Phishers exploit human nature, taking advantage of individuals, combining social psychology, technical systems, security subjects and politics.
Call it what you will: business email compromise (BEC), phishing, spearphishing or whaling, all email-based cyberattacks have one thing in common: they use social psychology. The goal of the email attacker is to put the user off balance, causing an emotional reaction that gets them to open an email and take a compromising action.
Sometimes social engineering means making a message look like something a user would expect to see: an urgent request from an executive, or an email from a vendor. Other tactics go for the exact opposite, using tactics that are decidedly not safe for work.
The GreatHorn Threat Intelligence Team has identified a new trend on corporate email where attackers are using X-rated material in emails designed to lure employees. Between May 2020 and April 2021, the number of such attacks increased 974%. These attacks reach across a broad spectrum of industries and appear to target based on male-sounding usernames in company email addresses.
These attackers aren’t always appealing to salacious interests. Sometimes, users will open an email simply because its header and subject line are shocking and unexpected. This type of tactic is known as “Dynamite Phishing”: shocking a user in order to get them to take action. It doesn’t always involve explicit material, but the goal is to put the user off balance, frightened – any excited emotional state – to decrease the brain’s ability to make rational decisions.
In these recent attacks, the attackers use malicious URLs that proceed to one or more of the following:
- Automatic download of a malicious file onto the user’s machine,
- Redirectors that send the user to a dating website where they capture financial information, and/or,
- Tracking user behavior for a secondary attack – extortion.
