U.S. taxpayers will again get a reprieve on their April 15 tax filing deadline, this year. If historical trends are any indication, there will be no let-up on the pressure that cybercriminals put on email users each year at tax time.
As if the demands of tax season weren’t enough, at this time of year IT professionals have to be on high alert for attacks targeting their employees, clients and companies. In these attacks, in particular, funds and highly sensitive personal information are at elevated risk, due inherently to the subject matter.
Last year, when the COVID-19 pandemic emerged, with Tax Day 2020 already in view, the tax filing deadline extension came on March 17, 2020. On that date, the U.S. government issued its first announcement, extending the deadline for tax returns to May 17. Just a few days later, on March 21, the tax return deadline was extended again, to July 15.
Email scammers took advantage
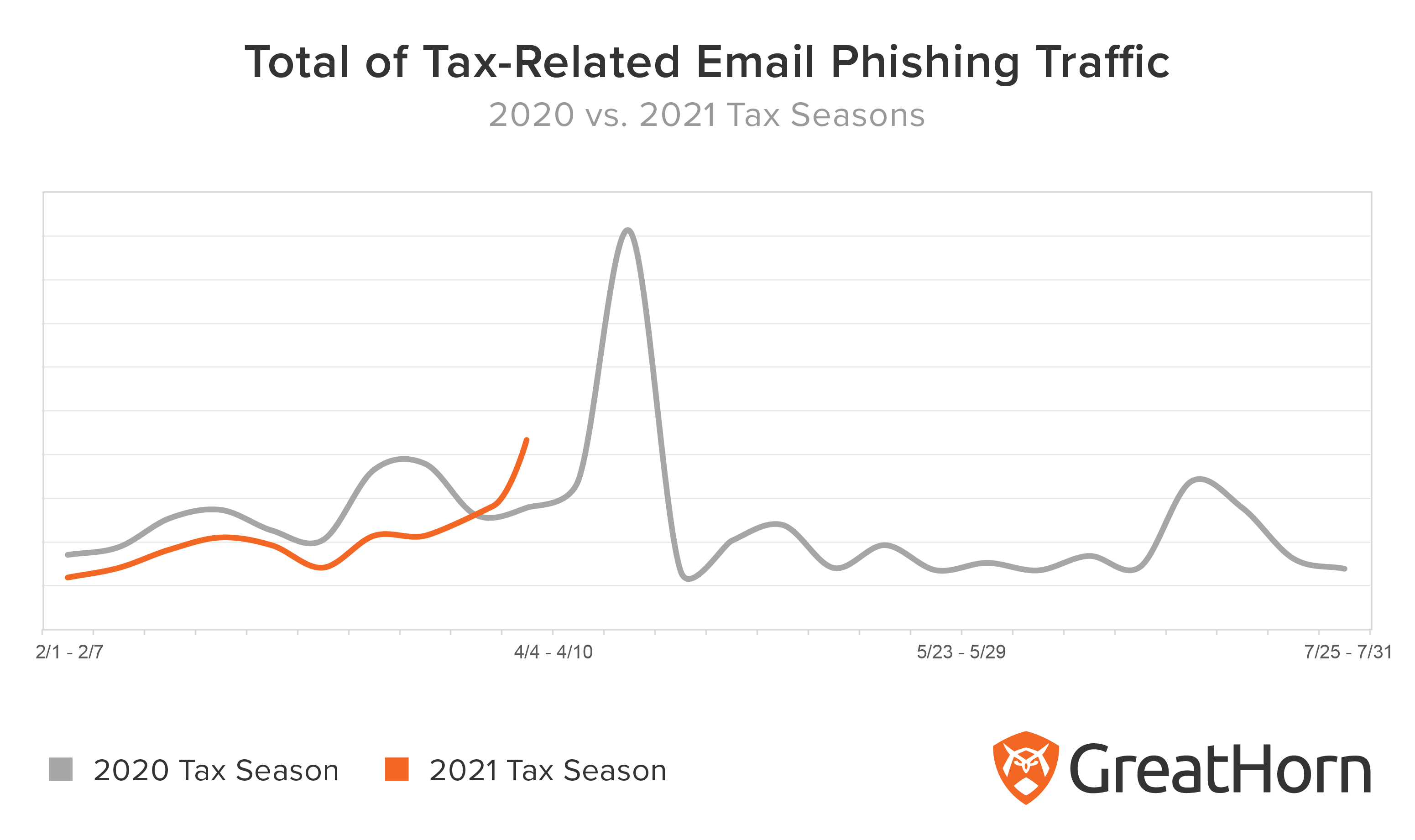
The GreatHorn Threat Intelligence Team logged a 78 percent increase in the quantity of email phishing campaigns, following the deadline extension announcements.
