Phishing campaigns come in a wide variety of flavors – from volumetric voicemail scams to clever executive impersonations. While most of the phish you see in your inbox are spam-like in their delivery – focusing on volume and a small percentage of responses – we’re increasingly seeing highly targeted attacks that trigger off of some personalized fact.
In this blog, we’ll highlight how attackers are increasingly using publicly available security information to capture security-savvy employees.
That quarantine message isn’t real
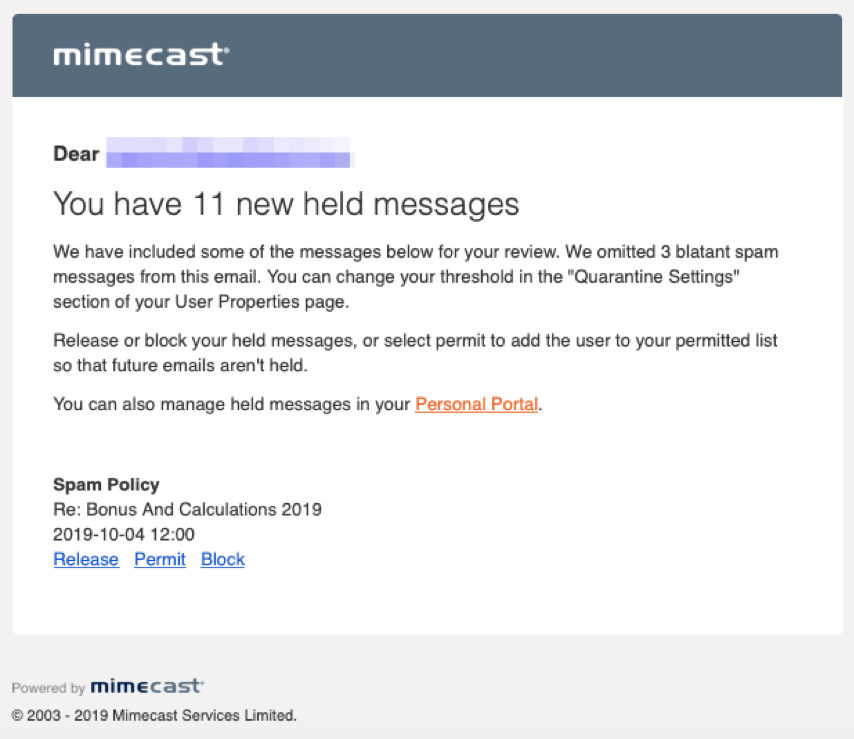
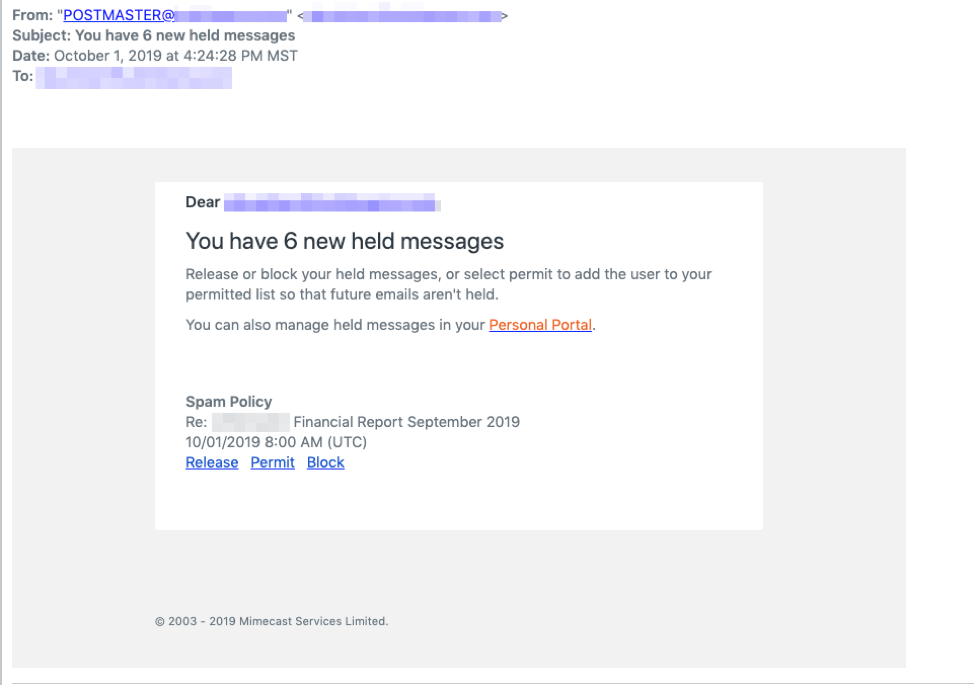
In the past six months working with prospective clients, we’ve seen a surge in fake notifications spoofing the incumbent secure email gateway (SEG) that is in-use during our pilot period. As illustrated in the below example, a hacker will leverage this information to spoof a SEG like Mimecast, Proofpoint, or Barracuda, acting as though it’s a valid notification or alert coming from the email security vendor, when in fact it turns out to be a harmful phish, most often bringing you to an Office 365 credential theft site.