Attackers use phishing attacks as an initial vector to gather information about the target. Because of the x-rated content, attackers set up victims with compromising material to be used for blackmail. In these attacks, cybercriminals are tracking the identity of victims who click on their sites by using a technique called an email pass-through. The same technology enables legitimate email senders to auto-populate an unsubscribe field with a user email address. Once a user clicks on a link in the email, their email address is automatically passed to the linked site. In these attacks, the cybercriminal leverages the information they gleaned in order to set up a second stage. Individuals who clicked on links to compromising material could be targeted in the second attack to extort the individual.
Example #1:
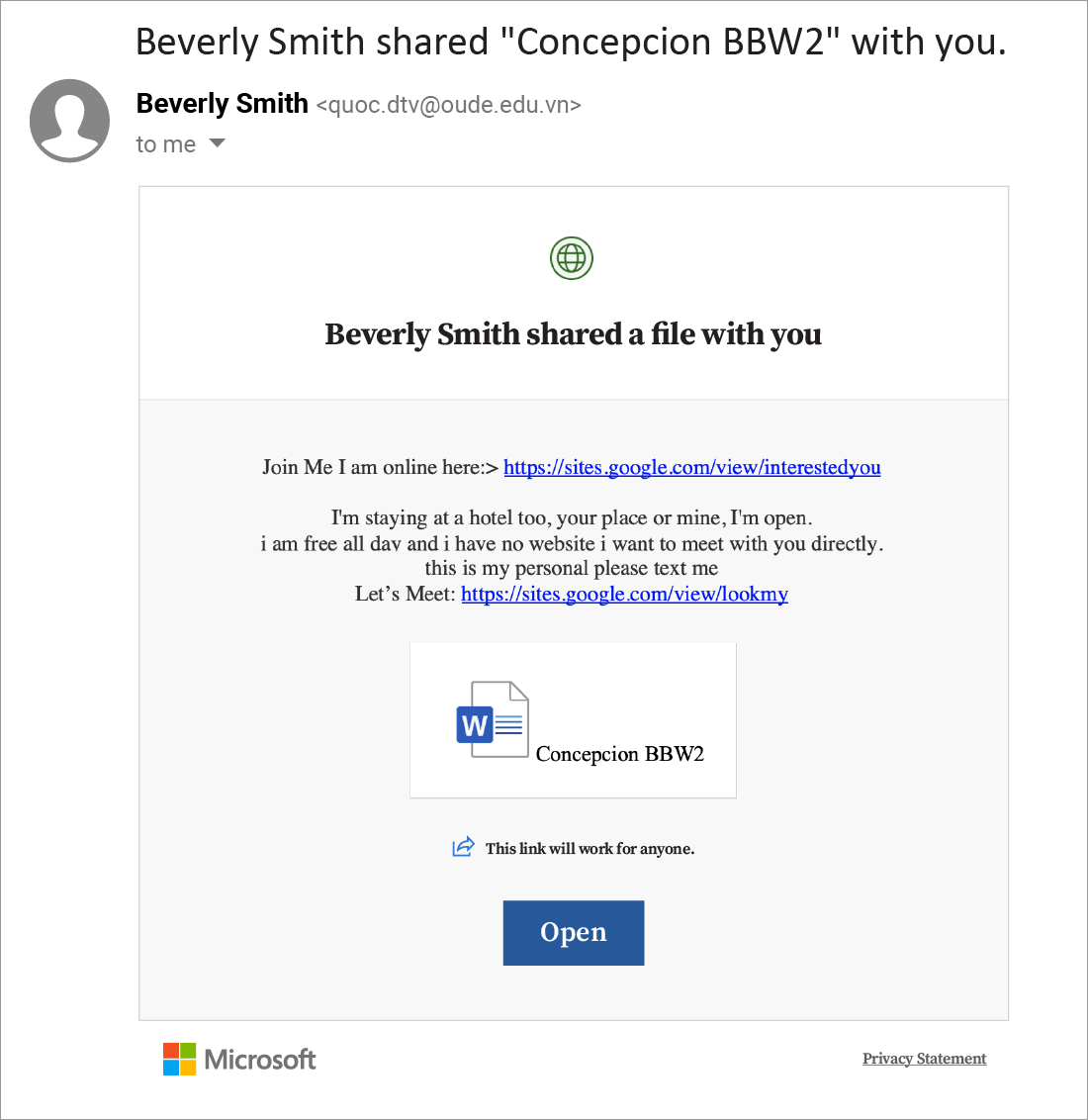
The link at the top of this email points to a destination page which is classified as Malicious by Google Safe Browsing. Clicking on (https://sites[.]google[.]com/view/interestedyou would bring you to a site with photos. There, a further link points to hungrygrizzly.com, which has the appearance of a dating site. It is likely a fake site designed to hook users into providing payment information. User data gleaned in this way will be transmitted to cybercriminals, who will use it for various malicious purposes, such as money withdrawal, blackmailing or committing further frauds.
Example #2:
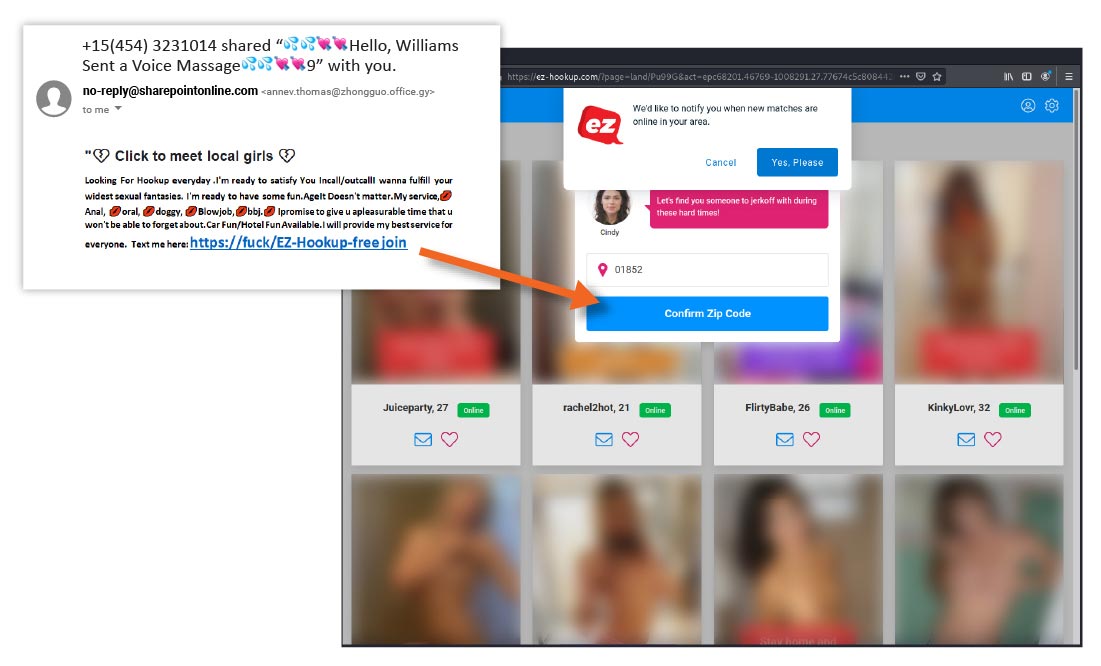
Clicking on (https://fuck/EX-Hookup-freejoin would bring you to a site with x-rated photos, with the ability to “confirm zip code” and search for individuals in the area. In addition, the URL installs cookies onto the user’s browser enabling notifications. It is likely a fake site designed to hook users into providing payment information. User data gleaned in this way will be transmitted to cybercriminals, who will use it for various malicious purposes, such as money withdrawal, blackmailing or committing further frauds.
To find out more about how malicious URLs like these work, and how GreatHorn protects against them, click here.





