2020 Email Security Benchmark: How Organizations Are Responding to More Frequent and Sophisticated Phishing Attacks
At GreatHorn, we have a 30,000-foot view of the email phishing threat landscape. That enables us to see hotspots like a recent spate of coronavirus-themed phishing emails hitting inboxes. That view isn’t enough to understand how phishing email attacks are evolving, and how security teams are responding to the threats to their organizations. In order to achieve that level of understanding, we need to see email phishing attacks through the eyes of the people who face them and make the decisions that can help prevent and remediate these attacks. Once a year, we survey hundreds of people in the business, spanning security, IT and the C-suite. The results are published in our annual Email Security Benchmark report.
This year, the report’s third year, we received responses from 640 individuals, reaching a diverse array of markets and a spectrum of business sizes. We asked about new threat vectors, high-impact issues and new strategies for responding to email phishing attacks. Comparing responses to data from 2019, we have a clear picture of how the industry is evolving in a chaotic time. Below, we’ll provide the following, pulled from the report: two brief takeaways about what organizations are facing in threats to email security; and a short list of the solutions that are working to safeguard data systems from email attacks.
1. Impersonations are becoming the most pervasive, and successful, form of phishing attack
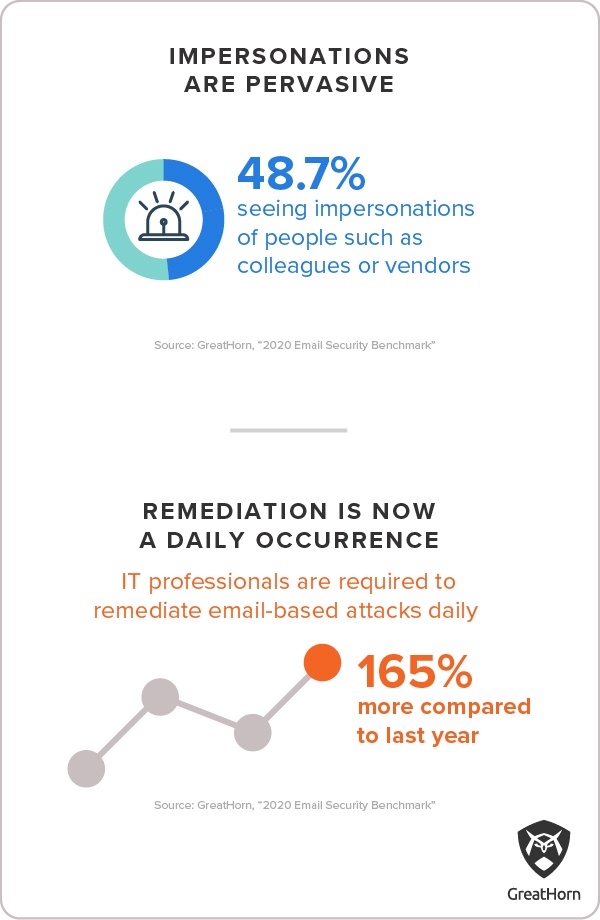
Impersonation attacks have long been on our radar at GreatHorn. In 2020, we see them on the increase. They come in two flavors: attacks that impersonate a known individual, and attacks that impersonate a known brand.
People impersonation attacks are the most common. Nearly half of respondents to our 2020 survey (48.7%) reported seeing people impersonation attacks. In these phishing attempts, attackers rely on research, using LinkedIn and other sources to learn the names of colleagues inside the organization. They can also learn the names of people who work at vendors, partners and investment firms connected to the target organization. In the 2020 benchmark survey, more than one third (35.1%) of respondents said people impersonation attacks are their top email threat.
Brand impersonations are a close runner up and are proving among the most effective types of attacks, with 42.4% reporting their organization had fallen prey to a successful phishing attack that used brand impersonation to infiltrate. That’s up from 22.4% in 2019. Like people impersonations, phishing attacks that employ brand impersonations rely on attacker research to identify the business names and domains that will be familiar to users inside your organization. These phishing attacks often employ fake URLs that look a lot like the known brand.
2. Phishing threat remediation is increasingly becoming a daily task for security teams
The threats described above are coming fast and furious, to the point where SOC teams find their normal resources and operations procedures strained by new volume and aggressiveness in phishing email threats.
