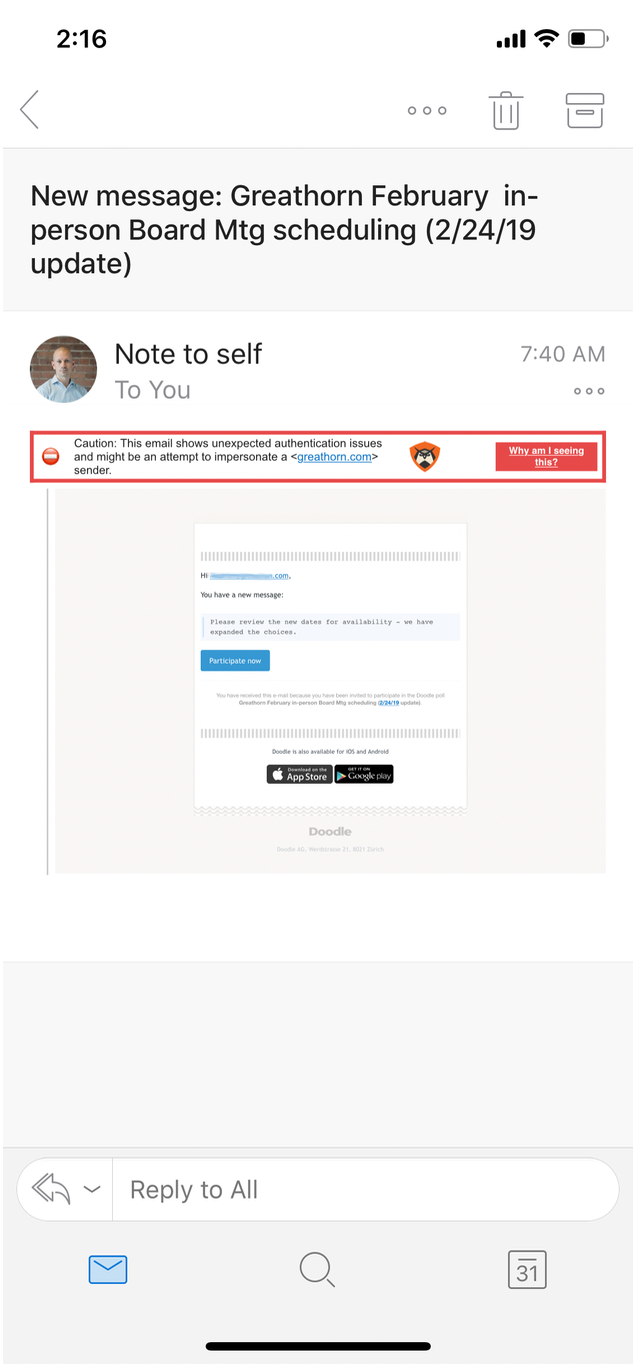
Purporting to be from the CEO of an organization, the phishing attack claims that a planned board meeting needs to be rescheduled and requests participation in a poll to identify a new date.
The attack appears to be hitting multiple senior executives (e.g. CEOs, CFOs, CTOs, SVPs) within an organization and has been found present across multiple industries and organization sizes, always direct spoofing (i.e. using the same “from” email address as the “to” email address) with a display name of “Meetings” and subject line / content personalized to the targeted company.
Importantly, on a mobile device, the native Outlook client overwrites the display name to say “Note to self,” further complicating the attack and making it even more likely for a recipient to interact with it. While some of these messages were sent to Microsoft’s “Junk” folder, they remained accessible to end users, leaving them vulnerable to the attack. As of 3:20pm, the destination site remained up and unidentified by browsers as a malicious site.
The attack was found (and eliminated) in 14% of GreatHorn’s customer base. In addition to blacklisting the domain, GreatHorn correctly identifies the destination as suspicious in its Link Protection module.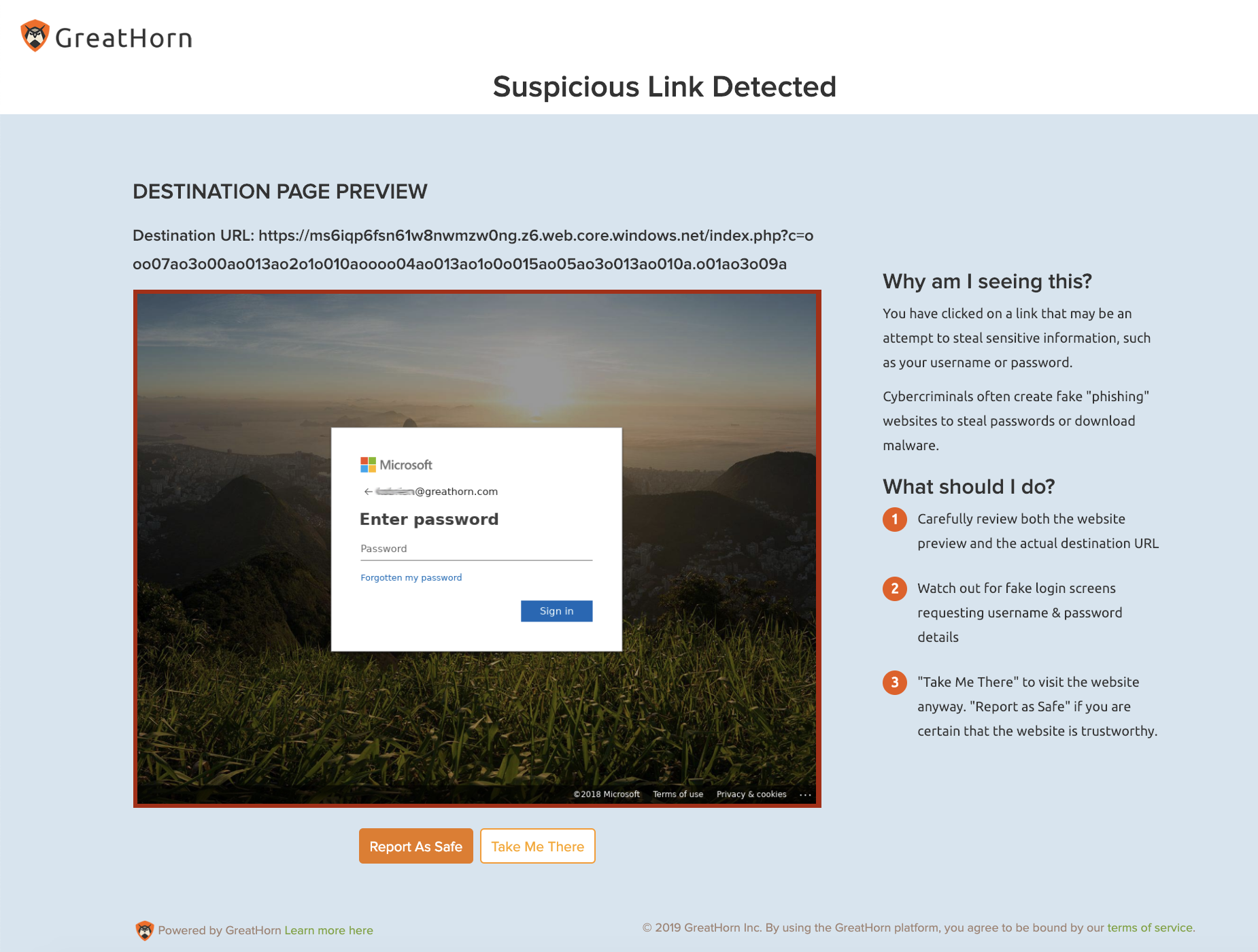
