What are cryptocurrencies?
Cryptocurrencies move over decentralized networks, with each computer (or “node”) that plugs into the network acting to validate transactions. That gives them the ability to facilitate transfers of money without a bank or money transmitter in between to say who gets to use the network, and who doesn’t.
In this way, cryptocurrencies are like digital cash: transactions clear almost instantly, and there’s no need for one party to trust that the other is good for the funds.
Contrary to popular belief, most cryptocurrencies aren’t untraceable. Each transaction leaves a digital trail, which allows the network to confirm its validity. Law enforcement officials have become adept at following those trails. The challenge can come in tying transactions to real-world entities at either end. If you pay an extortionist in cryptocurrency, police may know where your money is, but they may not know who controls it.
Cryptocurrencies have become the favored currency of extortionists. Unlike cash, they’re not completely anonymous. But they’re much less traceable than a bank account. And, being digital, they’re a heck of a lot more convenient than a brown paper bag filled with banknotes.
Using cryptocurrency in an extortion attempt gives a criminal a chance to grab the money and run, at a distance, digitally, with no bank in the middle to stop the payment or alert the authorities. As such, it presents an attractive tool for criminals looking to exploit individuals and organizations. This is especially true when extortion is done via email phishing attacks.
The GreatHorn Threat Intelligence Team has studied extortion emails and emails related to cryptocurrencies. Out of all extortion emails sent by cybercriminals, 98.7% ask for payment in Bitcoin, the largest cryptocurrency. Looking at the problem from the other side, of all the phishing attempts sent by cybercriminals that mention Bitcoin, 18% are extortion attempts.
One of the problems these criminals face is converting ill-gotten cryptocurrency into cash. Bitcoin is the oldest of the modern generation of cryptocurrencies. It has the most users, the highest value and the largest number of trading venues and services supporting it. Bitcoin may be more traceable than other, privacy-oriented cryptocurrencies, but it is far easier to buy and sell. That’s why cybercriminals so frequently ask for payment in bitcoin.
Cybercriminals also know bitcoin is the best-known cryptocurrency among their intended victims. Interestingly, the GreatHorn Threat Intelligence team found a high correlation between the frequency of cryptocurrency-related phishing attacks and the volume of Google searches related to cryptocurrency.
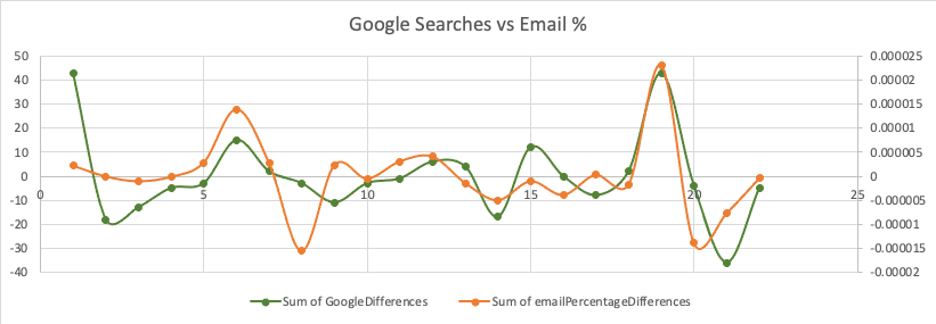
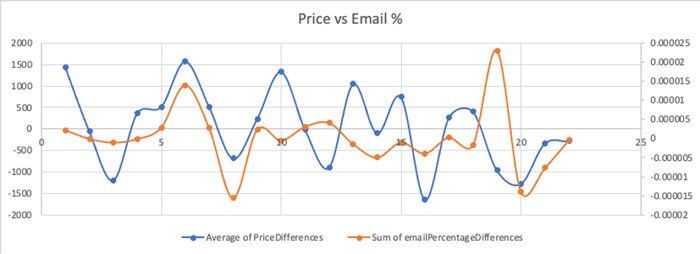
However, this does not impact the trading prices of cryptocurrency.
Often in extortion attempts, cybercriminals have already completed some reconnaissance and may have even tracked a users’ behavior. Even if they haven’t, and their messages are way off the mark, the shock and fear a recipient feels when opening a so-called “sextortion” email can be enough to elicit the criminals’ intended reaction. (Read more on the social psychology used by cybercriminals, here.)
Here are two examples of extortion emails intercepted by the GreatHorn Threat Intelligence Team. Personally, identifiable information has been altered or removed.
Example extortion email 1

Example extortion email 2

As you might guess, these kinds of emails can be terribly effective, even if the cybercriminals sending the email know little about the recipient and are bluffing about their access to systems and sensitive material.
To find out more about how GreatHorn’s advanced cloud email security solution protects your employees and your organization against phishing attacks, click here.





