The GreatHorn Intelligence Team has identified an increase of 84% in phishing attacks leveraging Google’s open redirects using Google Meet and Google DoubleClick between Q1 2021 and Q2 2021. The use of the open redirects on these platforms allows for threat actors to evade detection by most email security solutions, allowing emails to land in users’ inboxes and appear as trustworthy links. These attacks are primarily focused on getting users to fall victim to credential harvesting, payment fraud and auto-downloads of malware.
What are open redirects?
Open redirects occur when an authentic domain allows the user to input data and determine what the destination URL will be, redirecting the user who clicks on the link to any destination URL.
What makes open redirects dangerous to users?
Most email security solutions are not able to identify the misuse of open redirects when analyzing the URL in real-time. If that specific full URL has not been identified as “known bad”, those links will pass through the email security solution and into your users’ inboxes. Threat actors use authentic and trustworthy domains that allow open redirects, such as Google, to more effectively trick users into clicking a link and falling victim to the attack.
Google DoubleClick
Google DoubleClick is the advertising technology that provides deep analytics and insights for marketers to more effectively advertise based on the behavior of users. DoubleClick has been known to maintain this security vulnerability dating back to 2008, following the acquisition by Google. Since then, the open redirect and the vulnerabilities this type of access poses has not been addressed. Even in 2014, a known malvertising campaign was identified using doubleclick.net.
The structure of the open redirects within the phishing campaigns identified by the GreatHorn Threat Intelligence Team are all similar, whereby the attacker adds in the “advertising URL” (seen as “adurl=”) to redirect the user to the destination site, that appears as a legitimate site, but in fact is malicious. To note, an attacker does not require a DoubleClick account to develop the redirect. Instead, anyone can modify a DoubleClick URL and change the redirect.
Between Q1 2021 and Q2 2021, the use of Google’s DoubleClick platform to send malicious links increased 141%.
Google Meet
Google Meet teleconferencing is a highly used and recognized service, commonly used and included in any subscription to Google Workspace. In fact, during the COVID-19 pandemic, Google reported over 100 million daily Meet meeting participants. And, because of the widespread use and trust associated with the #1 brand on the market, leveraging the option to apply an open redirect became a commonly used practice by threat actors. Between Q1 2021 and Q2 2021, the use of Google Meet platform to send malicious links increased 57%.
The structure of the open redirects within the phishing campaigns identified by the GreatHorn Threat Intelligence Team are all similar, whereby the attacker adds in a “link redirect” (seen as “linkredirect?”) to tell the browser what destination site the user should go to. Unfortunately, using the domain of “meet.google.com/” appears as a legitimate site, but the destination site found after the “dest=” in the URL parameter is malicious.
Example of Phishing Emails Using Google Doubleclick and Google Meet:
Though these emails do not pose as Google itself, and instead use the Microsoft brand, the success of these campaigns is predicated on the trust of Google’s domain authority itself. Therefore, instead of most email security platforms, analyzing the redirect, they look only at the root domain which bypasses traditional email security that would typically block malicious sites.