Often, the emails will look extremely convincing. In the below examples, the messages sound legitimate and follow the format of a Mimecast quarantine email—one of them goes as far as to include Mimecast logos and coloring—but both of them point to credential theft sites.
How criminals find your security dirty laundry
You might wonder how criminals know which services you’re using, but in fact, it’s relatively simple.
Solutions with legacy email solutions (such as a SEG) reroute email through the gateway to inspect them before they reach their end destination (Microsoft Office 365 or Google G Suite >> User’s Inbox). Since gateways require a change in your MX record, this is effectively publishing your email platforms and security providers for public review, which poses a security risk to your organization. It’s like giving the hacker a map to where the treasure trove is located. Not surprisingly, cybercriminals are using this to benefit themselves. How?:
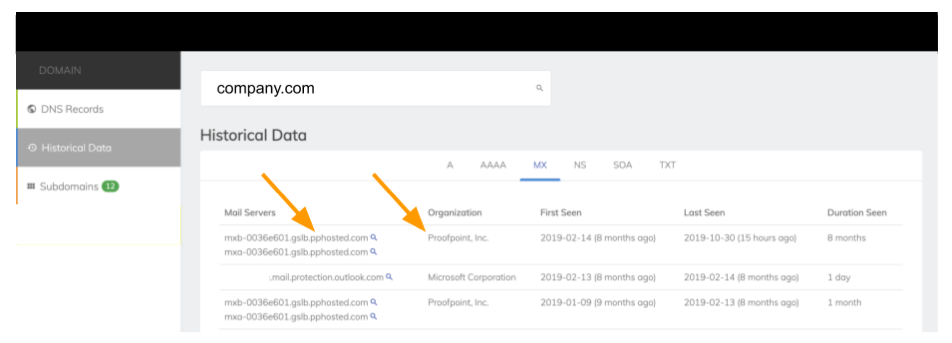
Simply visit a website like SecurityTrails or MXToolbox, and do a search on the domain of interest, e.g. company.com. The output under the MX record detail will show anyone which email platform is being used and if there are any SEGs that are rerouting MX records (there are only a small number to choose/ guess from). This information is readily available for anyone on the public internet to access in a matter of two clicks:
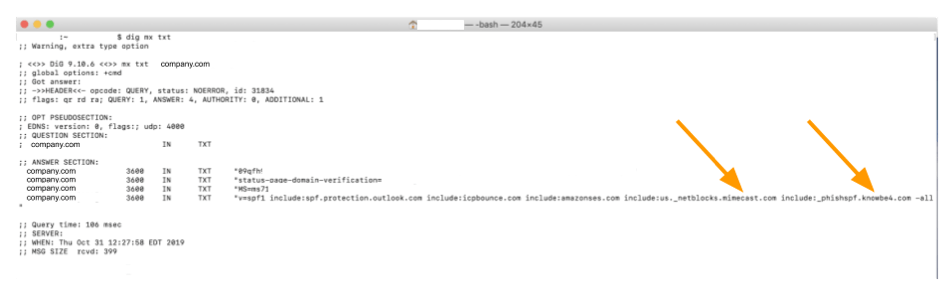
Alternatively, you can open up a Terminal Service window and execute a quick command:mx txt <domain.com>
The output will tell you (or a threat actor) a similar story:
Criminals use this information to construct attacks such as the ones highlighted above or this sophisticated scheme impersonating Barracuda. For users that have paid attention to their security awareness training, this kind of approach would be more likely to put them at their ease – leaving them vulnerable to a credential theft attack and a resulting compromised account.
Consider Another Way: The API Approach
GreatHorn leverages the API approach, rather than rerouting email via an MX records change. This modern architecture doesn’t expose any information on which email security technology is being used by an organization. Less exposure means less risk, mitigating any possible attack vector the threat actors could be considering.
Join the modern age with GreatHorn and give us a try.



