With the holidays just around the corner, more impersonation attacks are targeting users. In fact, brand impersonations are 83% of spear phishing attacks.
Cyberattacks have become more subtle. As we embark on the holiday season, the GreatHorn Threat Intelligence Team found a clear example of a phishing attacks impersonating American Express. What makes this attack successful, and bypasses traditional email security solutions, is not only the authentic-looking email, but the use of Google Forms to capture user credentials and other personal identifiable information (PII).
As more cybercriminals target users with advanced phishing attacks, the question remains is: How can we detect these attacks before reaching end users?
What is an example of a phishing attack impersonating American Express?
The American Express impersonation attack refers to the newest phishing scam that targets consumers and businesses, masking as an American Express account verification email.
What makes this cyber-attack successful, is the ability of these emails to bypass traditional email security with the use of Google Forms URLs. Google Forms is a platform designed to record information through surveys and registration sheets. Because it is a legitimate platform, these URLs are more effective at bypassing email security solutions and reaching users, and have become a common vector for cybercriminals to leverage as part of a multi-step attack.
How does this phishing attack work?
To understand the risk of this attack, here is a step-by-step guide to how this campaign is executed and successfully harvests credentials, along with other PII.
Step 1: Email
The phish itself appears as a legitimate email from American Express. Within the design of the email, the cybercriminals have even pulled authentic American Express logos and other branded elements to impersonate the brand from openly available sources on the internet.

The email is a request for the recipient to update their account information. This could be anything from usernames, passwords, names, addresses, phone numbers, and email addresses. It also suggests there might be a new card that needs to be activated, prompting the user to enter their AMEX card details such as the last 4 digits of the card number.
Step 2: Google Forms
Many users don’t look at the specific URL when clicking through to an online destination. However, cybercriminals look to common and trusted platforms by users, so the use of Google Forms becomes a successful vector for getting users to fall victim.
Here’s a glimpse of what you should look out for:
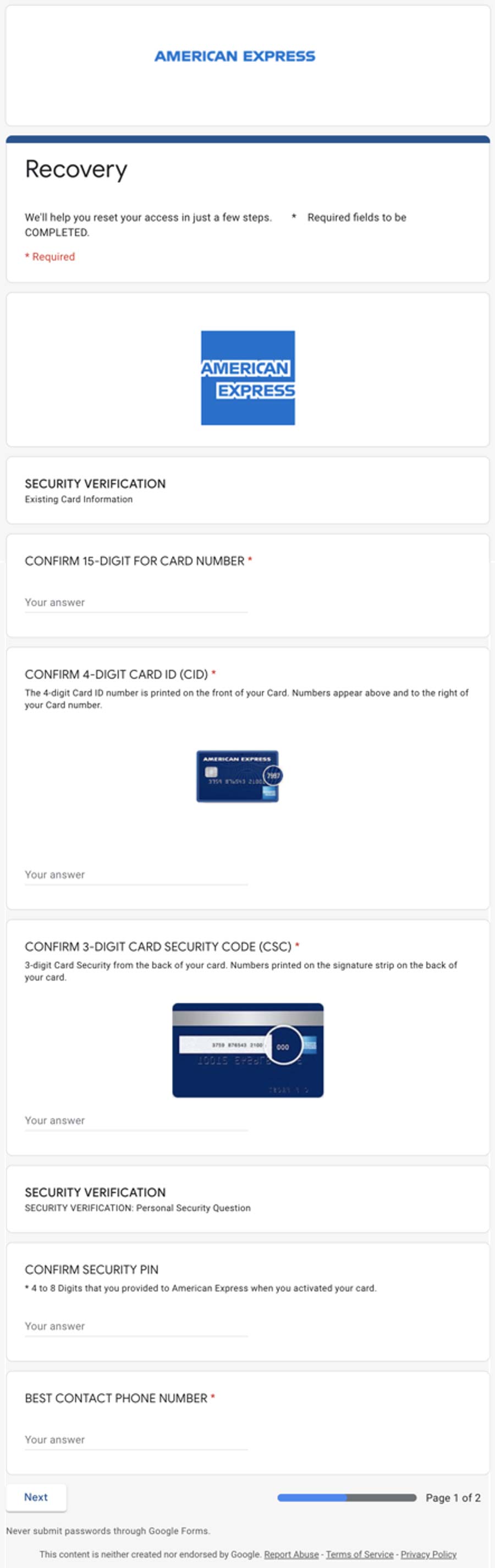
The form will start out by asking for the user’s credit card information and phone number. It will ask for the 15-digit card number, the four digits to the CID, and the security code. It’s that simple. Fearfully enough, it will also ask for the best phone number they can contact the user with. All of these fields serve as validation and are required for the attacker to complete fraudulent charges on the credit card.
What’s at Stake?
Once sensitive information such as credit card details are available to cybercriminals, they can begin to commit fraud. Plus, not only is that one card or account exposed, but any other associated account using the same username and password. Organizations must help employees especially those who have access to corporate credit card or account information understand the risks involved and how to manage this risk when it comes to email and making transactions.
PII (Personal Identifiable Information)
PII is the most valuable information that users must keep secure. It’s important to remind employees and anyone having access to your financial accounts and cards to never give out that information unless they are certain it is for an approved purpose. Examples of PII include:
- Driver’s License
- Social Security Number
- Passports
- Bank Account Numbers
- Phone Numbers
- Emails
Once a cybercriminal gets a hold of these pieces of information, it automatically becomes compromised.
What’s Next?
Now that phishing attacks have become more sophisticated, with cybercriminals developing tactics to bypass traditional email security solutions, users are quickly falling victim to these attacks. In fact, research conducted by GreatHorn.com found that 33.9% of professionals working white-collar jobs have reported credential thefts via email security tools.
Organizations today require a more robust cloud-based email security solution that can detect and assess all areas of risk associated with email. This includes a solution that uses authentication measures such as DMARC, DKIM, and SPF. Understanding historic communication patterns and being able to analyze URLs in the moment of risk is critical. Examining company email history broadens the context for users within your organization. It also helps to reduce warnings and when an email is flagged, the recipient on the other end is more likely to heed it.