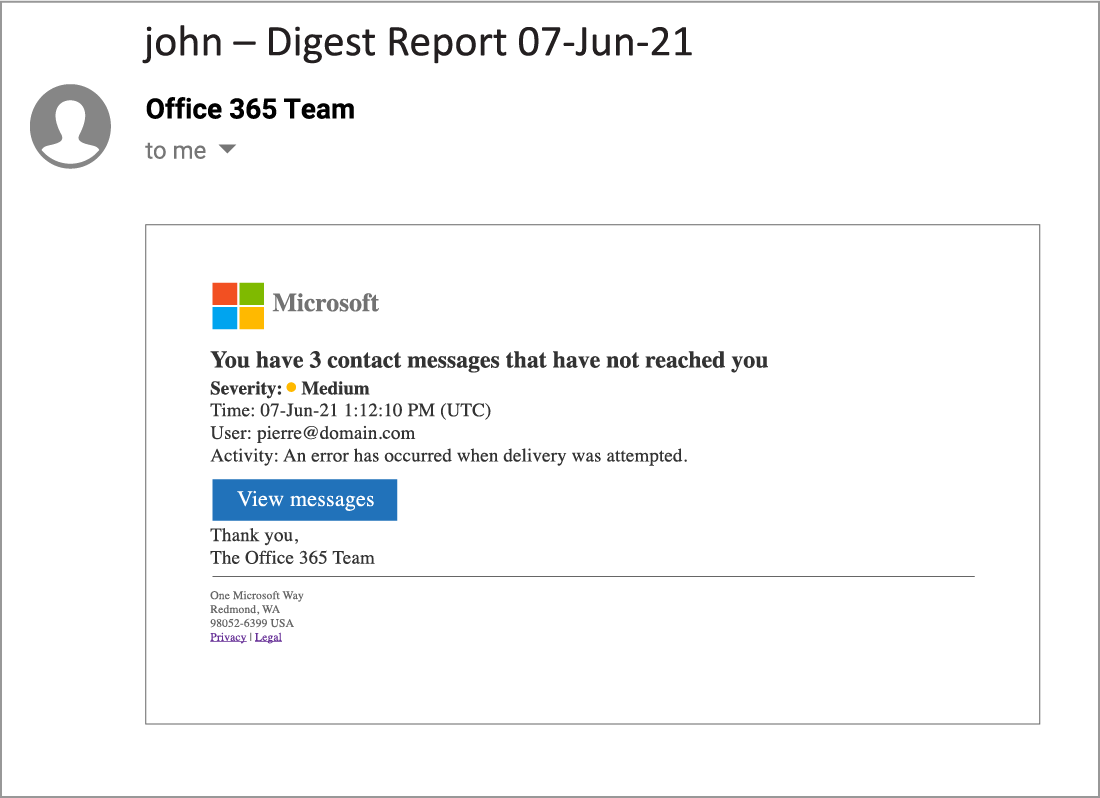
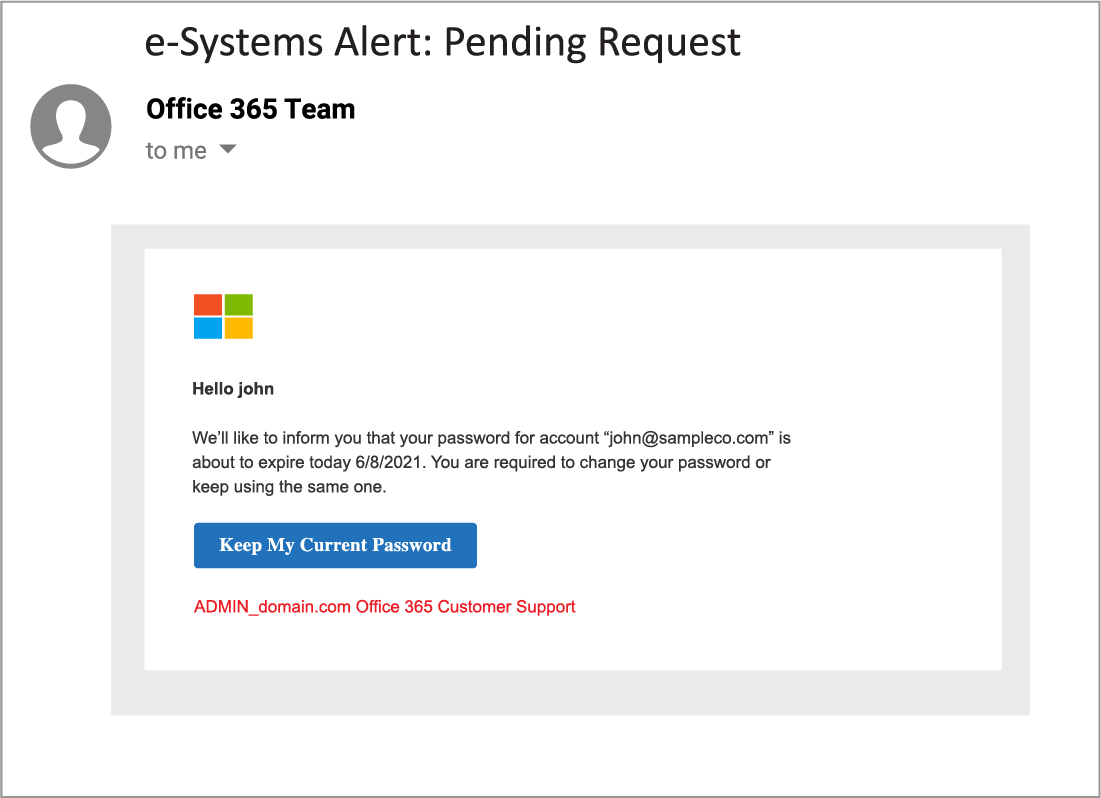
The links embedded within the emails all lead to similar destination URLs, where a user’s credentials are harvested, with some destination sites also deploying an automatic download of malware.
