This is the first post in our new blog series, “Phishing Emails, Explained.” In this series, we’ll take a closer look at real-world phishing examples and the tactics that cybercriminals are using to lure victims into interacting.
Phishers frequently exploit global brands like Microsoft, Dropbox, and DocuSign in their scams because the brands’ good reputation lulls victims into a false sense of security. Once trust is established, it’s easier to convince people to interact with malicious links and attachments. And because the URLs for these brands are hosted on seemingly legitimate websites, they can more easily evade many common email security tools.
Below is a recent phishing email that masquerades as an important message from Microsoft.
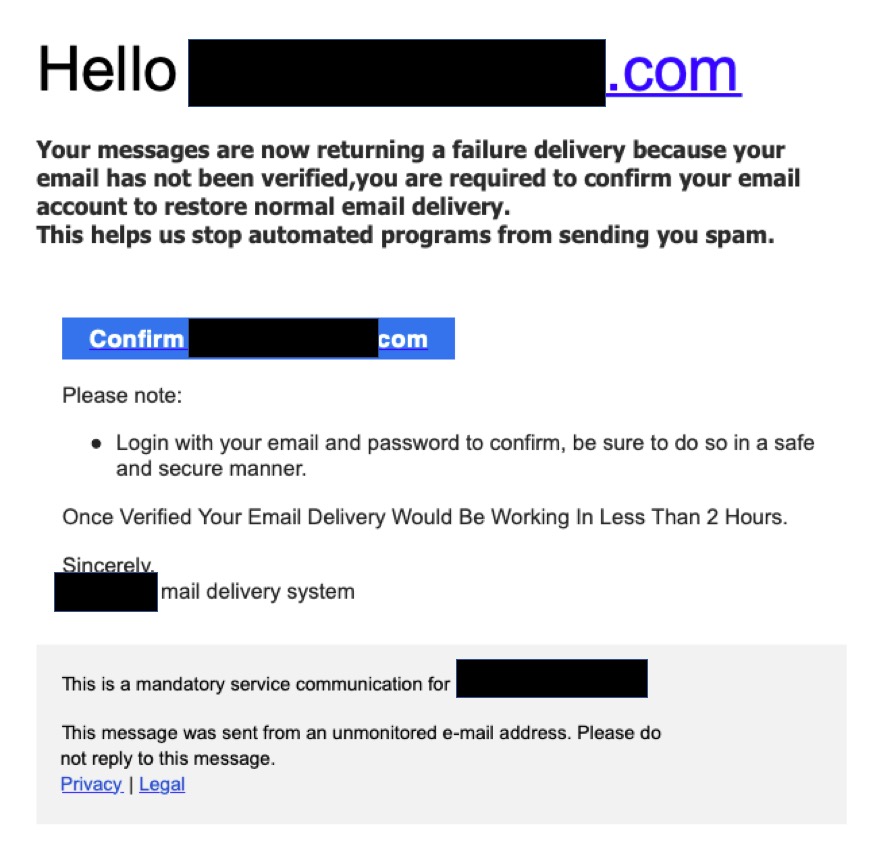
Checking the sender details of suspicious emails is one way of verifying whether they are legitimate communications or phishing attacks. This bogus email does not originate from a Microsoft email domain.
The “From” field:
“Microsoft Outlook Messaging Department”
The subject of the email:
Action Required – Mail Sync Error!
The body of the email:
“Your messages are now returning a failure delivery because your email has not been verified, you are required to confirm your email account to restore normal email delivery.
This helps us stop automated programs from sending you spam.
Please note: Login with your email and password to confirm, be sure to do so in a safe and secure manner.
Once Verified Your Email Delivery Would Be Working In Less Than 2 Hours.
Sincerely, mail delivery system”
The call to action! (in a Microsoft blue CTA box):
“CONFIRM (recipient’s email)”
The goal:
Attackers are attempting to steal credentials by convincing users that their mail service is not working.
No matter the tactics used, all phishing emails have two things in common: the false sense of a trusted sender (or entity) and a clear sense of urgency or action needed! Although not a new tactic, this “Mail Sync Error” example is a fairly convincing phishing email. The broad attack consists of a deceptively simple, yet branded HTML email message, telling the recipient that his/her email account ‘has not been verified.’ Recipients are encouraged to click the ‘Confirm email address’ link to re-sync with the mail server to continue receiving email messages.
If the recipient clicks on this link, they are taken to a convincing replica of a fake website, simulating a Microsoft Office 365 portal. The URL contained in this message redirects to website with a compelling version of a Microsoft login page, including the recipient’s pre-populated email. Although the design of the log-in page looks legitimate, this is a fake website used by cybercriminals to collect login data from unsuspecting victims.
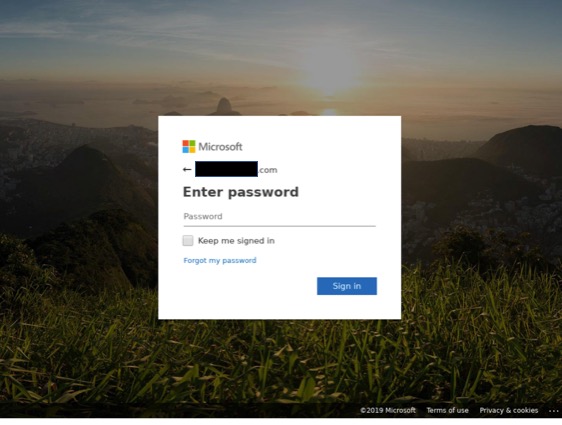
Because of the massive number of users, Microsoft Office 365 is a regular victim of these types of credential scams. Attackers typically spoof the display name and couple that with the use of a freemail service such as gmail.com, outlook.com, etc., which almost guarantees no SPF, DKIM, or DMARC issues. In the past year, there’s been an explosion of Microsoft spoofing attacks. Credential theft attacks are amongst the most dangerous because the effects/damage are not necessarily felt right away.
Phishing continues to be one of the most predominant forms of cybercrime. Recent GreatHorn research shows that there’s been a 25% increase in the number of email threats making their way to inboxes on a weekly basis and 22% of organizations have experienced a data breach due to an email-borne attack in the last three months. The FBI stats on phishing are clear. Phishing attacks can be enormously costly (in the billions of dollars) and destructive, and new scams are appearing every week.
GreatHorn recently announced new capabilities to proactively identify and block Office 365 credential theft attempts using computer vision. If you would like to learn more, please read our press release or blog.