More than a third of respondents (35.8%) now report they are seeing email threats incoming every day. The number of respondents reporting this kind of activity on a daily basis is up from 24.3% in 2019. Moreover, a third of respondents (33.6%) say they need to take some kind of action every day, to remediate these threats. Email threat remediation responses include running PowerShell strips, suspending compromised email accounts, resetting compromised application accounts and taking legal action. That’s more than double the number of respondents (12.7%) who reported in 2019 that the threats facing their organization required daily remediation. The volume of threats and their seriousness have both increased in the past year, putting new strain on IT departments and security teams.
Two solutions to increased sophistication and volume of email phishing threats
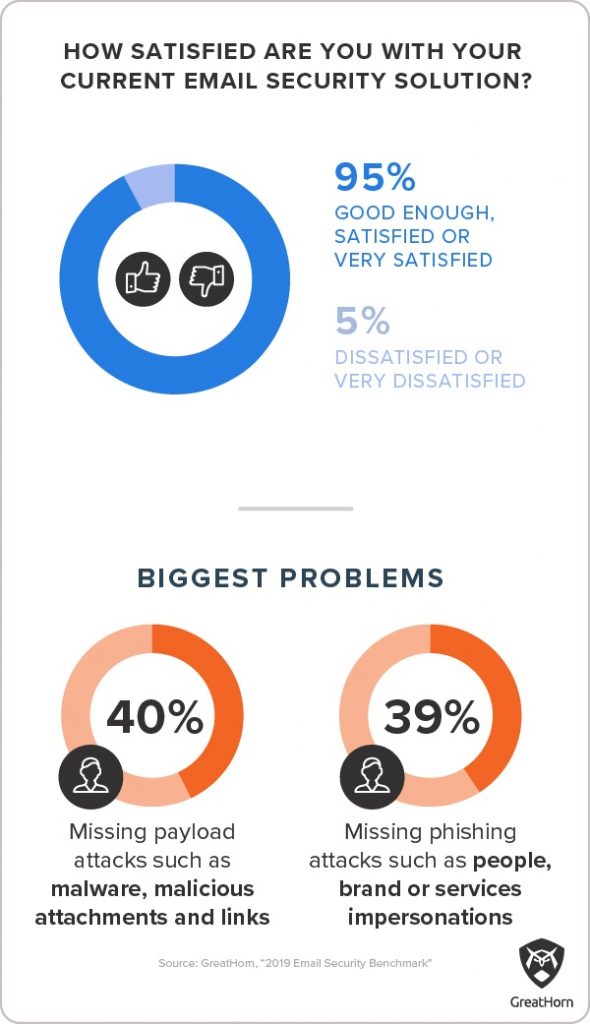
One salient fact that emerged from the 2020 survey is that IT professionals have become numb to the deluge of email threats. Despite one third of respondents reporting that the inbound threat volume is requiring a daily pace of action to remediate successful phishing attacks, 95% of respondents from the same pool told us that they’d rate their current email security solution “good enough”, “satisfied” or “very satisfied.” However, some are taking steps to change the status quo.
Solution # 1: Automation
Threats make use of impersonation and specific targeting based on attacker research; it’s all too easy for attackers to spin up new servers, register fake domains and bring the same attack from multiple different directions. In a nutshell, email phishing attacks in 2020 are too sophisticated, voluminous and varied for “known-bad” rules to possibly keep up. The threats also come too fast and thick for ad hoc responses. Even IT departments writing scripts to automate responses to specific threats are finding themselves overwhelmed. Successful security teams are taking a step beyond scripts, deploying automated solutions that can calculate the risk an email poses, based on its content and metadata, and set up appropriate defenses without involving IT staff.
Solution #2: Education
Automation can relieve the burden on security teams, but it can’t do so by filtering all suspicious email. Unfortunately, many organizations seem to be moving in that direction. Nearly half (48.3%) of respondents to our 2020 survey said that at least once in the past week they had to go into their junk or spam folder to retrieve legitimate email. When filters catch too many false positives, they are ineffective. In 2019, only 30.7% said they’d had to do this in the same timespan.
Instead of filtering out suspicious emails, many can go through to the user with information about the level of risk they represent. Informing users about real threats in real time and equipping them is a path organizations are using to prevent phishing attacks from hitting their mark, at the user level. It’s allowing organizations to pivot from detection to response much more nimbly, across the entire organization.
Conclusion

The email security threat landscape has evolved, bringing with it an overwhelming volume of attacks that have increased in their variety and sophistication. In this environment, the organizations that are keeping up with the rising tide of threat are deploying solutions that put all their resources to work–from automated detection to real-time education that enablers their users to turn from a vulnerable population to their best line of defense against email phishing attacks.