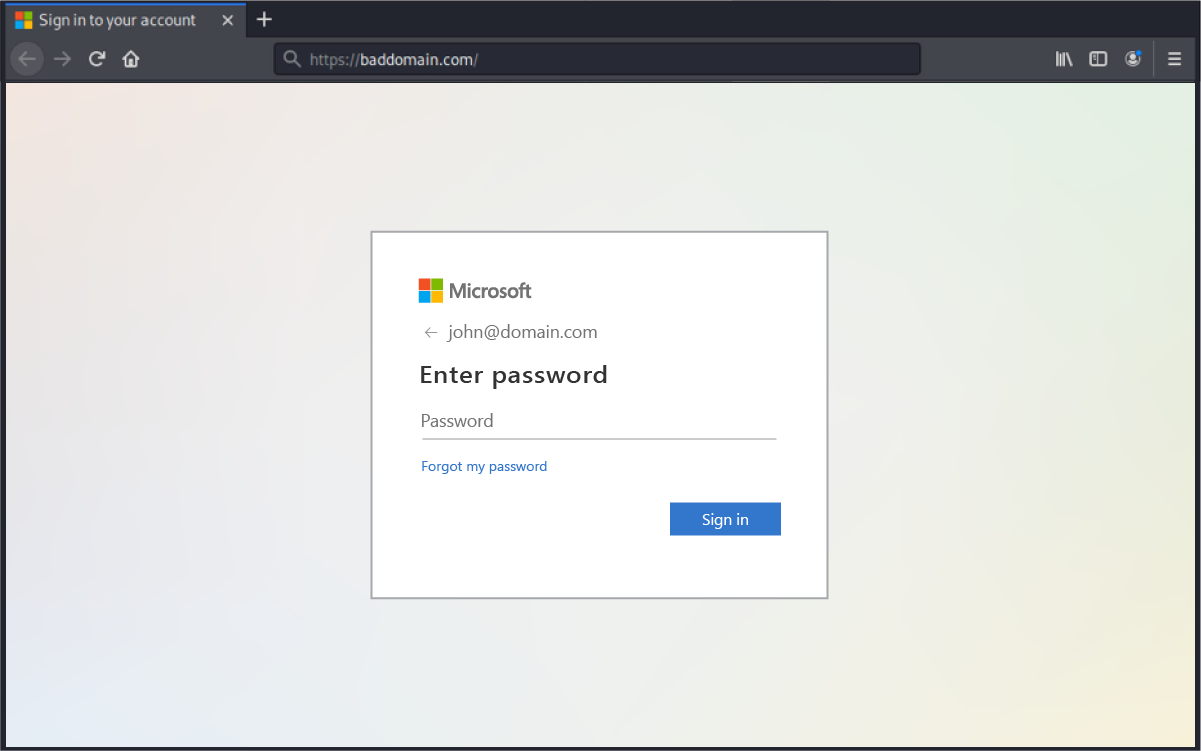
In order to protect users and your organization from attackers taking advantage of Google DoubleClick and Google Meet, GreatHorn recommends that security teams understand how their email security platforms analyze both domain authority and destination sites to protect users from falling victim to open redirect attacks. Learn more about how to protect your users and organization from open redirects.
Want to uncover if your organization is experiencing phishing attacks leveraging Google’s open redirects?
Try GreatHorn Risk-Free for 30 Days!