Many cybercriminals proceeded as planned with email phishing campaigns, despite the announcement. The quantity of phishing emails received by organizations spiked as usual on the week of the standard deadline (April 17), increasing 167 percent, week-over-week. After the normal deadline passed, it fell back 85%.
There was a final increase in tax-related email phishing traffic during the weeks of July 4 through July 17, 2020, but that week’s email phishing activity remained 170 percent lower than the traffic the GreatHorn Threat Intelligence Team monitored in the week of the normal, April tax deadline.
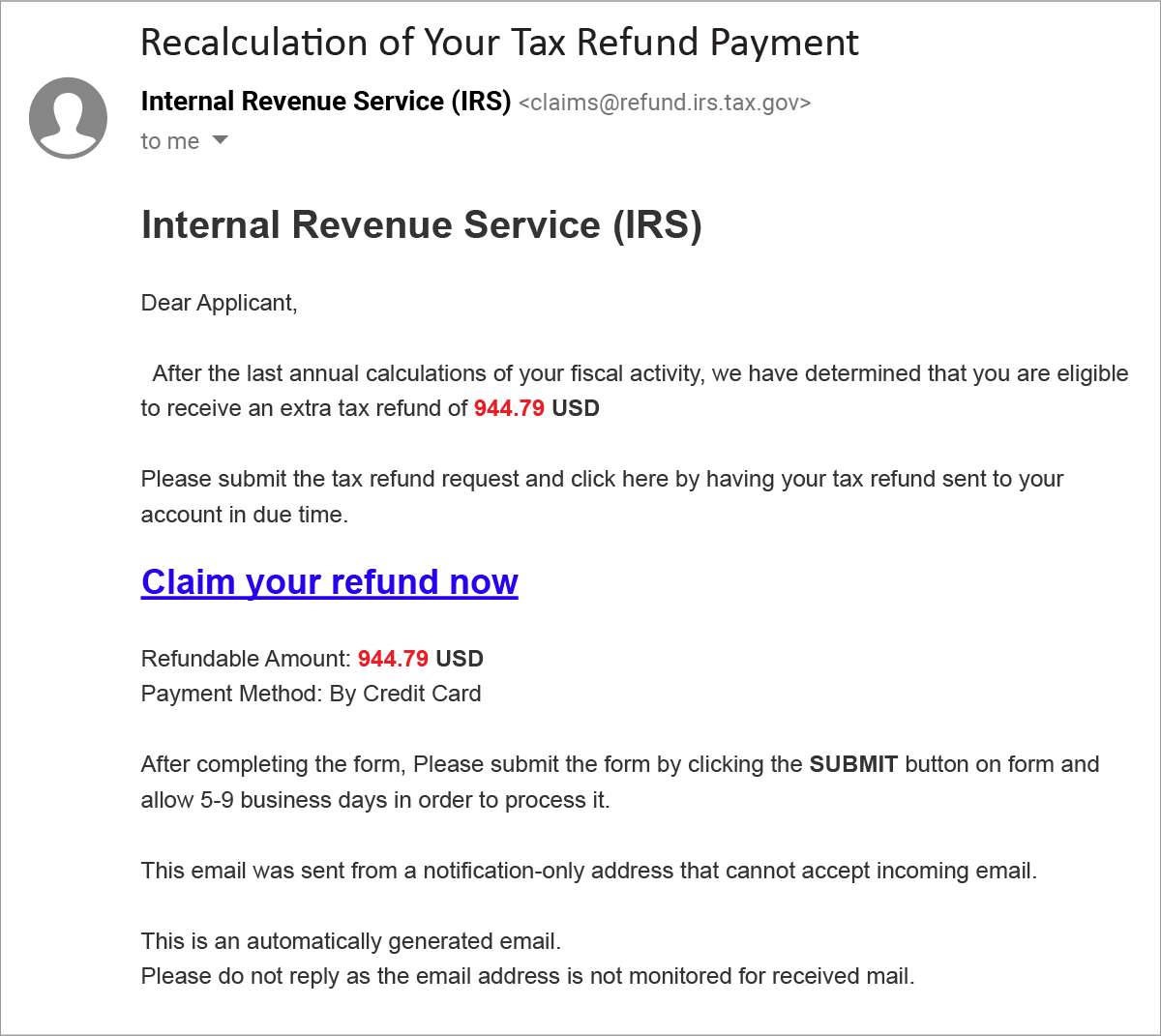
Example phishing email
Here is an example of a phishing attack identified by the GreatHorn Threat Intelligence Team. The Display Names being used in this specific phishing attempt are permutations the Internal Revenue Service including “IRS”, “IRS Help Desk”, “Internal Revenue Service” and “Internal Revenue Service (IRS).”
