GreatHorn Blogs
Featured

Most Popular
More Blogs
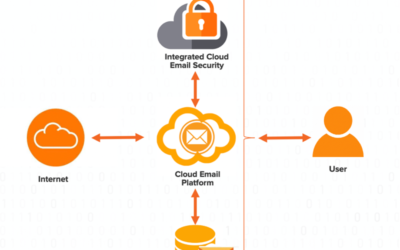
Native vs SEG vs ICES: What You Need to Know About Email Security
The shift from on-premise email platforms to cloud email platforms has taken shape, with the...
Blueberry Muffins vs Blonde Chihuahuas: Debunking Artificial Intelligence in Email Security
In cybersecurity, buzzwords come and go, often being replaced with new buzzwords while the market...
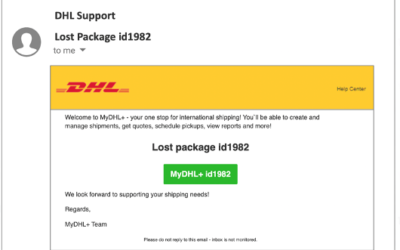
Global Supply Chain: Attackers Targeting Business Deliveries
Our global supply chain includes all the people, companies and countries that need to work...
Google and Open Redirects: Preventing Your Users from Becoming a Victim of Attacks
The GreatHorn Intelligence Team has identified an increase of 84% in phishing attacks leveraging...
Supply Chain Attacks: How to Defend Against Vendor Email Compromise
The GreatHorn Threat Intelligence Team, alongside hundreds of responses from IT security...
Bitcoin and Cryptocurrency: 2021 Email Extortion Trends
What are cryptocurrencies?Cryptocurrencies move over decentralized networks, with each computer...