The GreatHorn security team is currently monitoring this attack and providing automated support to clients.
Currently, here is what we know about this attack:
- The initial point of infection is via a phishing email sent to senior executives with a display name of “Meetings” and their own from address.
- The subject line is consistently New message: [Company Name] February in-person Board Mtg scheduling (2/24/19 update)
- The email appears to be a Doodle poll but actually links to an Office 365 credential theft site, with a primary domain ending in web.core.windows.net
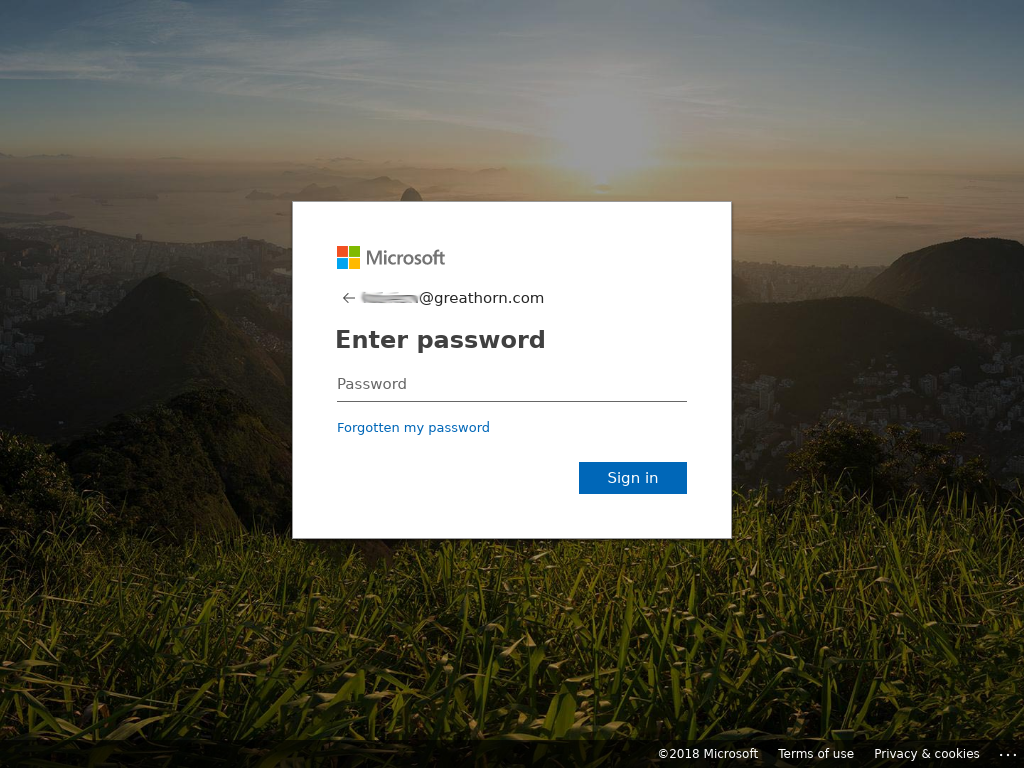
GreatHorn Security Response:
- All attack emails within GreatHorn’s customer base have been removed from customer inboxes.
- All customers of GreatHorn Email Security can rest assured that this destination has been added to GreatHorn’s blacklist, ensuring that all future emails will be blocked
We are continuing to monitor for evidence of this malware and will provide additional information and remediation support as our investigation continues.
If you have any questions or concerns, please feel free to contact the GreatHorn team at [email protected].