The tax refund noted in the email is designed to heighten the urgency by allowing users to claim their refund by Credit Card.
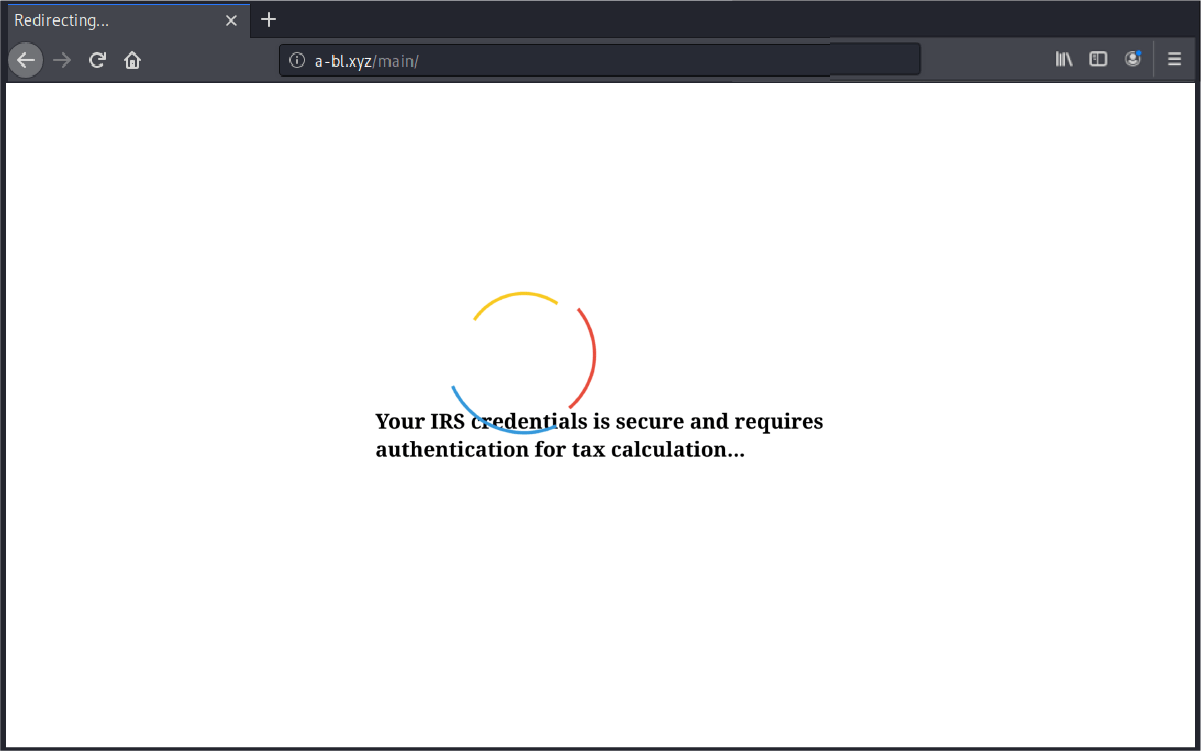
The hyperlink itself takes users to a well-designed page, where the users are informed that their IRS credentials are secure and requires authentication.
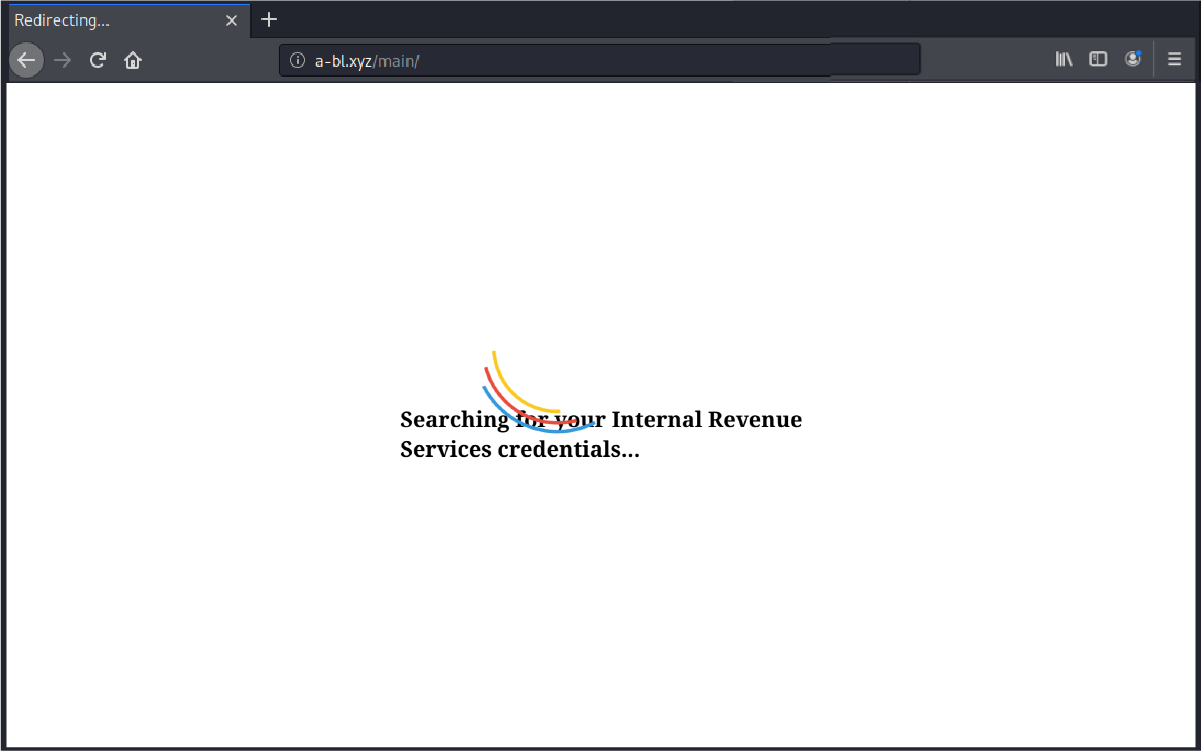
GreatHorn categorizes most these tax season email phishing attacks as External Impersonations Attacks. There are a number of ways GreatHorn can identify suspicious messages and quarantine them for easy remediation. These include the following three methods.
- Behavioral analytics: GreatHorn artificial intelligence and machine learning analyzes the patterns of normal communications, to identify anomalous emails.
- Relationship strength: The strength of a sender’s relationship to the recipient, as well as “friends of friends” is a factor in flagging suspicious emails.
- Spoofing likelihood: Analysis for employee display name spoofs, domain spoofs and domain look-alikes includes comparison against known email addresses and email authentication standards.
As we enter the height of tax season again, the GreatHorn Threat Intelligence Team warns organizations against the coming influx of phishing campaigns using tax-related terms. Some of the most prolific terms used by cybercriminals include: “IRS,” “Internal Revenue Service,” “Intuit,” “Tax Filing,” “Tax Fraud,” “Tax Refund” and “Turbo Tax.”
Based on historic trends, the GreatHorn Threat Intelligence Team expects that organizations will see a significant spike in tax-related phishing campaigns beginning this week, April 12 – April 17, 2021.





